A Master-Slave Blockchain Paradigm and Application in Digital Rights Management
Zhaofeng Ma, Weihua Huang, Wei Bi, Hongmin Gao, Zhen Wang School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing 00876, China
2 Shenzhen Datong Industrial Co..Ltd, Shenzhen 518000, China
3 SeeleTech Corporation, San Francisco, 94107, USA
Abstract: Upon flaws of current blockchain platforms of heavyweight, large capacity of ledger, and time-consuming of synchronization of data, in this paper, we proposed a new paradigm of master-slave blockchain scheme(MSB) for pervasive computing that suitable for general PC, mobile device such as smart phones or PADs to participants in the working of mining and verification, in which we separated traditional blockchain model in 2 layer defined as master node layer and a series of slavery agents layer, then we proposed 2 approaches for partially computing model(PCM) and non-computing of model(NCM) in the MSB blockchain, Finally large amounts of simulations manifest the proposed master-slave blockchain scheme is feasible, extendible and suitable for pervasive computing especially in the 5G generation environment,and can apply in the DRM-related applications.
Keywords: master-slave blockchain; proof of equivalent work; proof of contribution; pervasive computing; DRM application
I. INTRODUCTION
The original and core motivation of blockchain is to build up a cryptography-based decentralized digital currency system for self-organization transaction in an anonymous.Current blockchain platforms such as Bitcoin,Ethereum or Hyperledger provide a new and promising technology for digital cryptocurrency, distributed trusted data management or supply chain manangement[1-4]. However either Bitcoin or Ethereum and HyperLdger needs to synchronize the lager capacity of ledger, once the host is used as blockchain node for mining or verification, the whole computing memory and resource is occupied for computing, synchronizing, storing data by the blockchain system, in fact,current blockchain system is heavyweight and is difficult for extendible. In general case, blockchain is a decentralized trusted p2p platform which provides a cryptography-based trusted computing paradigm that all the transactions are constructed in a merkle-tree, and the specific transactions are organized under a unique
merkle-root, then in a proper time interval,then creates a block that include block header and block body, and the block header usually include timestamp, previous block hash, dif ficulty, version and reward.
As thefirst implemented blockchain appliciaiton, Satoshi Nakamoto first proposed the famous Bitcoin system in his paper “a peer-to-peer electronic cash system” as the genesis innovation of decentralized digital cash system[1], in which the Bitcoin uses a proof-of-work mechanism to ensure the fair work of the computing and security[2], if someone try to modify the blocks existing in the blockchain, the proof-of-work consensus can ensure the block cannot be changed without redoing the work.As later blocks are chained after it, the work to change the block would include redoing all the blocks[1-3]. Upon the peer to peer network,when constructing the block, new transactions are broadcast to all nodes, then each node collects new transactions into a block, each node works on finding a difficult proof-of-work for its block, When a computing node finds a proper difficult by proof-of-work, it then broadcasts the block to all p2p nodes, thosed nodes accept the block only if all transactions are valid and not already spent. nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.
Bitcoin is an innovative payment network and supports for rewards for mining or verification, however, Bitcoin is not so efficient for real-time transaction, and it is difficult and complex to developers, to solve the problems,Vitalik Buterin first proposed the kernel of Ethereum blockchain system which attempt to solve the efficiency and extendibility of the blockchain[5-7]. The Ethereum is a Turing-complete language which generally can solve the problem if there’s enough time and storage space(whereas bitcoin is not Turning-complete), which supports Ethereum externally owned accounts (EOAs) and smart contract accounts, which is defined by its internal unique address, that can execute any possible user-defined codes according to user’s needs and requirements via ERC20, the smart contract is executed in the Ethereum Virtual Machine(EVM). Ethereum is more flexible,extendible, easy and simple for users to build up variant blockchain by creates unique Token(defined by unique address)[3].
While Hyperledger fabric[4] provides a new, secure and enterprise consortium blockchain platform, which supports for manage node, verification node, each user should connect each other by certificates, and Hyperledger fabric is suitable for consortium blockchain for secure data management. The fabric is based on the most main source code from IBM, which does not support mining but is available for constructing consortium-based blockchain for authorized blockchain members.
In fact, the blockchain is defined as a cryptographic-based p2p distributed ledger with high-level security, credit, consensus and reward, which can build up variant application such as digital cryptocurrency, supply chain management, digital rights management[5-13].in [14], the authors innovated a scheme of de-anonymizing social networks with overlapping community structure, and proposed a well-justified cost function minimizing the expected number of mismatched users over all possible true mappings. In fact, the efficiency, blockchain capacity and computing node, especially the computing ability restricts and limits general terminal and endpoint computing device joining into the mining and computing. If considering the computing and availability of mobile device, such as mobile phones, PAD, and personal computer, it need to consider flexible and extendible computing paradigm for blockchain for personal computing devices as light-weight blockchain nodes with fair consensus[9-10,13].
II. RELATED WORK
2.1 Current popular blockchain technology
2.1.1 Bitcoin and its extendible blockchain platform
As the first successfully implemented blockchain application, Bitcoin[1-2] innovated the peer-to-peer electronic cash system as the original blockchain implementation, which proposed the cryptocurrency in a self-organi-zation mode in P2P network, which verifies,constructs, synchronizes and stores the blockchain data permanently. However the Bitcoin is considered as low-efficient in TPS( only 7 TPS), and the average amount of the block is nearly 1MB, and the Bitcoin is not so efficient and is difficult to extend the architecture such as capacity, efficiency and instance of the transaction verification. Upon the Bitcoin-class blockchain, such as LiteCoin, Lighting Network are innovated and tried to solve the problem. Upon the efficiency, it is heavyweight and cannot be separated the mining module into layered subsystem to enhance the efficiency, which limited the extendibility of the Bitcoin-like blochchain.
2.1.2 Ethereum blockchain and its Tokenbased Innovation
To implement an extendible and reliable blockchain, Mr Butlin innovates a flexible blockchain Ethereum[3] and ERC20, in which Ethereum implements the paradigm in a generalized manner. And it provides a plurality of such resources, each with a distinct state and operating code but able to interact through a message-passing framework with others. Ethereum designed, implemented, and issued the flexible, useful, extendible platform for a new and flexible blockchain paradigm, especially it innovated the ERC20 protocol, which can make it easy to define a new token-based digital currency in public blockchain.
2.1.3 Hyperledgerfabric consortium blockchain platform
Hyperledger fabric[4] provides a new, secure and enterprise consortium blockchain platform, which supports for authentication node,manage node, verification node, Hyperledger fabric is suitable for consortium blockchain for secure data management, such as supply chain management, traceability of source management, and public beneficence management[4-6, 12].
2.1.4 Other new blockchian technologies
As for the efficiency, capacity, and security,the other new blockchain technologies such as lighting network, cross-blockchain, muli-blockchain technologies have been studied for more efficient and high-performance transaction capacity[5-12]. And there still exists DAG, EOS[18] public blockchain technologies, which will try to provide a more efficient and effective transaction process ability in TPS, transaction fee.
