A Steganography-Based Optical Image Encryption System Using RGB Channel Integration
Cheng-Hung Chuang
1.Introduction
With the rapid development of communication technology,it is easy to acquire multimedia data everywhere.Unfortunately,the problem of illegal data access or interception occurs frequently and universally.Therefore,it is important to protect the content and the authorized use of multimedia data against the illegal users.Data encryption is a strategy to make the data unreadable,invisible or incomprehensible during transmission by scrambling the content of data[1].In an image encryption system,it uses some reliable encryption algorithms or secret keys to transform or encrypt secret images into ciphered images.Only the authorized users can decrypt secret images from the ciphered images.The ciphered images are meaningless and non-recognizable for any unauthorized users who intercept ciphered images without knowing the decryption algorithms or the secret keys.
Dissimilarly,steganographic techniques refer to methods of embedding secret data into cover data in such a way that people cannot be aware of the existence of the hidden data.The image steganographic methods(or called virtual image cryptosystems)[2]-[5]are proposed to hide the secret images into cover images which are readable but non-critical.They are designed to reduce the notice of illegal users.Common methods for data hiding can be categorized into spatial and transform domain methods.One of the common spatial domain methods,which have high embedding capacity,embeds data into least significant bits(LSBs)of image pixels.Contrarily,in the transform domain,e.g.the discrete cosine transform(DCT),Fourier transform,or wavelets,transformed coefficients of cover images can be manipulated to hide secret data.
For high speed applications,image encryption methods based on optical theories have been developed.Many optical image encryption algorithms have been proposed for transmission security[6]-[11].The double random phase encoding technique[6]was a famous and widely used algorithm which employs two random phase masks in the input plane and the Fourier plane to encrypt images into stationary white noise.In [7],an optical image encryption system based on the double random phase encryption and a public-key type of data embedded technique was proposed.The data hiding scheme proposed in [7]always embeded data in a fixed area of the encrypted image.Although it is a simple way to achieve the data embedding and extraction,the visual quality of the decrypted images is lower when the hidden data size is large.In [8],the optical encryption was performed using the fractional Fourier transform.In [9],an adaptive steganographic method was presented to improve the security and visual quality in the optical image encryption system proposed in [7].However,the input images are limited to the grayscale in those encryption systems.In [10],the encryption method using wavelength multiplexing and lensless Fresnel transform hologram was proposed for the applications of color images.In [11],the optical color image encryption scheme was performed in the fractional Fourier transform domain.In [12],the optical image encryption system based on the adaptive steganographic method[9]was extended to color images.In the proposed system,a color image was separated into three channels,i.e.red,green,and blue,and each channel was encrypted individually.
In this paper,an adaptive steganography-based optical color image encryption system using RGB channel integration is presented.The RGB channel in a color image is first integrated into one large grayscale image.The integrated image is encrypted by two random phase masks.Then secret data is embedded into the LSBs of the quantized encrypted image data using the zero-LSB sorting technique.In our experiment,a comparison of steganography methods in the optical image encryption system is performed.Experimental results show that the proposed method obtains a good performance in both hiding capacity and decrypted image quality.
2.Review of Optical Image Encryption System
In optical image encryption systems,the double random phase encoding technique[6]is a famous and common method.In the encoding process,an image I is multiplied by a random phase mask P1in the input spatial plane and Fourier transformed to the frequency domain.It is multiplied by another random phase mask P2in the Fourier plane.Then it is inverse Fourier transformed to obtain its encrypted image IEin the output spatial plane.In the decoding process,the encrypted image IEis Fourier transformed and then multiplied by the conjugate of mask P2and inverse Fourier transformed to the spatial domain.It is multiplied by the conjugate of mask P1to obtain its decrypted image IDin the output spatial plane.The equations are expressed as follows:

where p1and p2are random numbers of the image size between [0,1],F and F-1define the Fourier and inverse Fourier transforms,and * denotes the conjugate operation.The optical 4f architecture of the image encryption system is shown in Fig.1,where f is the focal length of the lens.
