Privacy-Preserving Prepayment Based Power Request and Trading in Smart Grid
Shaohua Li, Xiang Zhang, Kaiping Xue,*, Lijie Zhou, Hao Yue
1 Department of Electronic Engineering and Information Science, University of Science and Technology of China, Hefei 230027, China.
2 Science and Technology on Communication Networks Laboratory, Shijiazhuang, Hebei, 050081, China.
3 Department of Computer Science, San Francisco State University, San Francisco, CA 94132, USA.
I. INTRODUCTION
With the development of IT and IoT technologies, smart grid is regarded as the next generation of power grid which utilizes information and communication technologies to achieve a more efficient, reliable, flexible and sustainable system [1-3]. Speci fi cally, smart grid uses two-way flows of electricity and information to create an automated and distributed energy delivery network. In smart grid, the control center can instruct the utility companies to generate electricity based on users’ demand requests, i.e., power request [4,5]. This mechanism is useful and desirable because users’electricity demand can always be satisfied.Another benefit is that the redundant power generation can be avoided, which cuts down the cost of the utility and makes less carbon dioxide emission to the environment [6,7].
Power request can be implemented in different ways [7,8]. For example, anonymous credentials are used for privacy preservation in[8]. Users request credentials from the control center in advance, and then submit their power usage demand by sending a certain number of the credentials back. The problem is that the actual consumption of the users is usually different from the demand they submit, which will seriously disturb the generation plans of the grid. As a common solution, an extra charge will be added to the users’ electricity bills to make up the utilities’ loss. Similarly,in [7], penalties will be imposed on the user if the submitted request and actual consumption do not match.
An accurate electricity demand estimation is not easy. Many unexpected occurrences,e.g., a business trip or a bad weather, would change the customers’ demand dramatically.Since the differences between users’ power requests and their actual consumption may lead to great losses and inconvenience, we need a new method more than simply imposing penalties on users. In fact, the changes of users’actual demand lead to the surplus or shortage of their original requests. A basic idea is to transfer the electricity from the users who request too much to the ones who request too little. In this way, the changes of most users’demand will be neutralized and the negative effect on the utility’s generation schedule will be minimized.
In order to realize the above idea, in this paper, we introduce a prepayment mechanism[9,10], which requires smart meters equipped with a built-in switch [11,12], and digital credentials called tokens used to represent users’demand. In every requesting phase, users can estimate the amount of electricity they will consume and make their power requests by paying the corresponding electricity bills in advance. At the same time, smart meters receive equivalent tokens for consuming electricity afterward. To adapt to the users’ dynamic demand, the control center runs an electricity trading market. If a user’s demand changes,he/she can sell or buy electricity tokens in the market before the next requesting phase.
Many studies have shown that users’ demand can reveal their private information [13,14]. Therefore, we need to ensure the privacy of these procedures. For example, if a user sells a lot of electricity tokens in the market,adversaries can infer that no one in the house and then break into it. Hence, users’ privacy must be properly preserved. In this paper, we propose a feasible solution in a privacy-preserving way. Specifically, our contributions are summarized as follows:
· We adopt the prepayment mechanism and propose a power request and trading scheme. By power request, the grid utilities can schedule the power generation, distribution, and transmission more economical;by electricity token trading, customers’ dynamic demand can be satis fi ed, thus achieving the win-win between customers and the grid utilities.
· We design two security protocols to protect individual privacy from the malicious adversary or semi-trust grid utilities, such as control center and the gateway. These two protocols can respectively meet two different requirements of the gateway deployment.
The remainder of the paper is organized as follows. Section II discusses the related works. System model and design goals are described in Section III. Our proposed scheme is presented in Section IV. Security and performance analysis is presented in Section V and VI respectively. We draw our conclusions in Section VII.
In this paper, we discuss the users’ dynamic demand and propose a power request and trading scheme to deal with it.
II. RELATED WORK
Smart grid has been widely studied in recent years [1, 2], and power request is one of the most fundamental problem. With the help of power request mechanism, the grid is supposed to be achieve outstanding balance between users’ demand and the utility’s supply [6, 15]. Usually, privacy protection is an essential requirement for an appropriate power request scheme [4, 13] as well as others [16,17]. The existing schemes for IoT security,such as [18–21], cannot be adopted to meet these requirements, especially privacy preserving. Methods in [7, 22, 23] adopted homomorphic encryption to aggregate users’ demand at the gateways so that no one can obtain particular user’s demand, including the control center. Chimet al.[8] proposed that extra charge should be imposed on user according to the difference between submitted demand and real consumption. Uludaget al.[24] proposed a hierarchical architecture to achieve secure and scalable data collection which can minimize the total collection time. Furthermore, Yanget al.[25] proposed a power request scheme which can not only achieve demand aggregation of multiple users but also provide demand traceability of malicious users.
Electricity trading is also an important component of smart grid [26–28]. Tusharet al.[26] proposed an energy trading scheme which considered price discrimination using game theory and achieved social and Pareto optimization. Wang.et al.[27] designed an incentive mechanism using Nash bargaining theory to encourage proactive energy trading and fair benefit sharing in interconnected microgrids.Specifically, an effective trading approach which adopted double auction mechanism and guaranteed an equilibrium point was provided in [28].