2.2 Existing problems and flaws of current blockchain
2.2.1 Lacks of extendible architecture of blockchain[9-10]
Current blockchain technologies such as Bitcoin, Ethereum and hyperledger provide a cryptography ensured P2P distributed ledger,to ensure the fair and secure transactions, its supports kinds of consensus such as PoW,PoS, DPoS, PBFT. However, current blockchain is difficult to extend to a flexible, reliable and efficient computing paradigm that allows more and more computing units join in the computing and verification.
2.2.2 Heavy-weight but low efficiency of TPS[1-3]
Current blockchain provides a distributed and trusted leger with blocks and transaction, but current blockchain node is not so efficient in TPS, not so flexible especially in a heavyweight mode, it cannot extend for distributing the task to other computing unit such as general PC, mobile smart phones or PADs to participants the work of computing.
2.2.3 Lack of consensus for new blockchain paradigm[12,15-17]
Current consensus such as PoW, PoS, DPoS,PBFT[1-5], are very limited for variant consensus supporting, such as PoW is low efficient for mining, while PoS is not still not so high performance for transaction confirmation.Current blockchain should considering more practical and efficient consensus for high TPS and DAPPs[12-17].
III. THE PROPOSED MASTER-SLAVE BLOCKCHAIN SCHEME
3.1 The proposed master-slave blockchain model
Upon flaws of current blockchain platforms of heavyweight, large capacity of ledger, and time-consuming of synchronization of data,in this paper, we proposed a new paradigm of master-slave light-weight blockchain architecture(MSB) for pervasive computing that suitable for general PC, mobile device such as smart phones or PADs, in which we separated traditional blockchain model into master-slave model, in which the master node responsible for transaction collection, computing task distribution, and the slave agents responsible for independently computing and commit result to the master node. The slave computing device may be personal computer, mobile phones.The master-slave blockchain model is described as follows in figure 1, which showed a hierarchical model of master-slave blockchain computing paradigm.
3.2 The master-slave blockchain architecture
In the master-slave blockchain scheme, we proposed 2 approaches for partially computing model(PCM) and non-computing of model(NCM) in the MSB blockchain, and in the PCM blockchain model we proposed the consensus defined as proof of equivalent work(PeW), and in NCM, we proposed proof of contribution(PoC). In PCM model, as for a given amount of transactions, the master node dispatches partial computing task(includes but not limited difficulty, timestamp, hash, and version et.al parameters) to the slave agents for distributed computing with high concurrency, when the slave agent computed and found the Nonce that satisfied the mining condition, once the result of the Nonce is verified as true for the partially computing, then the master node gives a reasonable reward to the slave agent.
And in NCM model, the master node works directly as usual, but it related a series of slave agent for service-related contribution such as providing advertisement, service flow, page view(PV), unique visitor(UV), visit view(VV),independent IP address(IP), when the master node works and gains the rewards from the whole blockchain network, then it distributes rewards to the slave agents according to their service related contribution(PoC). Finally we evaluated the MSB scheme based on Bitcoin system, large amounts of simulations manifest the proposed MSB scheme is feasible, extendible and suitable for pervasive computing, the master-slave blockchain architecture is described as in figure 2.
IV. SECURITY INFRASTRUCTURE OF MSB BLOCKCHAIN SCHEME
As for the blockchain technology, SHA256,SHA3, RIPEMD160 and ECC-based public cryptosystem ECDSA are the infrastructure of the security algorithms[24-28]. and the public address of most blockchain is based on BASE58. Such as in Bitcoin, the ECC algorithm in blockchain system uses secp256k1 elliptic curve which is different to the standard ECDSA[26-27].
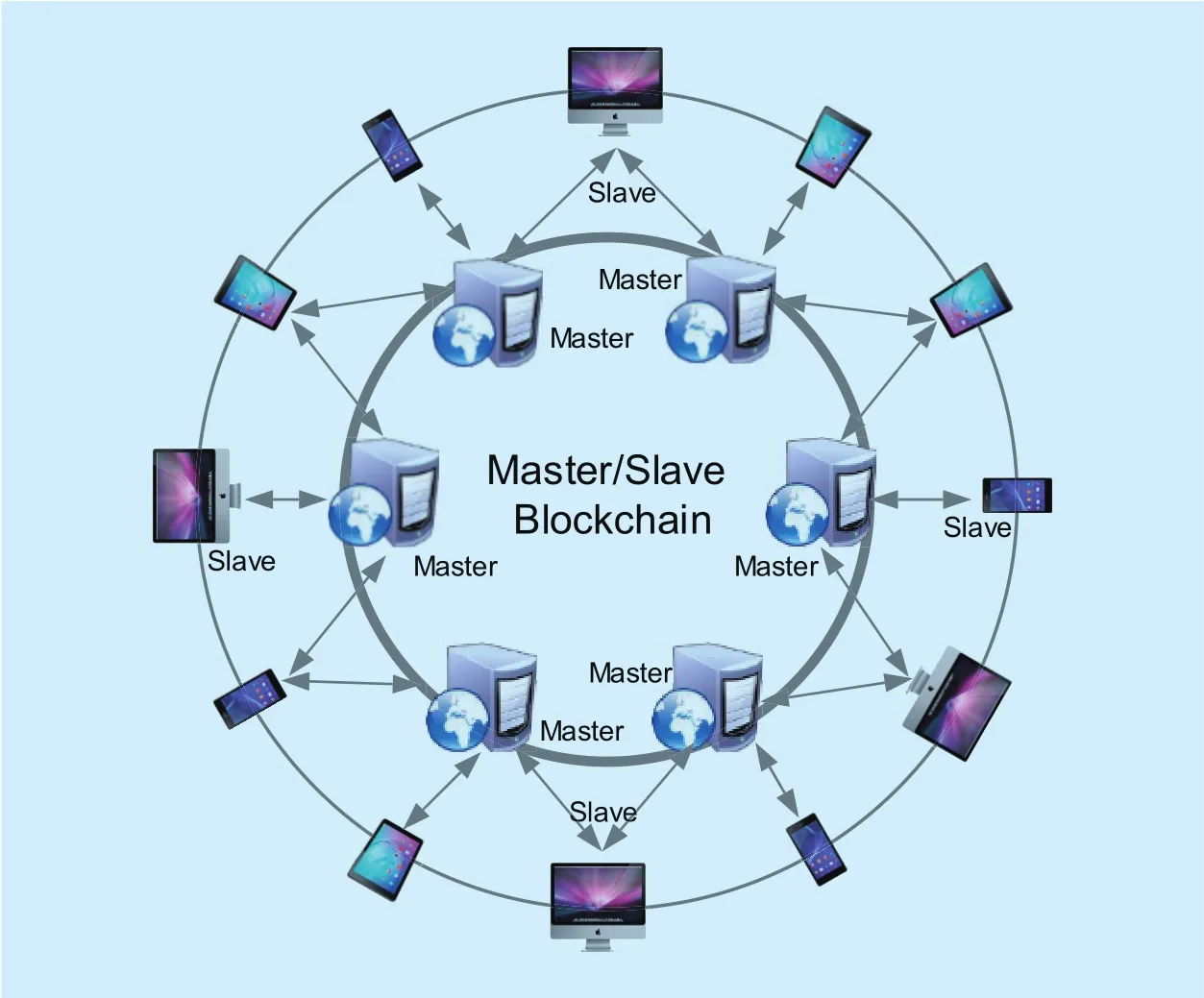
Fig. 1. The master-slave blockchain model.