For a steganography-based optical color image encryption system,it is first separated into three channels:red,green,and blue.The three channel images are individually coded by the double random phase algorithm,i.e.multiplied by random phase masks P1R,P1G,P1B,and P2R,P2G,P2B.Then the secret data is embedded into the three encrypted channel images by using the LSB replacement technique.That is,the encrypted cover signal should be quantized into bit data first.Then the secret data is embedded into LSBs of the quantized bit data.Next,the quantized bit data must be de-quantized to recover the encrypted stego image.Afterward,the encrypted stego image can be transmitted to the receiver.In the receiver side,one can extract the secret data and decrypt the cover image from the encrypted stego image.Fig.2 shows the block diagram of the optical color image encryption system.
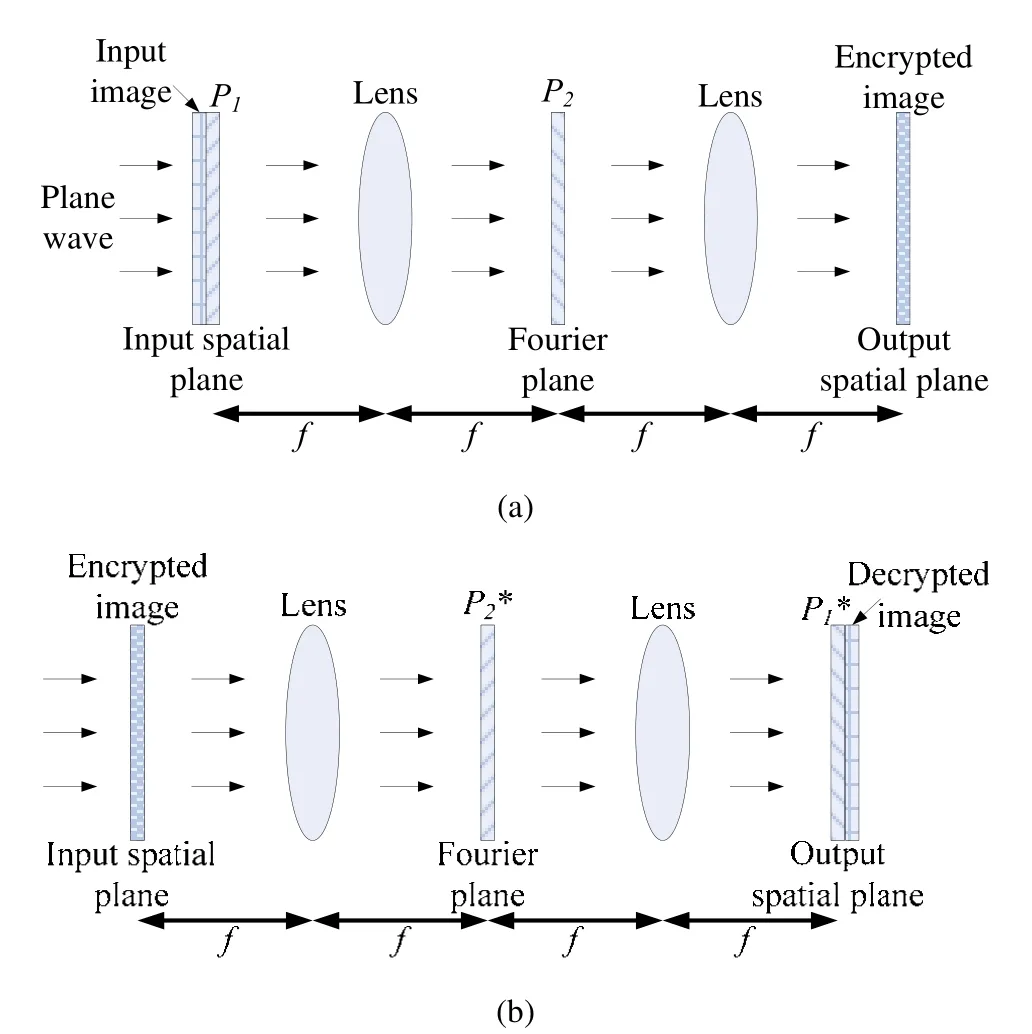
Fig.1.Optical 4f architecture of the image encryption syste:(a)encryption architecture and(b)decryption architecture.