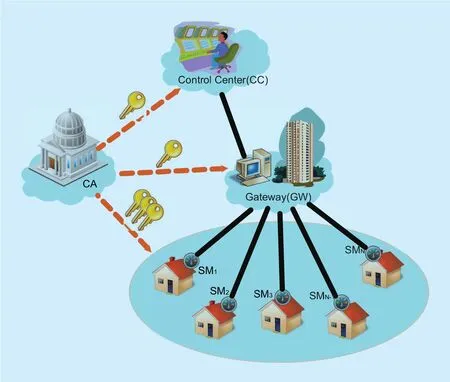
Fig. 1. System model.
Prepayment mechanism is very necessary to achieve effective electricity trading [29,30]. Tewariet al.reviewed the economics,logistics, and technology underlying the South African experiment of prepaid electricity [11].And Kuzluet al.discussed the communication technology requirements for electric service prepayment [9]. To reduce electricity loss, Jainet al.proposed a prepaid smart meter which contains a prepaid card analogous to mobile SIM card [12]. Once the prepaid card is out of balance, the consumer load is disconnected from the grid by the contactor.
III. SYSTEM MODEL, ADVERSARY MODEL, AND DESIGN GOALS
3.1 System model
As described in figure 1, we consider the following hierarchical smart grid system, which consists of four kinds of entities: a global certificate authority (CA), a control center (CC),a neighborhood area gateway and a number of smart meters (SM) for users.
· The certificate authority(CA)is a fully trusted entity in our system. All the other entities in the system apply for key pairs from CA. Especially, every smart meter can apply for multiple key pairs. We assume CA does not collude with control center or gateways.
· The control center(CC)is the coordinator
of the system, which controls power generation, transmission, distribution, power request, billing and so on. In our scheme, CC also runs an electricity trading market to support buying and selling between users.CC is assumed to be honest but curious. It follows the protocol honestly, but is also curious about users’ private information.
· The gateway(GW)is located in residential area and is responsible for message collection, forwarding, and possible computing tasks. We assume the GW is honest but curious, just like the CC. Based on the different storage and computation assumption,we consider two scenarios of the GW:
1) The GW has limited storage and computation capabilities. It only acts as a relay between smart meters and CC, and no complex operations will be executed on it.
2) The GW has sufficient storage and computation capabilities to perform highcost operations, such as asymmetric encryption and decryption. We call this kind of gateway as an enhanced gateway.
We will introduce our scheme under the above two scenarios in Section IV. Specifically, we will first introduce our scheme under the first scenario in detail, and then briefly describe the main changes of the scheme under the second scenario.
·Smart meters(SM)are installed in users’homes and used to generate power requests.Each SM contains a built-in switch controlling whether the user can consume the electricity. To guarantee the protocol runs properly, we assume that the switch cannot be broken from outside and users cannot access the grid without the smart meters.
3.2 Adversary model
We assume that an adversary can either be an outsider or insider. An outside adversary mainly aims at intruding users’ privacy, disturbing normal operations or even compromising the grid utilities. We consider that the outside adversary is able to eavesdrop all network communications, replay the transmitted messages,as well as inject bogus messages to the grid. If the adversary is an insider, besides eavesdropping, replaying and injecting messages, it can also commit frauds in electricity payment. For example, when users consume electricity by specialized tokens, the inside adversary may try to consume electricity by forging or double spending tokens.
3.3 Design goals
Our design goal is to develop a privacy-preserving power request scheme which can also enable usage control and electricity trading for users. Specifically, the following three objectives will be achieved.
· An electricity trading market should be provided. Users can buy or sell electricity tokens in this market to decrease the losses caused by the dynamics of their demand.
· A usage control mechanism should be included. It means users cannot consume the electricity they have not requested. It guarantees the effective trading operation.
· Users’ privacy should be well preserved.Unauthorized entities cannot know how much electricity a user intends to consume or trade, including GW and CC.
IV. PROPOSED SCHEME
In this section, we present the details of our proposed scheme. We fi rst introduce the general procedures for users to request, consume and trade electricity. Then we describe the details of power request by prepayment. After that, how to consume electricity with tokens is elaborated. Finally, we present the implementation of the electricity trading market.
To be noted, as we introduced in Section III-A, we consider two different assumptions about the storage and computation capacity of the GW. In the section, we first present our detailed scheme under the first assumption,that is, the GW has limited storage and computation resources, and will be used as a relay between the SMs and CC. Then, we will show the changes of the scheme under the second scenario in the last subsection.
4.1 Overview
As shown in figure 2, we define a consumption phase as a period of one week or one month.At the end of every consumption phase, i.e., in requesting phase, users request the electricity they plan to consume in the next consumption phase. Electricity price in requesting phase is normal and fixed. The control center could predict the electricity demand of a region, and then make a reasonable distribution of electricity.