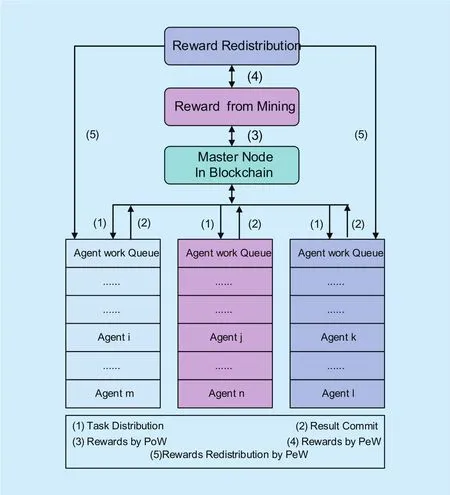
Fig. 3. The master-slave blockchain execution procedure.
V. MASTER-SLAVE BLOCKCHAIN EXECUTION AND CONSENSUS
5.1 Master-slave blockchain execution process
In the PCM blockchain model we proposed the consensus defined as proof of equivalent work(PeW), and in NCM, we proposed proof of contribution(PoC). In PCM model, as for a given amount of transactions, the master node dispatches partial computing task(includes but not limited difficulty, timestamp,hash, and version et.al parameters) to the slave agents for distributed computing with high concurrency, when the slave agent computed and found the Nonce that satisfied the mining condition, once the result of the Nonce is verified as true for the partially computing, then the master node gives a reasonable reward to the slave for the computing of the slave computing work(PeW). And in NCM model,the master node works directly as usual, but it related a series of slave agent for service-related contribution such as providing advertisement, serviceflow, page view(PV), unique visitor(UV), visit view(VV), independent IP address(IP), when the master node works and gains the rewards from the whole blockchain network, then it distributes rewards to the slave agents according to their service related contribution(PoC). The master-slave blockchain execution process is described in figure 3.
5.2 New Consensus of master-slave blockchain scheme
The main consensus mechanisms[19-21]include proof of work(PoW), proof of stack(-PoS), distributed POS(DPoS) and practical Byzantine Fault Tolerance(PBFT), other consensus mechanisms include Paxos, Raf, which can satisfy different applications of blockchain scenes.
In the proposed MIB consensus, we proposed proof of equivalent work(PeW), proof of contribution(PoC):
5.2.1 Proof of Equivalent Work(PeW)
In the Proof of equivalent work consensus, the mobile internet agent computes the Nonce as partial computing unit in the slave side.
(1) PeW Algorithm of MIB Slave User-Agent AID[i]
Input: AID, y0= T0, blockHeader
where,
T0is the target difficulty value
blockHeader is composed as follows:

Output: Nonce
(1) the slave mobile internet UserAgent AID node computes:
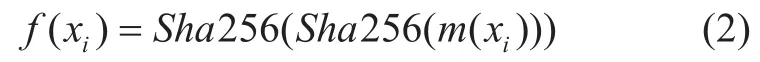
(3) Then AID node stops to compute, and set to Ni
AID set: Nonce=xi
(4) AID node signs the Nonce as follows:
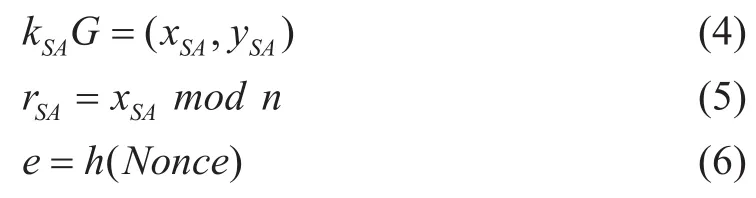
(2) if the condition is satisfied:

That is:
Then the server B computes:
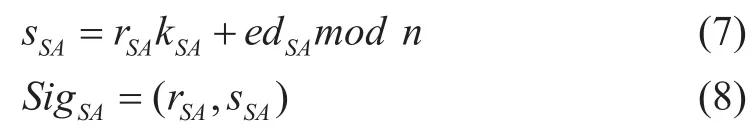
(5) Finally, the Slave Agent AID return Nonce and its signature SigSAto master node;
(6) End.
(2) PeW Algorithm of MSB Slave Agent AID[i]
Input: AID, Nonce, blockHeader,
where,
T0is the target difficulty value
blockHeader is composed as follows:

Ni, the nonce as the goal value for mining.
Output: blockHeader, blockBody, Rsuccess,RunSuccess
(1)After received the Nonce Ni, then MIB Master Node
f
i rstly verifies the validation of the Nonce.
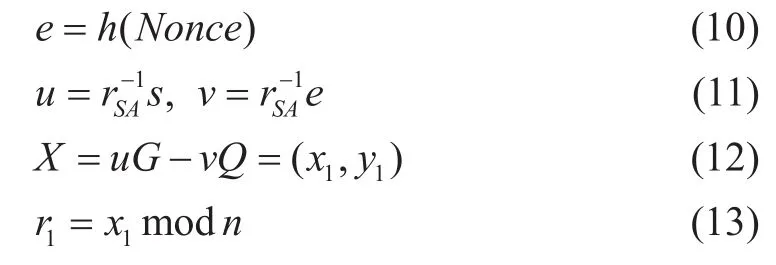
If r=rSAit manifests the signature is true.
(2) The MIB Master Node broadcasts the block data to all candidate blocks to verify its correctness and validity. Generally, supposing that there are M0blocks participant the verifying and the verification result is true, that is :

if all the bVeriResult[i] is true, i.e:

(3)The MIB Master Node constructs and outputs:

(4) The MIB Master Node then constructs :

Where
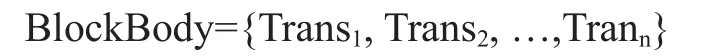
(5) The MIB Master Node dispatches Reward to the successfully mining or verifying Agent AID[i]:
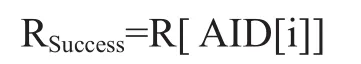
(6) To encourage those who participate the working of mining or verifying agent, the MIB Master Node still give reward to the Successfully mining AID[j](i!=j)

where(CPF means contribution Percentage Function)
t is the time the AID[j] took for the working of mining or verifying.
freq is the frequency of the AID[j] working.
eff is the efficiency value of the AID[j]working.