Fig.2.Block diagram of the optical color image encryption system:(a)encryption process and(b)decryption process(X:multiplication operation; E and E–1:data embedding and extraction processes).
3.Proposed Method
From the above description,the quantization and LSB replacement will cause the loss in image quality.The important issue is how to select the hidden regions or positions that result in low distortion of the decrypted image.It is a simple way to hide the data in fixed positions of the encrypted image.Nevertheless,due to the different image contents,the fixed positions are not always suitable for hiding data.Those positions with smaller absolute values are preferable to hide secret data since they have smaller energy and quantization step size.Therefore,an adaptive steganographic method is applied to choose positions with smaller absolute values.However,for a color image with RGB channel separation,the hidden position selection is restricted to individual channel images.To improve the visual quality of the decrypted image,the RGB channel integration is proposed.
In the proposed method,it is first integrated three channels into one grayscale image.The integrated image is encoded by the double random phase algorithm,i.e.multiplied by random phase masks Psand Pf,where Psand Pfare of the triple image size.Then the adaptive steganographic method is applied to the encrypted integrated image to find those positions that are suitable for hiding data overall.Fig.3 shows the illustration of three different types of data hiding strategies.There are 16×3 bits secret data hidden in the encrypted color image signal.The first class is the fixed-position type(Type I)which embeds data in the central square area in each encrypted channel image.The second class is the RGB-channel-separation type(Type II)which hides data in those positions that are selected by the adaptive steganographic method in each encrypted channel image.The last class is the RGB-channel-integration type(Type III)which conceals data in those positions that are chosen by the adaptive steganographic method across three encrypted channel images.

Fig.3.Illustration of three different types of data hiding strategies:(a)Type I:fixed position,(b)Type II:RGB channel separation,and(c)Type III:RGB channel integration(gray blocks mean those positions selected to hide data).
Assume that there are N bits in the secret data,i.e.B={b1,b2,…,bN}.Since the transformation coefficients in the encrypted image are complex numbers,the real and imaginary parts can be selected to embed secret data.In this paper,the real part is chosen to hide data.The detailed data embedding and extraction procedures are described as follows.
3.1 Data Embedding Procedure
Step 1:the values of real part α in the encrypted integrated image are sorted in ascending order according to their absolute values.The set of the first N+2 numbers except the maximum and the minimum is chosen and defined as Γ={α1,α2,…,αN},where |αi|≤ |αi+1| and αi,αi+1∈Γ.Note that the maximum and the minimum in the first N+2 numbers are not used to quantize and hide data,since the quantization step size is computed from them.
Step 2:the set Γ is quantized to be ΓQ= QL(Γ )= {α1,α2,…,αN},where QL(Γ )denotes a quantizer with L levels.