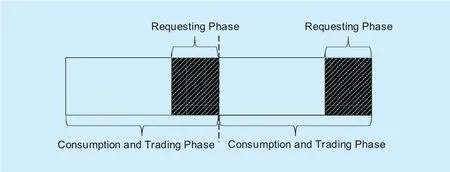
Fig. 2. General procedure.
To make sure that users estimate their electricity bills as accurate as possible, financial measures are necessary. If users need extra electricity after the requesting phase, they can make new requests at a higher price (e.g., 1.5 times of the original price). If users cannot consume all the electricity they requested by the end of the consumption phase, the tokens will be reclaimed by the control center at a lower price (e.g., half of the original price).Meanwhile, an electricity trading market is provided, where users can declare their desired electricity and price to the control center,and the control center operates the trading according to their bids. The trading phase is overlapped with the consumption phase but it must be completed before the next consumption phase starts.
4.2 System initialization
The CA is responsible for generating secret keys for SMs and CC. For each smart meterSMi, it generatesmpublic/private key pairs,denoted asAnd for the CC, it generates
Then, the CA distributes the secret keys to eachSMiand CC. At the same time, thePKCCand all thePKijare sent toSMiand CC, respectively.
4.3 Power request with prepayment
Next, we present our proposed power request procedure with prepayment in detail. In the requesting phase, userquestsdikWh of electricity through his/her smart meterSMito CC by prepayment.SMidivides the demanddiintomrandom parts,satisfying:
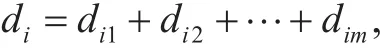
which will be requested withmpairs of keys ofSMirespectively. Without losing generality, we take the steps of requestingdi1with the key pairas an example, wherePKi1is one ofSMi’s public keys andSKi1is the corresponding private key. As shown in figure 3, it includes the following steps:
·Step-1:SMichooses a random number as the secret keyK1and computes:wherePKCCis the public key of CC, andTSis the current times tamp. The operator “||” denotes the concatenation of two strings or messages.ThenSMigenerates a signature onCi1with its private key:sendsto CC. CC checks the signatureSi1withPKi1and accepts the signature if the following equation holds:
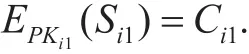
After checking the validity, CC decryptsCi1to obtainandTS′. IfTS′is a valid timestamp, CC encryptswithPKi1and sends it toSMi.
·Step-2:By decryptingwithSKi1,SMiobtainsand compares it withK1.If they are equivalent, a secure channel betweenSMiand CC has been established andK1is the session key. From now on, all the communications between them will be encrypted withK1. Then,SMicomputesand sends it to CC, wheredi1is the fi rst part of user i’s demand.
·Step-3:CC decryptsand obtainsdi1. Then CC computeswhere H is a hash function. Also, a payment message, e.g.,a web link of paypal, forSMiis generated, which is denoted asPMi1. After that,CC sendstoSMiand waits the demanddi1to be paid.SMireceives and decryptsextractPHi1andPMi1. IfPHi1equals touseriwill pay for the demand online according toPMi1.
·Step-4:After the payment is done, CC generates corresponding tokens forSMi.For the purpose of preserving privacy, the number of the generated tokens is fi xed no matter how muchdi1is. These tokens can be expressed aswhere c is a constant anddi1kWh of electricity can be consumed using thectokens. Then CC computesand sendstoSMi.SMirequest the tokens andTHi1by decryptingAfter checking the validity ofTHi1,SMistores thesectokens.
Aftermtimes of the above operations,SMisubmits its demanddito the control center successfully. However, CC will not know how much electricity userirequests, because the secure communications of power request are based on different keys, and CC cannot associate any keys to anySM.
4.4 Tokens and consumption
Essentially, tokens are the legitimate credentials that users purchase from CC. Every token can be expressed as:

Herenis the denomination represented in the token, which meansnkWh of electricity is allowed to be consumed.Trepresents a time point after which the token cannot be used anymore, andris a random number to avoid two identical tokens.is CC’s signature on. Since no one knows CC’s private key, except CC itself, the signature cannot be generated correctly, and hence a valid token cannot be forged.
The switch inSMiis off by default andSMineeds to send its tokens to CC to turn the switch on. Once the switch is on, userican consume electricity from the grid. The detailed steps are:
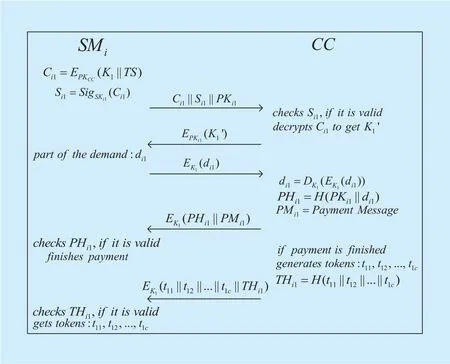
Fig. 3. Power request by prepayment.
·Step-1:SMichooses one of its key pairsand establishes a secure channel with CC. In addition to using a different session key, the secure channel is exactly the same as the one established in the requesting phase. So we will not repeat the process. Then,SMichooses one of its tokens, denoted bytve, and usesSKivto create a signature onand sendsto CC.