Then MIB Master Node gives thefinal rewards R as above:
(7) End.
5.2.2 Proof of contribution
In the non-computing of model(NCM), the master node works directly as usual, but it related a series of slave agents for service-related contribution such as providing advertisement, serviceflow, page view(PV), unique visitor(UV), visit view(VV), independent IP address(IP), when the master node works and gains the rewards from the whole blockchain network, then it distributes rewards to the slave agents according to their service related contribution, we defined the consensus as proof of contribution (PoC).
(1) Definition of PoC Algorithm in the non-computing of model(NCM)
Definition: Proof of Contribution(PoC)is the consensus algorithm that supports for non-computing model in master-slave blockchain environment, the reward and the consensus is defined as following the compound function f:
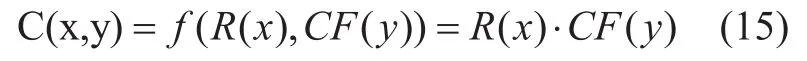
Where R(x) and CF(y) represent the reward function and control factor function:
And the parameters in R(x) represent service flows, which include page view(PV),unique visitor(UV), visit view(VV), independent IP visiting(IP), advertisement hit(AH).Generally, the parameters often has the following relationship:
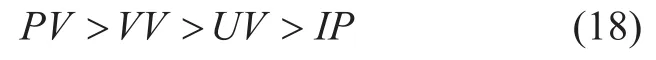
While the CtrlFactor(y) represents the control factor function to control invalid or deliberate cheating behavior, the PoC consensus function C(x,y) is defined as the following formula:
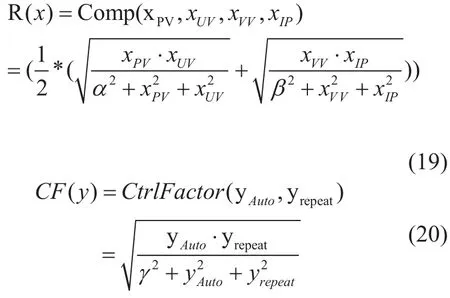
As the parameters such as page view(PV),unique visitor(UV), visit view(VV) are natural numbers, thus the factors α, β, γ parameters is defined as natural number,then there exists the following property of PoC:
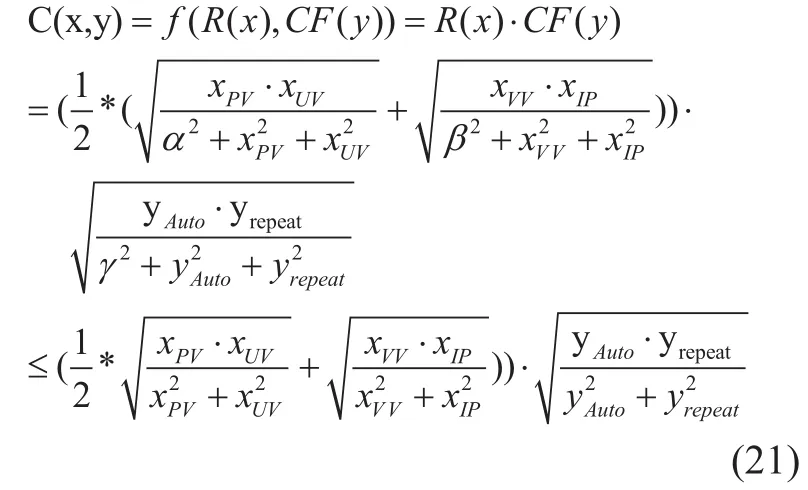
Then in the proof of contribution consensus(PoC), we can give proper reward as the above definition. And in real application system, it is reasonable and fair for different users to visit and contribute to the service-related system.
(2) PoC Algorithm in the non-computing of model (NCM)
Input: user behavior vector R(x) and R(y)to the destination objects as defined as the above definition.
Output: The contribution awards share C(x,y) to the user
(1) the system daemon monitors and records each client’s behavior, the system counts each parameter in R(x), which includes page view(PV), unique visitor(UV), visit view(VV),independent IP visiting(IP), advertisement hit(AH).
(2) For each parameter of R(x), the system counts and calculates the summary of the specific time period(such as a day):
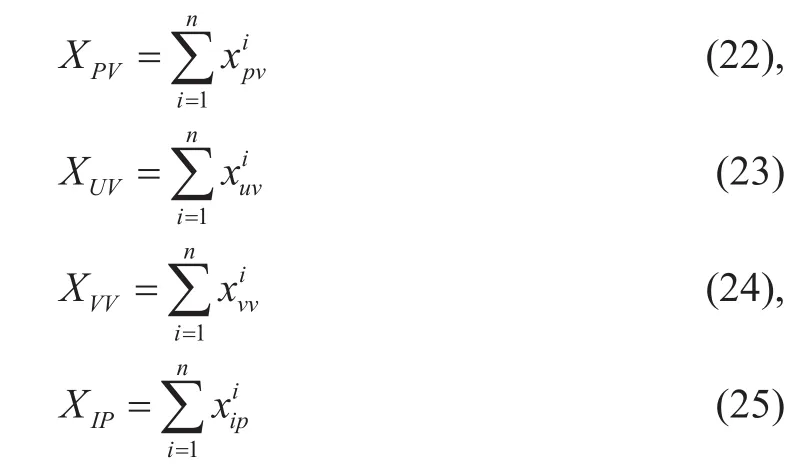
(3) For each parameter of R(x), the system merge the repeat parameter as one valid behavior:
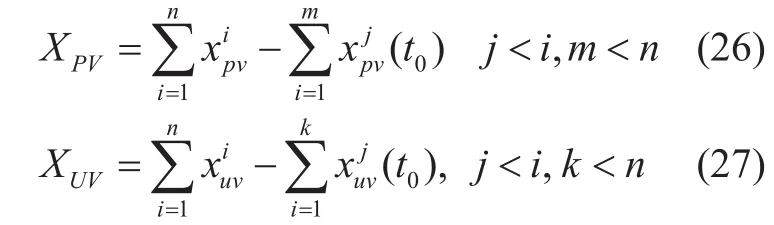
In which t0is the specific time window,such as in 10 minutes the system monitored a user accessed the specific page view 100 times, which is obviously a machine behavior,then the PV counter should be NOT accepted in the system.
(4) Not only the repeat counter such as PV or VV should be viewed as invalid, and the system should punish the machinery automatic behavior as follows:
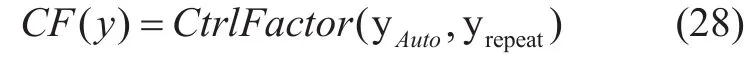
Where yautoand yrepeatrepresents the the machinery page view (PV) counter and visit view( VV) counter.