Step 4:the sequence S ={s1,s2,…,sN} generated by the set ΓQZS,where si∈{1,2,…,N} and i = 1,2,…,N,is used to be the data hiding index.That is,the secret data B is successively embedded into the LSBs of the set ΓQwith the sequence S,namely ΓQS={αqs1,αqs2,…,αqsN},where αqsi∈ΓQ.The embedding rule is defined as

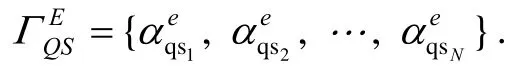
3.2 Data Extraction Procedure
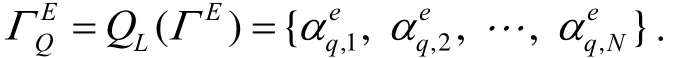

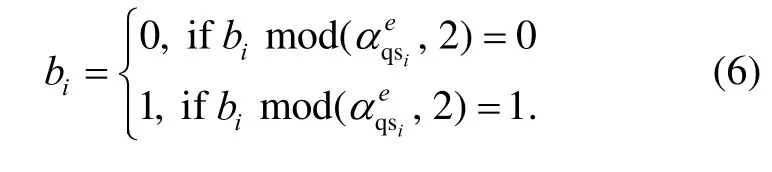
4.Experimental Results
In our simulation and experiment,one hundred 24-bit color images are collected for examination[13]–[15].All of test images are set to 512×512 pixels.The peak signal-to-noise ratio(PSNR)is applied to evaluate the visual quality of the decrypted color images.The equation is defined as follows.
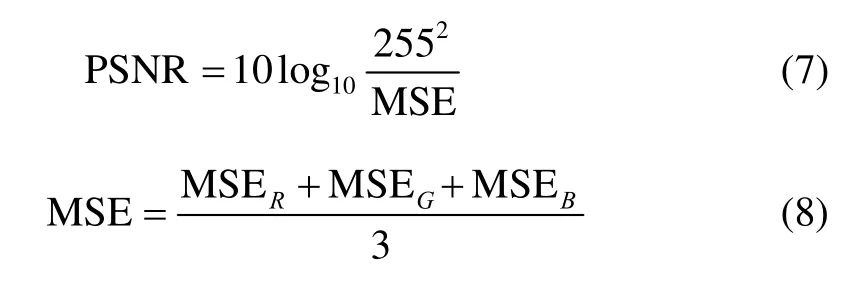
where MSER,MSEG,and MSEBare mean square errors in three channel images,respectively.
Three different types of data embedding algorithms are performed for comparison.For a fair evaluation,the size of hidden data is fixed and set to 196608 bits.That is,the size of secret data is 65536 bits in each channel image in Type I and Type II methods.Table 1 shows the maximal,minimal,and mean PSNR values(in dB)of the decrypted images of test images with different quantization levels(QL=8,16,32,64,128,and 256),i.e.,with a range of 3-bit to 8-bit quantization.With 3-bit quantization(QL=8),the image qualities achieved by Type I,Type II,and Type III methods are 16.08 dB,38.56 dB,and 43.31 dB in average,respectively.It is obvious that there is a significant increase in the PSNR values from 16.08 dB of the Type I method to 43.31 dB of Type III method in average.The methods of Type II and Type III give rise to increases of 22 dB and 27 dB in the PSNR values,respectively.
Fig.4 shows the inferior and superior examples with in the 100 cases.The original,encrypted stego,and decrypted images of No.58 and No.80 with 3-bit quantization(QL=8)are shown.The PSNR values are 11.91 dB,19.59 dB,34.13 dB,42.10 dB,38.93 dB,and 46.85 dB in Fig.4(e),(f),(g),(h),(i),and(j),respectively.It is apparent that noise exists in Fig.4(e)and(f).And it is hard to identify the difference between the decrypted images of Type II and Type III methods and the original images.Fig.5 shows the PSNR plot of the decrypted images for the 100 test images with 3-bit quantization(QL=8),where the solid,dashed,and dotted lines are the results using the methods of Type III,Type II,and Type I,respectively.In Fig.5,the average PSNR values are 43.31 dB,38.56 dB,and 16.08 dB from top to bottom curves.
To evaluate the visual quality of the decrypted images versus the data hiding capacity,the encrypted images are embedded with different size of data ranged from 108 bits to 750000 bits for test images.The quantization level is set to 8,i.e.3-bit quantization.The average PSNR value of the decrypted images is calculated for the distortion evaluation.Fig.6 shows the average PSNR for different values of data hiding capacity for test images by three data hiding methods,where the solid,dashed,and dotted lines are the results using Type III,Type II,and Type I methods,respectively.When the hidden data size is more than 30000 bits,the average PSNR value is less than 25 dB using Type I method.In the results of the Type III method,it is about 68 dB when the hidden data size is 30000 bits.If the PSNR value is set to 25 dB in the results of the Type III method,the hidden data size can be reached about 668190 bits that is 22 times the data size of the Type I method.It is demonstrated that the proposed steganography-based optical color image encryption system has a better performance than the other two methods.
