An MAC Layer Aware Pseudonym (MAP) Scheme for the Software De fined Internet of Vehicles
Zishan Liu, Li Zhu,*, Jianwu Li, Guiyang Luo, Lin Zhang
1 Key Lab of Universal Wireless Communications, Beijing University of Posts and Telecommunications, Beijing 100876, China
2 China Transport telecommunications and information Center, Beijing 100009, China
2 People’s Public Security University of China, Beijing, China
3 China Center for Information Industry Development Institute of Cyber-Space NO.27 Wanshou Road, Beijing 100846, China
4 State Key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications, Beijing, China
Abstract: This paper proposes a cross-layer design to enhance the location privacy under a coordinated medium access control (MAC)protocol for the Internet of Vehicles (IoV).The channel and pseudonym resources are both essential for transmission efficiency and privacy preservation in the IoV. Nevertheless,the MAC protocol and pseudonym scheme are usually studied separately, in which a new MAC layer semantic linking attack could be carried out by analyzing the vehicles’transmission patterns even if they change pseudonyms simultaneously. This paper presents a hierarchical architecture named as the software defined Internet of Vehicles (SDIV).Facilitated by the architecture, a MAC layer aware pseudonym (MAP) scheme is proposed to resist the new attack. In the MAP, RSU clouds coordinate vehicles to change their transmission slots and pseudonyms simultaneously in the mix-zones by measuring the privacy level quantitatively. Security analysis and extensive simulations are conducted to show that the scheme provides reliable safety message broadcasting, improves the location privacy and network throughput in the IoV.
Keywords: IoV; software defined network(SDN); location privacy; MAC protocol;cross-layer design
I. INTRODUCTION
The 5G technologies have envisioned the Internet of Vehicles (IoV) that support the vehicle-to-vehicle (V2V), vehicle-to-infrastructure(V2I), vehicle-to-pedestrian (V2P), and vehicle-to-cloud (V2C) communications, i.e., vehicle-to-everything (V2X) communications. The 5G’s unique technologies such as the software defined network (SDN) [1], [2] and cloud/fog computing and processing [3] are expected to integrate into the IoV framework. Since the numerous messages provide rich information about the vehicles’ locations and enable the tracking of them, it is of practical significance to protect the location privacy in the IoV.
Recently, standardization bodies such as IEEE 1609.2 [4] and ETSI [5], have applied the public key infrastructure (PKI) based pseudonyms to represent the short-lived public keys of each vehicle. Pseudonyms need to change frequently and appropriately [6], [7],[8], so that the messages originating from the same vehicle are unlinkable to prevent the continuous tracking from the adversary.
The applications and services in the IoV impose certain quality of service requirements, the other challenge could be the design of an efficient medium access control (MAC)protocol for the provision of the transmission requirements for the various applications. Unfortunately, the dilemma between pseudonym changing and channel accessing arises in IoV.E. Fonseca et al. [9] pointed out that the identifiers of other layers, e.g., the IP address and MAC address must be changed consistently with the pseudonyms. Although previous work has considered the cross-layer influence on the pseudonym changing, the MAC layer and pseudonym schemes are designed separately,which brings new location privacy threat and transmission degradation.
The dedicated short range communication standard employs the IEEE 802.11p [10] that is based on the carrier sensing multiple access (CSMA) for the channel accessing. Prior studies [11], [12] have shown that the CSMA operation is only suitable for low-to-moderate traffic scenarios. As the safety messages are required to broadcast periodically by each vehicle, the time division multiple access(TDMA) based schemes have become one of the promising candidates for IoV. By letting each vehicle report their sense on the status of all the time slots [13], [14], [15], the TDMA approach can alleviate the hidden terminal problem. The distributed TDMA based protocol, VeMAC [13] assigns disjoint sets of time slots to vehicles moving in opposite directions,so as to reduce the transmission collisions caused by vehicle mobility. Later, we propose the TDMA based sdnMAC [16], [17] protocol in the software defined vehicular network to support the cooperative safety.
With the development of SDN and cloud computing, ultra-dense deployment of the RSUs enable the local clouds to cooperatively coordinate the channel resources [17] and manage the pseudonyms for the vehicles [18].However, the more coordinated, the more likely to facilitate the MAC semantic linking attack by taking the transmission and resource allocation context as the “ fingerprint” to link the vehicles’ old and new pseudonyms. For example, in VeMAC, the disjoint sets of the transmission slots for vehicles moving in opposite directions reveal their driving directions. Meanwhile, the pseudonym changing introduces negotiation and cooperation overhead, which degrades the safety message transmissions. To the best of our knowledge,it still lacks a protocol to resolve the operation inconsistency between the MAC layer and pseudonym schemes in the SDN based IoV.
In this paper, we present a hierarchical architecture named as the software defined Internet of Vehicles (SDIV) where the multi-channel transmission and pseudonym management are coordinated by the RSU clouds. Facilitated by the architecture, an efficient MAC layer Aware Pseudonym (MAP) scheme is proposed to deal with the new MAC layer semantic linking attack. Specifically, the main contributions of the paper are three-fold.