(5) The system then calculates the contribution as follows:
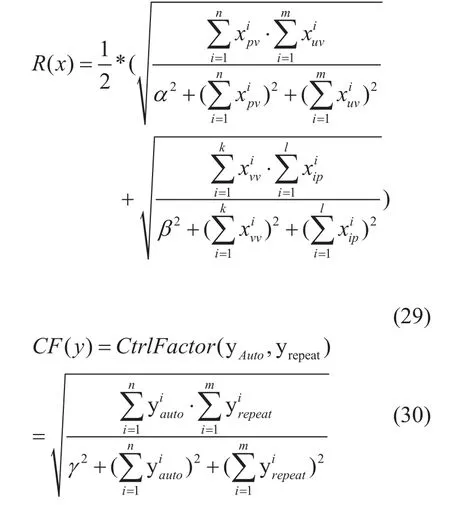
In the above R(x), the parameters xpvand xuvis the valid counter that had be dealt without machinery automatic behavior.
(6) Then the final reward contribution is computed as:
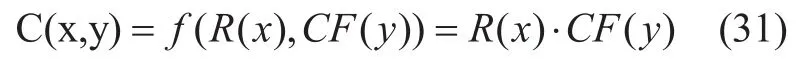
(7) Finally, the system returns the C(x, y) as thefinal contribution reward for the proof of contribution(PoC).
5.3 Blockchain management and reconstruction
When the master-slave blockchain procedure is verified as valid, then when constructing the correct block in the whole blockchain system, the blockchain management includes for 4 stage operations: (1) download blockchain data;(2) receive blockchain data;(3) verify the blockchain data; (4)reconstruct bllockchain.
5.3.1 Whole blockchain data downloading
When the node first runs the blockchain network, it need to download the whole blockchain data. The efficient stratagem of the blockchain download is headerfirst, that is the systemfirstly download the block header(only 80bytes), when download all the blockheader, then the system can download the whole blockdata from different peers in P2P network.
5.3.2 Blockchain receiving
After downloaded the blockchain data from peers, then the current node will load the whole index from LevelDB,which may be a tree rather than a single chain, that is each block has only one parent block, but has more than one sub-blocks.
5.3.3 Blockchain verification
Once the node first runs the blockchain network, it need to download the whole blockchain data. The efficient stratagem of the blockchain download is headerfirst, that is the systemfirstly download the block header(only 80bytes), when download all the blockheader, then the system can download the whole blockdata from different peers in P2P network.
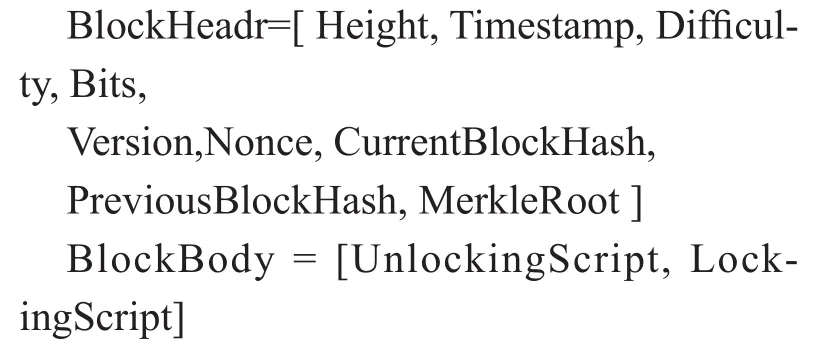
As well known, the blockchain data structure of the block data is listed as follows:
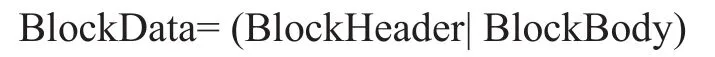
where the
1) Then the peerfirstly verify the data in-tegrity and the correctness of data format.
2) The blockchain peer transfers the blockdata to the receiver and signs the block as follows:

And then the peer computes:
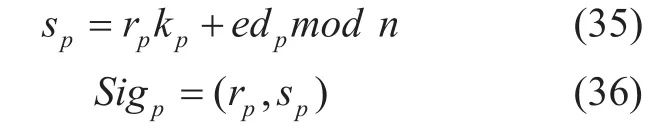
3) each other peer received the blockdata,and can verify the correctness as follows:
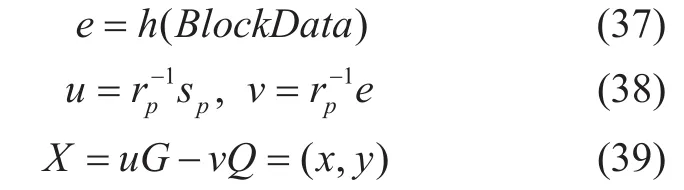
The signature is valid if and only if the following formula exists:

In fact, it’s easily to verify that the signature is valid in and only if the following equation is correct:
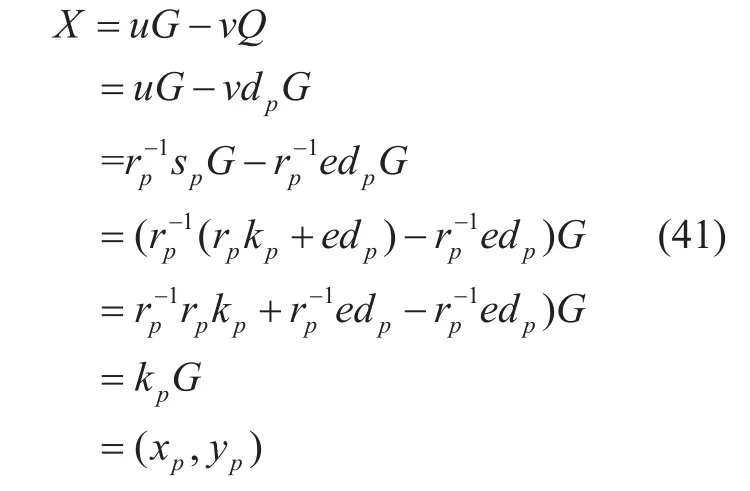
Then there must exist:

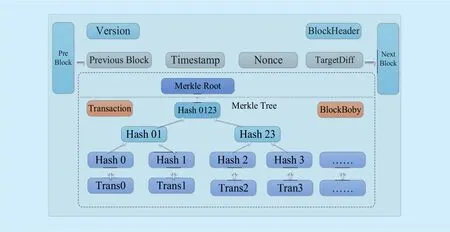
Fig. 5. The Blockchain block and transaction data structure.
Thus its manifests the peer verifies the signature of the blockdata as true, then the blockchain management system then check the transcation is a UTXO or not.
5.3.4 Blockchain reconstruction
When the peerfinds a longer chain than current exist chain, it needs to reconstruct the blockchain, most reconstruction is just for one block data reconstruction, only occurs when different miners computes the same valid block.