·Step-2:Upon receivingCC acceptstveas a valid token if the signature intveis valid. Then, CC checks iftveis already used. It maintains a database of all the used tokens and users’ signatures on them and queriestvein the database.Iftveis not in the database, CC verifies the validity ofsuccessfully(CC accepts the signature if the equation holds:After that,CC addstveandto the database and sends a veri fi cation success message oftveto theSMi.
·Step-3:SMireceives the verification success message and checksnve, which is the denomination represented intve. The switch inSMistays on untilnvekWh of electricity is consumed completely. By then, another unused token will be sent to CC. When all the tokens are used, user i will be cut off from the grid.
Note that in the consumption phase, although users send their tokens to the control center, the control center still does not know anything about any user’s demand or consumption information.
4.5 Trading market
As we discussed above, users’ demand changes dynamically and the electricity they requested may not be the same as they consume actually. However, if users are in shortage of their original requests, they can further request more from the control center, but the price would be much higher than that of the original ones. Also, if they requested too much beyond they actually need, the electricity will be reclaimed by the control center at a very low price. In either situation, users have to take fi -nancial losses eventually. Driven by that, users can choose to trade electricity in the market to minimize their losses. Since electricity is provided by tokens, the trading of electricity is actually the trading of tokens.
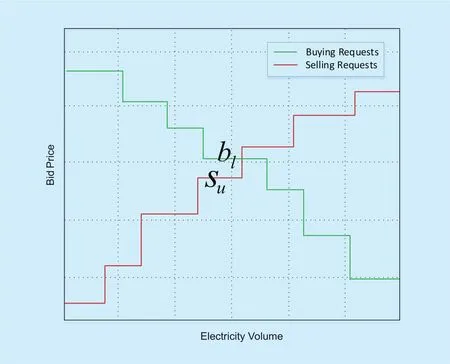
Fig. 4. Double auction.
The trading market is open to users in every consumption phase. When userdecides to participate in the market,SMifirst establishes a secure channel with CC using one of its key pairs. If useriis a buyer,SMican choose a random key pair. But if useriis a seller,SMican only use the key pairs with which the tokens to be sold can be obtained. For brevity, we denote the key pair asWith some interactions,SMilearns about useri’s trading information, including useriwants to buy or sell tokens, the amount of the tokens useriwants to trade, and the price. The trading information can be denoted asBS,QandP, respectively.SMigenerates a signature on them:and sendsto CC through the aforementioned secure channel.
After receiving the useri’s trading request message, CC checks the signature withPKi.If it is valid, CC accepts the request and divides all accepted requests into two categories according toBS: buying bids and selling bids.Because the total amount of the electricity the buyers want to purchase and the sellers want to sell can be different, we need to determine who is allowed to trade and who is not. Besides, the price at which the buyers and sellers make a deal is also important. Since many buyers and sellers are involved, double auction mechanism can be employed as in [28]. CC conducts the double auction and the trading by the following steps:
·Step-1:Assume there are X buyers andYsellers. Denote the buying bids a swherebjis buyerj’s bid andxjis the buying amount, and denote the selling bids aswhereskis sellerk’s bid andykis the selling amount.
·Step-2:CC sorts the buying bids in a decreasing order as follows:Also, CC sorts the selling orders in an increasing order such that we have:Then, the buying curve(buyers’ bidsbjas a function of the buying amountand the selling curve (sellers’ bidsskas a function of the selling amountcan be generated, as shown in figure 4. These two curves will intersect at a point that corresponds to a buying bidand a selling bidThis intersection point is easily computed using known numerical and graphical techniques.
According to the double auction theory,lbuyers andusellers can participate in the trading process except that buyerland sellerucan only trade a part of their request amount. The trading price should be within the intervalWithout loss of generality,all buyersj≤land sellersk≤uwill trade tokens at a priceptwherepossible that buying curve and selling curve have no intersection, which means no buyer or seller can participate in the trading, or all buyers and sellers can participate in the trading and the trading priceptcan be seen asl=Xandu=Y.
·Step-3:The l buyers andusellers receive a message indicating that they are allowed to proceed trading. The message also includes the trading price and the number of tokens the buyer or seller can trade. According to the message, every buyer pays for his/her buying amount to CC and every seller sends his/her selling tokens and a signature on these tokens to CC. To preserve their privacy, the money buyers pay will not be available to the sellers right away but will be used to offset when the sellers pay for tokens in the next requesting phase. After verifying the tokens and the signatures from the sellers and adding them to the database,CC calculates the difference between the sum of the denominations represented in the tokens and the allowed trading amount of each seller. Then, CC generates new tokens for sellers according to the difference and for buyers according to their payment.Finally, the tokens are sent to the buyers and sellers through secure channels.
Because CC may receive the trading requests at any time, the auction operation will happen at intervals of, e.g., one hour. Every time CC executes a double auction, both the new traders and the ones who failed to trade before are involved. To increase the possibility of trade, the former traders can send fresh bids to override their original bids. They can also stick to their original bids to maximize their benefit.