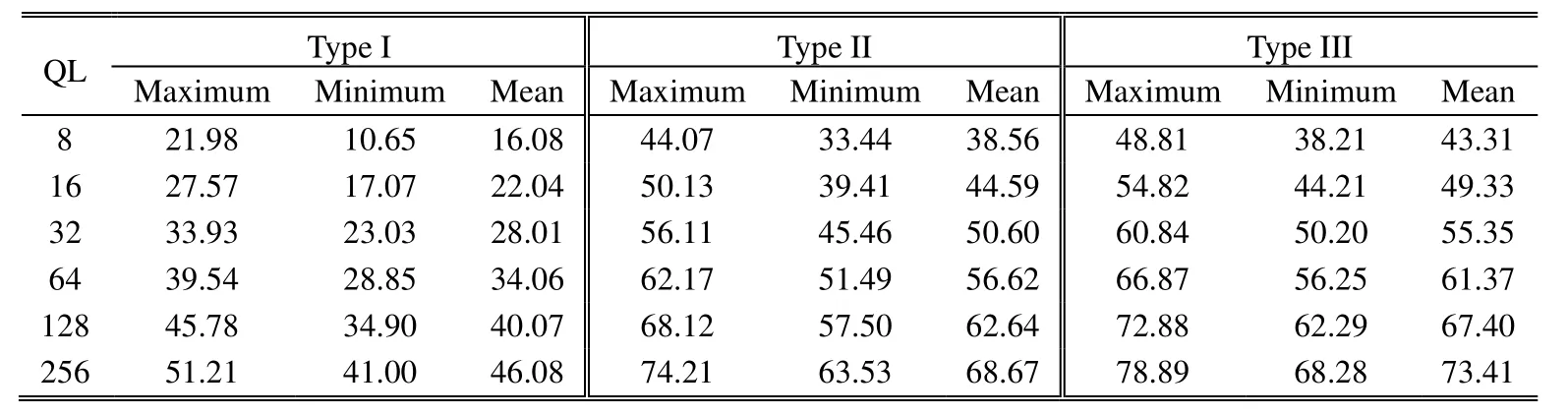
Table 1:PSNR(in dB)evaluation of the decrypted images with different quantization levels(QL)for three different methods
5.Conclusions
In this paper,the optical color image encryption system based on the RGB channel integration steganography is presented.The double random phase encoding algorithm and the adaptive data embedding technique are applied in the proposed system.The color images are encrypted by the double random phase encoding algorithm.Then the secret data can be embedded into the encrypted signal by the adaptive data hiding method with the strategy of RGB channel integration.In comparison with the conventional techniques,a higher data embedding capacity and better visual quality of the decrypted image are performed.It is verified that the proposed image encryption system provides data hiding characteristics of content-dependence,low distortion,and security.

Fig.4.Sampling of the experimental images(QL=8):(a)and(b)original images of No.58 and 80,(c)and(d)the encrypted stego images,(e)and(f)the decrypted images of the Type I method(PSNR=11.91 and 19.59 dB),(g)and(h)the decrypted images of the Type II method(PSNR=34.13 dB and 42.10 dB),and(i)and(j)the decrypted images of the Type III method(PSNR=38.93 dB and 46.85 dB).

Fig.5.PSNR plot of the decrypted images for test images(QL=8).The solid(top),dashed(median),and dotted(bottom)lines are the results using Type III,Type II,and Type I methods,respectively.