5.4 Block and transaction data construction
After pass the verification, the blockchain platform then build Up the blocks and transactions in time-order with tamper-resistance and security, the block data and transaction data is constructed and included block header and block body. The blockchain will permanently stores the data in the P2P network and cannot allow it be modified or deleted in a tamper-resistance mode, which can provide strong and high level reliability and security. Even some blockchain nodes deliberately announced or the nodes truly corrupted, the most other nodes can provide strong and trusted service for evidences. The block and transaction data structure are defined as bellows which is easy to convert to JSON format. The blocks and transaction data are organized in figure 5 and figure 6.
In the master-slave blockchain mode, the slave agent only acts as the light-weight client of computing nodes, which computes andfinds the proper nonce that satisfy the condition, thus gets the rewards according to the consensus methods such as proof of equivalent work or proof of indirect contribution.
VI. EVALUATION OF MASTER-SLAVE BLOCKCHAIN SCHEME
6.1 Evaluation environment of master-slave scheme
To evaluate the availability and efficiency, we built up the master-slave blockchain simulation environment based on Bitcoin v0.10.99.0-unk, in which we simulated the task redistribution thread and receiver thread from slave agents, and when the slave agents received the computing task(including mining computing and verification computing), then do the computing work according to the related computing parameters. The master-slave blockchain simulation environment is listed as table1.
We deployed 4 master nodes and each nodes serves 3 slave agents include general personal computer, android mobile phones and Pads for task receiving and computing and verification.
6.2 Experiments of master-slave blockchian scheme
In the deployed 4 bitcoin blockchain system,the master-slave bitcoin platform, we used variant kinds of PCs. Android mobile phones or Pads joined into to 4 master nodes, and then evaluated the performance and scalability of the master-slave blockchain scheme. The simulation of master-slave blockchain parameters are listed in table 2-3, algorithm 1 is the genesis initialization in CMainParams function, algorithm 2 is the blockchain data created from genesis block.
6.3 Simulation results of masterslave scheme
Figures 7-9 are the simulation results of the master-slave blokchain computing model.Figure 7-8 are the PeW consensus simulations in one master node and 3 slave nodes computing performance comparison, and figure 9 are the simulation results of PoC, in which α,β,γ were parameterized as 1, 2,3, to simply the whole computing complexity, in the serial data set S1, α,β,γ are parameterized as α=β=γ=1,and in serial data S2, α=β=γ=2,finally, in S3,α=β=γ=3. The results showed reasonable reward rate for variant contribution in PoC.
6.4 Simulation analysis of masterslave scheme
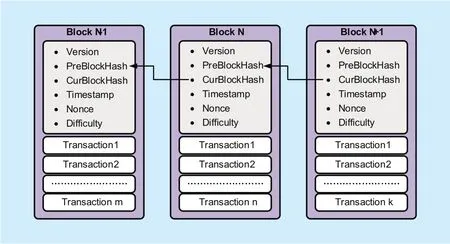
Fig. 6. The general data structure of blockchain(Bitcoin).
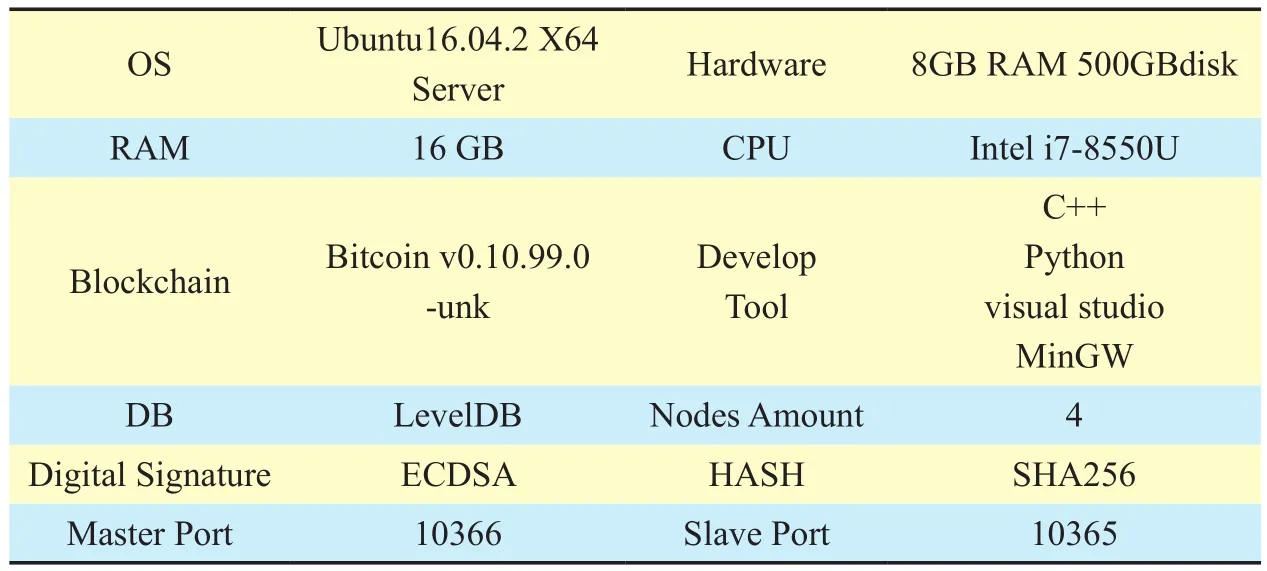
Table I. Development environment parameters.
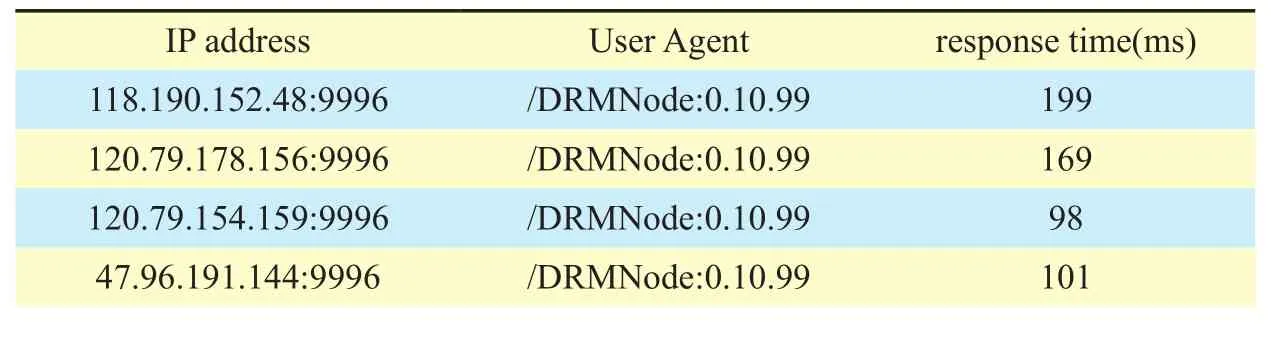
Table II. The network parameters of master nodes.