In the extreme case, there may be still a lot of buyers and sellers remaining in the market who do not give in about their bids so the trading cannot carry on. But this case will not happen or last long. Based on the assumption of rational behavior, For the buyers, if they do not raise their bids and trade in time, the tokens in the market will bid by others at a higher price, and they will purchase tokens from CC, where the tokens are more expensive. For the sellers, it is similar that if they stick to their original bids, their surplus tokens can only be abused or reclaimed by CC at a very low price. In short, compared with being stubborn and no trading, the buyers and sellers will always benefit more from the trading. It is just a matter of buyers and sellers gaming who give in first and how much they give in. We do not care about the detailed process, and know that the market will reach a point eventually,only selling or buying bids will remain.
4.6 Proposed scheme with enhanced gateway
The above procedures assume that the GW is a relay between the SMs and CC, and does not perform any complex computations. But sometimes, there may deploy a GW with strong computing power. We here provide an alternative scheme for this scenario. We will show the main changes to each phase in the following description, and the same procedures will be omitted.
1) System Initialization:In this scenario,each smart meterSMionly needs one pair of secret keyswhile it ismunder the fi rst scenario. And the GW here will be distributed with a pair of secret keysby CA. As for CC, it also hasas its key pairs.
2) Power Request with Prepayment:In the requesting phase, the main change is that every request or response from SMs and CC should be processed by the GW first, which guarantees the individual users’ privacy as well as reduces the computation overhead of both SMs and CC. When userwants to requestdikWh, instead of dividingdiintomrandom parts,SMiencryptsdidirectly with the session key established with CC. And the session key establishment is based on the onlyofSMi, which is quite different from the previous version, in which theSMihasmkey pairs. The changes of each steps are as follows:
·Step-1:SMicomputeswhereKiis a random session key andTSis the current time stamp. ThenSMigeneratesand sendsto the GW, who will accept the signature ifequals toCi. After verification,the GW generates a new signature onCi:and sendsto CC,who will verify and decrypt theCito obtain the session key.
·Step-2:We cancel this step due to the verification of the session key can be done in the third step, and the GW replaces the CC to verify the public key ofSMi.
·Step-3 & Step-4:We replace thePKi1inPHi1with an alias generated by the GW.This alias is unique and will be regenerated forSMion each requesting phase. TheSMican obtain its alias from the GW. The rest procedures are the same as previous,we do ot repeat them here.
3) Tokens and Consumption:Recall that during this phase, the previous procedures that related toSMi’s identity are the signature generation of thetveand its verification inStep-1& Step-2. Now, in this new scenario, theSMiwill sendto GW instead of CC. And the GW will verify the legitimacy ofthen regenerate a new signatureand forwardCC to complete the next procedures. The rest of consumption phase is the same as before.
4) Trading Market:Just like the previous consumption phase, the trading information and its signature will be verified by the GW firstly in this scenario, after which the GW will generate a new signature for CC to verify.Speci fi cally, theSMigenerates a signature on the trading informationand forward it as well asto the GW, which will verify the information and generate a new signaturefor CC to verify. Other processes remain no change.
We declare that the powerful GW will reduce the burden of both SMs and CC before.From the above changes, we can conclude the following advantages:
· During the requesting phase, eachSMino longer needs to generatemrequests to protect its privacy. Instead, he/she only generates one request. This is because the non-colluding GW will verify the requests and regenerate a new signature, while only the CC can know thedivalue. At the same time, the CC also only needs to verify once for eachSMiin each requesting phase.
· In every phase, especially the requesting phase, manySMimay send the messages simultaneously. After verifying each signature, the GW can generate one signature for all the messages, so that the CC only needs to verify once, too. This will significantly reduce the overhead of signature verification.
V. SECURITY ANALYSIS
In this section, we analyze the security properties of our proposed scheme in three phases:requesting phase, consumption phase, and trading phase. To be noted, the analysis below is based on the first scenario, and we omit the security analysis of the scheme under the second scenario. This is because the latter only changes the verification procedures of the former, the security guarantee of which is straightforward.
5.1 Requesting phase
· Mutual authentication: Smart meterwith public keyPKican obtain CC’s public keyPKCCfrom CA and generate the ciphertextwhich can only be decrypted by CC. Once CC sends theback andthe smart meter can believe it is from the CC and CC is authenticated. Using the similar method, CC can also achieve the authentication of every smart meter.
· Privacy-preservation: In our scheme, each smart meter owns multiple keys, which can be regarded as its different identities. The smart meter divides the demand into multiple parts and requests the parts with different identities separately. CC only knows each part of the demand is requested using a legitimate identity, but it cannot learn which keys belong to the same smart meter.Thus, every user’s demand information is well preserved.
· Confidentiality: Once CC and the smart meter finish the authentication, they both calculate a secret session key K. Since no one else can obtainK, the confidentiality of the following communications encrypted with theKcan be achieved.
5.2 Consumption phase
· Defense against token reusing: When a user wants to consume electricity, the smart meter has to send a token and corresponding signature to CC for verification. CC maintains a database of all used tokens and signatures. Every time CC receives a token,CC checks whether it is a valid token and then queries it in the database. If the token can be found in the token database, the verification will fail and the switch will stay off. As a result, reusing a token is impossible in our scheme.