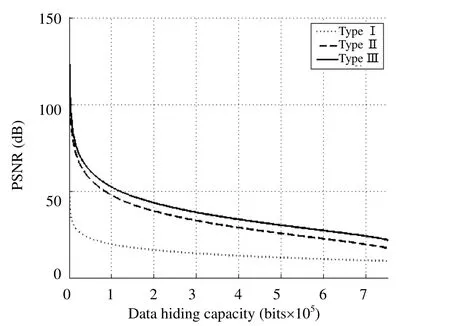
Fig.6.Distortion performance of three different methods versu data hiding capacity for test images(QL=8).
[1]M.Yang,N.Bourbakis,and S.Li,“Data-image-video encryption,” IEEE Potentials,vol.23,no.3,pp.28–34,2004.
[2]T.-S.Chen,C.-C.Chang,and M.-S.Hwang,“A virtual image cryptosystem based on vector quantization,” IEEE Trans.on Image Processing,vol.7,no.10,pp.1485–1488,1998.
[3]Y.-C.Hu,“High-capacity image hiding scheme based on vector quantization,” Pattern Recognition,vol.39,no.9,pp.1715–1724,2006.
[4]C.-C.Chang,C.-Y.Lin,and Y.-Z.Wang,“New image steganographic methods using run-length approach,”Information Sciences,vol.176,no.22,pp.3393–3408,2006.
[5]W.-Y.Chen,“Color image steganography scheme using set partitioning in hierarchical trees coding,digital Fourier transform and adaptive phase modulation,” Applied Mathematics and Computation,vol.185,no.1,pp.432–448,2007.
[6]P.Refregier and B.Javidi,“Optical image encryption based on input plane and Fourier plane random encoding,” Optics Letters,vol.20,no.7,pp.767–769,1995.
[7]G.-S.Lin,H.-T.Chang,W.-N.Lie,and C.-H.Chuang,“A public-key-based optical image cryptosystem based on data embedding techniques,” Optical Engineering,vol.42,no.8,pp.2331–2339,2003.
[8]R.Tao,Y.Xin,and Y.Wang,“Double image encryption based on random phase encoding in the fractional Fourier domain,” Optics Express,vol.15,no.24,pp.16067–16079,2007.
[9]C.-H.Chuang and G.-S.Lin,“An optical image cryptosystem based on adaptive steganography,” Optical Engineering,vol.47,pp.047002,Apr.2008.
[10]L.Chen and D.Zhao,“Optical color image encryption by wavelength multiplexing and lensless Fresnel transform holograms,” Optics Express,vol.14,no.19,pp.8552–8560,2006.
[11]M.Joshi,Chandrashakher,and K.Singh,“Color image encryption and decryption using fractional Fourier transform,” Optics Communications,vol.279,no.1,pp.35–42,2007.
[12]C.-H.Chuang and G.-S.Lin,“Adaptive Steganography-based Optical Color Image Cryptosystems,”in Proc.of the IEEE Int.Symposium on Circuits and Systems,Taiwan,2009,pp.1669–1672.
[13]Computer Vision Group(CVG).Department of Computer Science and Artificial Intelligence,University of Granada.[Online].Available:http://decsai.ugr.es/cvg/
[14]Kodak Lossless True Color Image Suite.[Online].Available:http://r0k.us/graphics/kodak/
[15]Programming/Image Processing/Video Codecs Resourses.[Online].Available:http://www.hlevkin.com/
 Journal of Electronic Science and Technology2013年1期
Journal of Electronic Science and Technology2013年1期
- Journal of Electronic Science and Technology的其它文章
- Design of MEMS C-Band Microstrip Antenna Array Based on High-Resistance Silicon for Intelligent Ammunition
- Low-Cost Embedded Controller for Complex Control Systems
- Data Hiding in DNA for Authentication of Plant Variety Rights
- An Image Authentication Method by Grouping Most Significant Bits
- Rejection of Direct Blast Interference Based on Signal Phase-Matching Array Processing
- Investigation on Active and Reactive Combined Spot Price Integrated with Wind Farm