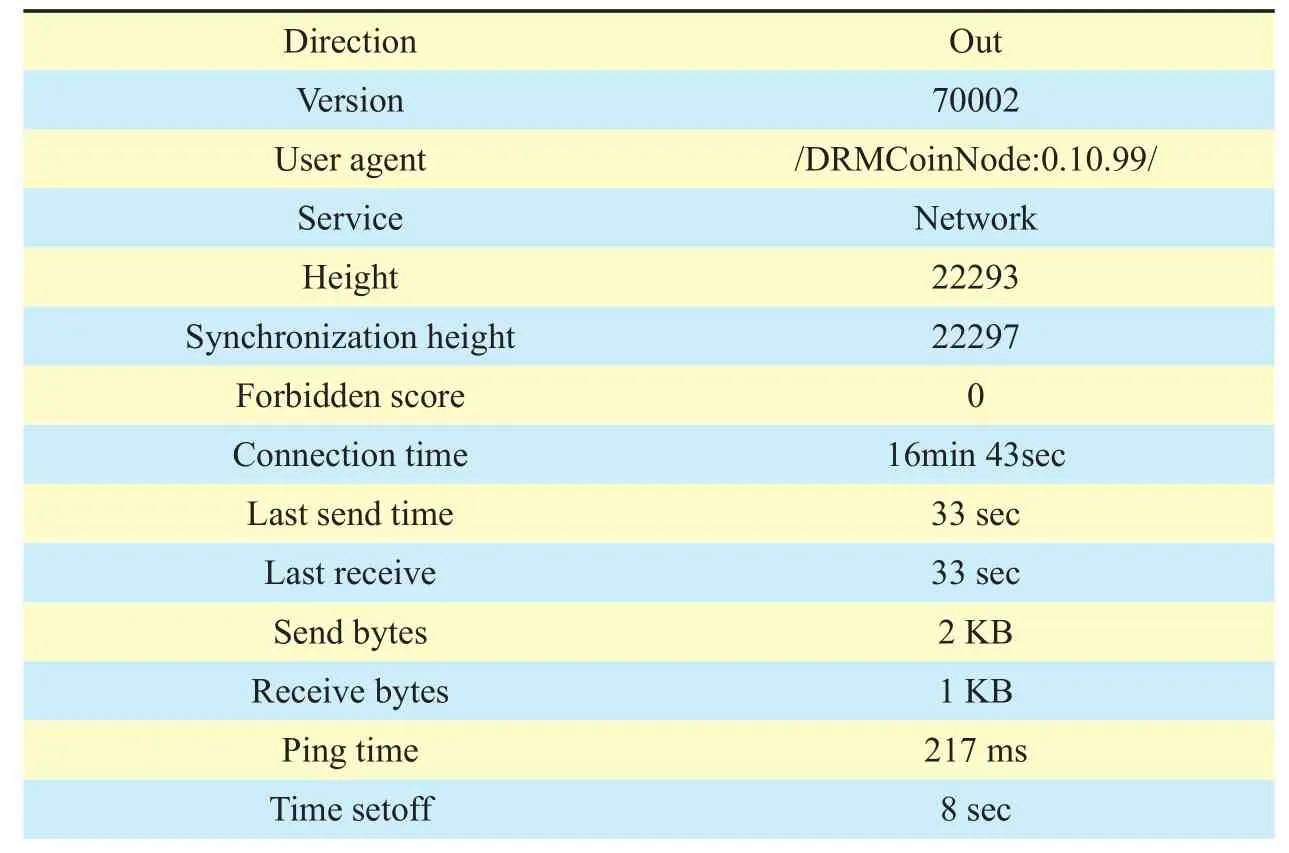
Table III. The peer node network status in master-slave platform.

Algorithm 1. The genesis initialization in CMainParams function.
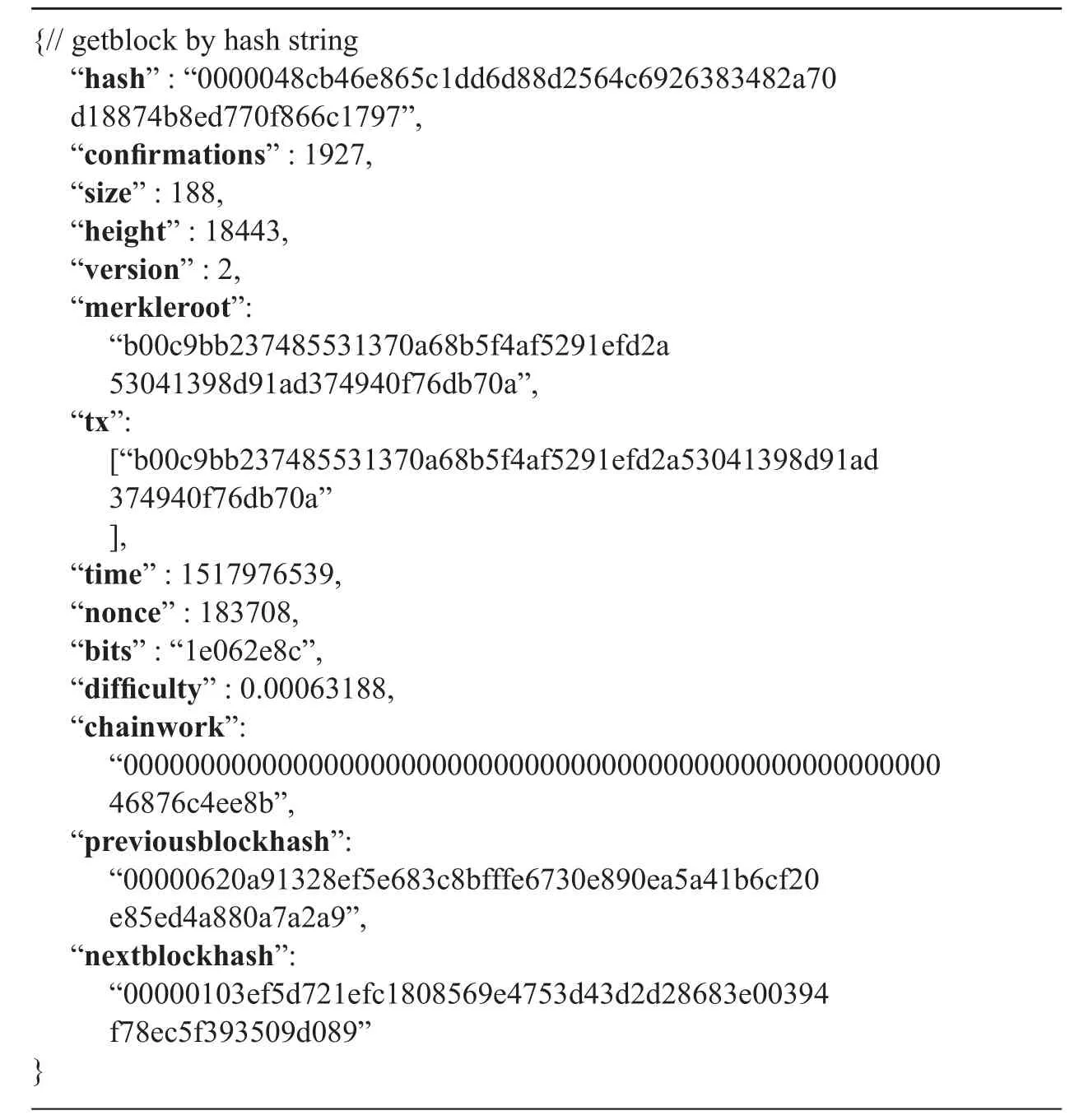
Algorithm 2. The blockchain information created from genesis block.