5.3 Trading phase
During the electricity trading, our scheme can also achieve privacy-preservation and defense against token reusing. Like in the requesting phase, the smart meter participates in the trading with different keys. Since CC cannot associate these keys with a specific smart meter, the privacy of user’s trading amount can be preserved. Moreover, when sellers sell their tokens, the tokens and sellers’ signatures on them are sent to CC and added into the database. Clearly, the sellers are not able to receive electricity by using these tokens anymore.
VI. PERFORMANCE ANALYSIS
In this section, we will evaluate the performance of our scheme in terms of computation and communication overhead.
We use RSA, AES, and SHA-1 to evaluate the computation overhead of our scheme. Corresponding parameters are defined as follows:
·TAdenotes the time for RSA-1024 encryption/decryption/signature operation.
·TSdenotes the time for AES-128 encryption/decryption operation.
·THdenotes the time for SHA-1 operation.
6.1 Computation overhead
We here consider the computation overhead under the first scenario. Since the gateways only forward the messages between smart meters and the control center, we do not takeinto consideration their computation overhead.Table 1 shows the computation overhead of requesting tokens, verifying a token and trading tokens for smart meters and the control center. Every smart meter hasmpairs of keys and requestsctokens with every pair of keys, so the computing time of a complete power request isandfor smart meters and the control center respectively. Compared with requesting tokens, the verification and trading of the token are less frequent, and hence the smart meters and control center have enough computation resources to process them. Thus, we only focus on the computation overhead of requesting tokens.
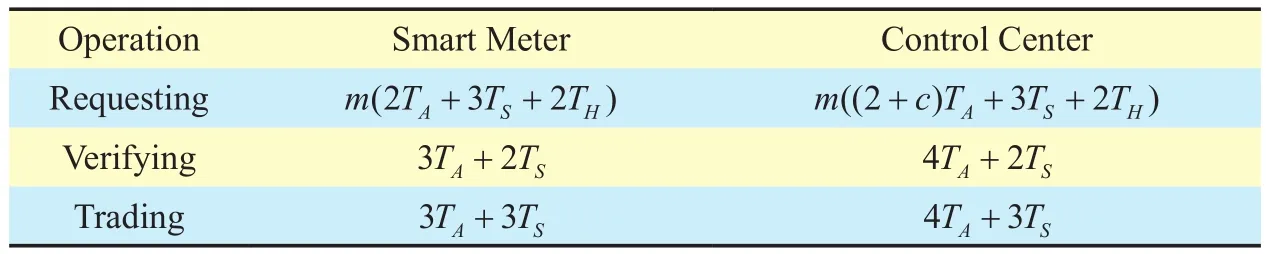
Table I. Computation overhead.

Table II. Computation Overhead under Enhanced Gateway.
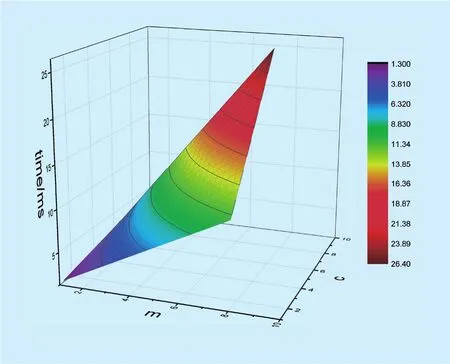
Fig. 5. Computation overhead of requesting tokens in the first scenario.
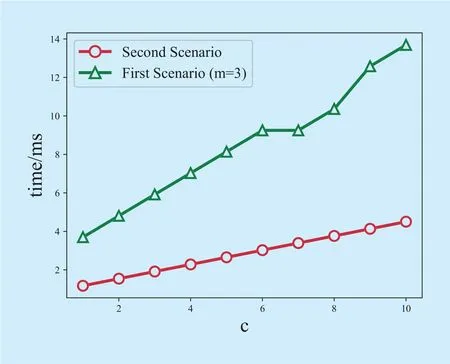
Fig. 6. Computation overhead of requesting tokens in the second scenario.
In our experimental environment (CPU: 2.0 GHz, RAM: 4.0 GB), we run 1000 times to obtain the average result. We fi nd thatTAis approximately 9 times faster thanTSand 25 times faster thanHT(TAis about 0.37ms on average when using RSA-1024,TSis nearly 0.041ms on average when using AES-128-cbc, andTHis about 0.015ms when using SHA-1). Clearly,the overhead of smart meters increases linearly with the increase ofmwhile the overhead of the control center is more complex.
Figure 5 shows the computation overhead variation of the control center with differentcandm. Although a largermimproves the security and a largercmakes trading more convenient, the computation overhead also increases ascandmgrow. There is a trade-off between security and computation overhead.According to our experiments, we believe thatm=3 andc=5 can achieve both high security and low computation cost. In this case, the total time required for requesting tokens for every smart meter is 2.67ms and the total time for control center to serve a smart meter is 8.16ms. Considering that the computation only happens in requesting phases and requesting phases may last for several days, the overhead is affordable for the control center and smart meters.
6.2 Computation overhead under enhanced gateway
Table 2 shows the computation overhead of requesting tokens, verifying a token and trading tokens for smart meters, the gateway,and the control center. Compared with the computation overhead under the fi rst scenario,the gateway has extra computation, that is 2TAfor each operation. But the computation overhead of requesting operation is fixed, while the former depends onm. Figure 6 shows the comparison of the communication overhead of the control center in different scenarios. We can see that the computation cost of the second scenario with the enhanced gateway has a significant improvement than the first one withm=3, which is the recommended value ofmin Section VI-A. As we described before, there is a particular advantage in the scheme under the enhanced gateway, that is, when some requests arrive at GW simultaneously, the GW could generate one signature for all of them. And the CC also needs to verify only one signature for them. This feature can significantly decrease the computation overhead of both the GW and the CC.
6.3 Communication overhead
In our scheme, the communication overhead mainly comprises of RSA ciphertexts/signatures and AES ciphertexts. Whenm=1, both two scenarios have almost the same communication overhead. Assume that we use 1024-bit RSA, 128-bit AES and 160-bit SHA-1.The length of a token is 128+128+1024 =1280 bits. The communication overhead of requesting, verifying and trading tokens once is 6688+1280c bits, 9600 bits, and 10624 bits, respectively. Whenc=5, the overhead is 1.4KB, 1.2KB and 1.3KB, respectively. Obviously, the communication overhead is considered acceptable.
To be noted, the communication overhead of the second scenario is independent ofm,while that of the fi rst scenario increases linearly withm.
VII. CONCLUSION
In this paper, we discuss the users’ dynamic demand and propose a power request and trading scheme to deal with it. We adopt the prepayment mechanism to make electricity trading possible. And the trading market provides an effective way for users to minimize their losses. Furthermore, we show our scheme under the enhanced gateway. Security analysis indicates that the privacy of users’original demand and their trading amounts is well preserved, and performance analysis further demonstrates the ef fi ciency of our scheme in terms of computation and communication.
ACKNOWLEDGMENTS
This work is partly supported by the National Key Research and Development Plan of China under Grant No.2016YFB0800301, the Fund of Science and Technology on Communication Networks Laboratory under Grant No. KX162600024, and Youth Innovation Promotion Association CAS under Grant No.2016394. Shaohua Li and Xiang Zhang contributed equally to this work (co- fi rst authors in alphabetical order). The preliminary results were presented at IEEE ICCC2017.
References
[1] X. Fang, S. Misra, G. Xue, and D. Yang, “Smart grid - the new and improved power grid: A survey,”IEEE Communications Surveys & Tutorials, vol. 14, no. 4, pp. 944–980, 2012.
[2] K. Moslehi and R. Kumar, “A reliability perspective of the smart grid.”IEEE Transactions on Smart Grid, vol. 1, no. 1, pp. 57–64, 2010.
[3] W. Han and Y. Xiao, “Privacy preservation for v2g networks in smart grid: A survey,”Computer Communications, vol. 91, pp. 17–28,2016.
[4] S. Zeadally, A.-S. K. Pathan, C. Alcaraz, and M.Badra, “Towards privacy protection in smart grid,”Wireless Personal Communications, vol. 73,no. 1, pp. 23–50, 2013.
[5] T. Chim, S. Yiu, and L. H. V. Li, “PASS: Privacypreserving authentication scheme for smart grid network,” inProceedings of the 2nd IEEE International Conference on Smart Grid Communications. IEEE, 2011, pp. 196–201.
[6] I. Koutsopoulos and L. Tassiulas, “Optimal control policies for power demand scheduling in the smart grid,”IEEE Journal on Selected Areas in Communications, vol. 30, no. 6, pp.1049–1060, 2012.
[7] T. Chim, S. Yiu, V. Li, L. Hui, and J. Zhong,“PRGA: Privacy-preserving recording & gateway-assisted authentication of power usage information for smart grid,”IEEE Transactions on Dependable and Secure Computing, vol. 12, no.1, pp. 85–97, 2015.
[8] T. Chim, S. Yiu, L. Hui, and V. Li, “Privacy-preserving advance power reservation,”IEEE Com-munications Mag- azine, vol. 50, no. 8, pp.18–23, 2012.
[9] M. Kuzlu, M. Pipattanasomporn, and S. Rahman,“Communication network requirements for major smart grid applications in han, nan and wan,”Computer Networks, vol. 67, pp. 74–88,2014.
[10] M. Parvin, S. Kabiret al., “A framework of a smart system for prepaid electric metering scheme,” inProceedings of the 4th International Conference on Informatics, Electronics & Vision.IEEE, 2015, pp. 1–5.
[11] D. D. Tewari and T. Shah, “An assessment of south african prepaid electricity experiment,lessons learned, and their policy implications for developing countries,”Energy Policy, vol.31, no. 9, pp. 911–927, 2003.