The simulation results of figure 7 and figure 8 reflex the master and slave node(s) computing resource occupation(CPU), of which the mobile phone’s CPU occupation is 25.17-28.21%, and the average value is 26.36%, and the pad CPU usage rate is 22.18-24.93%, and average percentage is 23.36%, while the PC slave node’s occupation is 18.21-20.03%, and the average rate is 19.05%, based on which we can found that with the hardware computing performance decreasing, the master node need much more computing CPU for the collection and waiting for the slave nodes to commit the computing and verification results.
While in PoC, it is easily found, that with the parameters α,β,γ increasing, the average reward rate declined from 41.53%, 40.11%, to 38.85%, this indicated that if we want to give the salve node a less reward we can parameterized α,β,γ to a large value, thus the reward rate can be reduced to a reasonable level.
VII. ANALYSIS OF MASTER-SLAVE BLOCKCHAIN SCHEME
7. 1 Availability of master-slave blockchain
The DRMChain Scheme provides a flexible DRM approach that enables user-controlled encryption but administrator and auditor can decrypt and audit the content once the released content is suspected violation or illegal usage,in the scheme, we proposed 3 parts control model trusted and creditable content encryption, secure key management, multi-signature for violation appraisal.
7.2 Consensus of master-slave blockchain
The proposed master-slave blockchain scheme allows variant computing device such as personal computer, mobile phones, or Pads can join into the blockchain computing and get reasonable rewards according to their work or contribution, the proposed proof-of-equivalent(PeW), and the proof-of-indirect-contribution(PIC) innovated the existing consensus of blockchain, and are effective and efficient
mechanism that can attract more persons joint into the blockchain system without large capacity ledger data synchronization.
7.3 Extendibility of master-slave blockchain
With the proper connection mode such as the mining pool for cluster computing in Bitcoin,the master-slave blockchain scheme innovates the blockchain paradigm that develops the heavy-weight blockchain to light-weight layered computing mode, which can dispatch different work to slave agents for discrete time usage of mining task balance or indirect contribution for blockchain useful utilization without synchronize blockchain data synchronization.
VIII.THE MASTER-SLAVE BLOCKCHAIN APPLICATION IN DRM
Digital content service is mainly occupying the bandwidth rather than the computing resource, upon which the proposed master-slave paradigm is very suitable for digital right management of content service. The proposed PeW and PoC consensus is a reasonable method for DRM-related applications[19-22].
8.1 Scene of the PeW in DRM system
In the DRM service[19-20], when the user client daemon is idle or free time, the PeW consensus can be implemented in a master-slave mode to allow computing resource limitation device such as phones or Pads join in the partial computing work as slave, and the full-computing node organizes the valid computing piece as master, which can speed up the full-computing node for the mining work.With 5G network bandwidth and computing ability development, it’s a good and promise direction for PeW application in mobile Internet computing times. In the DRM servie,when the client daemon is free or idle, the PeW is efficient and secure for master-slave blockchain paradigm[20].
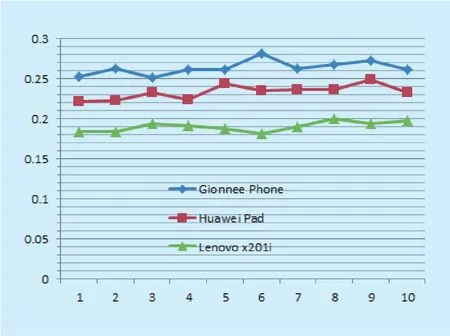
Fig. 7. The simulation of CPU usage of the master node in PeW.
Fig. 8. The simulation of CPU usage of variant slave nodes in PeW.
8.2 Scene of the PoC for DRM-based content view
As for the proposed blockchain paradigm, the proof of contribution(PoC) is suitable for user to visit or consume the content, once the user visit, preview, play, or share the content, the user should be encouraged, and should give the reward according to the user’s PV, UV,VV,or IP, and the valid sharing and the shared user’s valid consumption, the content service provider then gives the user an active blockchain-based digital currency reward, and the user can query the reward transaction in his/her account, which is very useful for sharing economy. Especially when using DRM[21-22]and blockchain technology for content service,it is easily implemented a blockchain-based new DRM content service, that the right content serves the right user in a right way with a right reward. The users can consume the content by digital currency, which either is he/she bought independently, or is granted as a reward by his/her contribution of consumption or sharing, thus PoC consensus is a classic application for DRM-based content service scene.
IX. CONCLUSION
The most useful contribution of the paper is that we proposed a new paradigm of master-slave blockchain scheme (MSB) for pervasive computing that suitable for general PC,mobile device such as smart phones or PADs to participants in the working of mining and verification, in which we separated traditional blockchain model in 2 layers defined as master node layer and a series of slave agents layer,and we proposed 2 approaches for partially computing model(PCM) and non-computing of model(NCM) in the MSB blockchain. Finally we evaluated the MSB architecture based on Bitcoin system, large amounts of simulations manifest the proposed MSB scheme is feasible, extendible and suitable for pervasive computing. The proposed PeW and PoC consensus is a reasonable method for DRM-related applications, and as the permanent research topic, performance and TPS enhance is the most important issues to be studied in the future work.
ACKNOWLEDGMENTS
This work was supported by the National Natural Science Foundation of China under Grant 61272519, the Research Funds of Blockchain Joint Lab between BUPT and BCT, and the joint Blockchain and Security Lab between BUPT and CAPSTONE.
- China Communications的其它文章
- A Stackelberg Differential Game Based Bandwidth Allocation in Satellite Communication Network
- Joint Resource Allocation Using Evolutionary Algorithms in Heterogeneous Mobile Cloud Computing Networks
- The Coevolutionary Relationship of Technology,Market and Government Regulation in Telecommunications
- Mobile Jammer-Aided Secure UAV Communications via Trajectory Design and Power Control
- A Quantitative Security Metric Model for Security Controls: Secure Virtual Machine Migration Protocol as Target of Assessment
- A Blind Spectrum Sensing Based on Low-Rank and Sparse Matrix Decomposition