[12] A. Jain and M. Bagree, “A prepaid meter using mobile communication,”International Journal of Engineering, Science and Technology, vol. 3,no. 3, 2011.
[13] X. Li, X. Liang, R. Lu, X. Shen, X. Lin, and H. Zhu,“Securing smart grid: cyber attacks, countermeasures, and challenges,”IEEE Communications Magazine, vol. 50, no. 8, pp. 38–45,2012.
[14] S. Tan, D. De, W.-Z. Song, J. Yang, and S. K.Das, “Survey of security advances in smart grid:A data driven approach,”IEEE Communications Surveys & Tutorials, vol. 19, no. 1, pp. 397–422,2017.
[15] M. Erol-Kantarci and H. T. Mouftah, “Wireless sensor networks for cost-efficient residential energy management in the smart grid,”IEEE Transactions on Smart Grid, vol. 2, no. 2, pp.314–325, 2011.
[16] A. Boustani, A. Maiti, S. Y. Jazi, M. Jadliwala, and V. Namboodiri, “Seer grid: privacy and utility implications of two-level load prediction in smart grids,”IEEE Transactions on Parallel and Distributed Systems, vol. 28, no. 2, pp. 546–557, 2017.
[17] S. Li, K. Xue, Q. Yang, and P. Hong, “PPMA: Privacy- preserving multi-subset aggregation in smart grid,”IEEE Transactions on Industrial Informatics, vol. 14, no. 2, pp. 462–471, 2018.
[18] X. Yao, X. Han, X. Du, and X. Zhou, “A lightweight multicast authentication mechanism for small scale IoT applications,”IEEE Sensors Journal, vol. 13, no. 10, pp. 3693–3701, 2013.
[19] X. Hei and X. Du, “Biometric-based two-level secure access control for implantable medical devices during emergencies,” inProceedings of the 30th IEEE International Conference on Computer Communications(INFOCOM). IEEE, 2011,pp. 346–350.
[20] K. Xue, C. Ma, P. Hong, and R. Ding, “A temporal- credential-based mutual authentication and key agree- ment scheme for wireless sensor networks,”Journal of Network and Computer Applications, vol. 36, no. 1, pp.316–323, 2013.
[21] C. Ma, K. Xue, and P. Hong, “Distributed access control with adaptive privacy preserving property for wireless sensor networks,”Security and Communication Networks, vol. 7, no. 4, pp.759–773, 2014.
[22] H. Li, X. Lin, H. Yang, X. Liang, R. Lu, and X.Shen, “EPPDR: an efficient privacy-preserving demand response scheme with adaptive key evolution in smart grid,”IEEE Transactions on Parallel and Distributed Systems, vol. 25, no. 8,pp. 2053–2064, 2014.
[23] A. Abdallah and X. Shen, “Lightweight security and privacy preserving scheme for smart grid customer-side networks,”IEEE Transactions on Smart Grid, vol. 8, no. 3, pp. 1064–1074,2017.
[24] S. Uludag, K.-S. Lui, W. Ren, and K. Nahrstedt,“Secure and scalable data collection with time minimization in the smart grid,”IEEE Transactions on Smart Grid, vol. 7, no. 1, pp. 43–54,2016.
[25] Q. Yang, J. Hong, K. Xue, W. Chen, X. Zhang,and H. Yue, “A privacy-preserving and real-time traceable power request scheme for smart grid,” inProceedings of 2017 IEEE International Conference on Communications (ICC).IEEE, 2017, pp. 1–6.
[26] W. Tushar, C. Yuen, D. B. Smith, and H. V. Poor,“Price discrimination for energy trading in smart grid: A game theoretic approach,”IEEE Transactions on Smart Grid, 2017.
[27] H. Wang and J. Huang, “Incentivizing energy trading for interconnected microgrids,”IEEE Transactions on Smart Grid, 2016.
[28] Y. Wang, W. Saad, Z. Han, H. V. Poor, and T.Basar, “A game-theoretic approach to energy trading in the smart grid,”IEEE Transactions on Smart Grid, vol. 5, no. 3, pp. 1439–1450, 2014.
[29] Q.-D. Ho, Y. Gao, and T. Le-Ngoc, “Challenges and research opportunities in wireless communication networks for smart grid,”IEEE Wireless Communications, vol. 20, no. 3, pp. 89–95,2013.
[30] R. C. Green, L. Wang, and M. Alam, “Applications and trends of high performance computing for electric power systems: Focusing on smart grid,”IEEE Transactions on Smart Grid, vol. 4, no. 2,pp. 922–931, 2013.
- China Communications的其它文章
- Identity-Based Encryption with Keyword Search from Lattice Assumption
- Vortex Channel Modelling for the Radio Vortex System
- New Precoded Spatial-Multiplexing for an Erasure Event in Single Frequency Networks
- Microphone Array Speech Enhancement Based on Tensor Filtering Methods
- Uplink Grant-Free Pattern Division Multiple Access(GF-PDMA) for 5G Radio Access
- Smart Prediction for Seamless Mobility in F-HMIPv6 Based on Location Based Services