? We identify the new MAC layer semantic-linking attack caused by the inconsistent operation of the pseudonym scheme and MAC protocol.
? We present a three-layer SDIV architecture,in which a MAP scheme is designed to schedule the MAC layer transmission with the pseudonym change by the local RSU cloud. The privacy level based pseudonym changing is formulated by the RSU cloud according to a composite location privacy metric that includes the pseudonym and slot age, anonymity set size and group confusion to deal with the new attack and improve the location privacy for the vehicles.
? Security analysis and extensive simulations are conducted to show that the MAP scheme significantly enhances the location privacy, and improves the transmission ef ficiency and reliability in the SDIV.
The rest of the paper is organized as follows. In Section II, we present the hierarchical SDIV system architecture, threat model and the new MA layer semantic linking attack.Section III introduces the MAP scheme. Subsequently, the security analysis and simulation results of the scheme are given in Section IV and V respectively. Finally, Section VI concludes the paper.
This paper proposes a cross-layer design to enhance the location privacy under a coordinated medium access control (MAC)protocol for the Internet of Vehicles (IoV).
II. SYSTEM MODEL
In this section, we introduce the proposed hierarchical SDIV architecture with some basic assumptions of the system and the threat model in the pseudonym scheme.
2.1 Software defined internet of vehicles (SDIV) architecture
Figure 1 shows the hierarchical SDIV architecture. It consists of three layers: central cloud layer, RSU cloud layer and vehicle layer. The management of the SDIV is two-tiers:the RSUs connect together according to the flow tables to manage the vehicles, and they are managed by the Controller in the central cloud layer. The de facto protocol, OpenFlow is applied as the communication protocol between the control plane and the data plane in the proposed SDIV. The OpenFlow switch in the data plane is equipped with wireless interface to communicate with both the vehicles and the Controller in the control plane. The details about the three layers are described as follows.
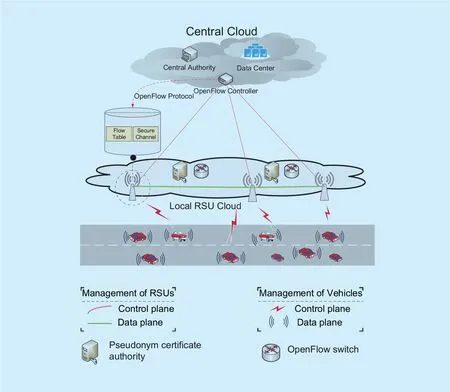
Fig. 1. The hierarchical SDN based IoV architecture.
? The vehicle layer is in the data plane of the SDIV. Each vehicle has at least one on-board unit (OBU) for the V2X communication, a global positioning system, and a temper-resistant device to store the cryptographic keys. The transmission range R is assumed to be the same for all the vehicles. The channel is symmetric, in the sense that vehicle Viis in the communication range of Vjiff Vjis in the communication range of Vi.
? The RSUs are supposed to fully cover the roads and connect together as the local cloud. For ease of exposition, we suppose that the distance between any adjacent RSUs is R. In the RSU cloud layer, the OpenFlow switches are equipped to communicate with the vehicles, and connect with each other and to the central layer through the secured wired connections.
? In the central cloud layer, the central authority (CA) has the responsibility for the bootstrap, certificate provision and revocation for the devices. Meanwhile, the Open-Flow controller is located in the control plane of the central cloud layer to control the RSU clouds.
2.2 Threat model of the SDIV
1) The global passive adversary (GPA) model:
In this paper, a GPA model [6] is assumed.The adversary only monitors and tracks any targeted vehicle by eavesdropping its messages without compromising the vehicle. The main motivation of the GPA is to track vehicles’ locations and driving paths, and thereby explore their lifestyles and sensitive information. The adversary is smart enough to carry out the syntactic linking attack and exploit the information contained in the received messages and the other layers’ context and activities,e.g, IP and MAC addresses and transmission cyclicality, to perform the semantic linking attack. We ignore the costly vision-based attack and active attacks, e.g, physical jamming attack, in this paper.
2) The MAC layer semantic linking attack
Previous work designs the MAC layer protocols and pseudonym schemes separately.Unfortunately, their inconsistent operations fa-cilitate the semantic-linking attack, by which the adversary can easily track a targeted vehicle by analyzing its transmission periodicity of the beacon messages. To formally describe the attack, we start by considering the tracking uncertainty of the GPA in a mix-zone.
The adversary A observes a set of N vehicles change pseudonyms simultaneously in a mix-zone at the time instant T. A compares the new set of pseudonyms with the old pseudonyms, and based on the mobility and other context information to predict the most probable linking. The adversary’s uncertainty on the linking of a tagged vehicle Viis denoted as Uiand computed as follows [20].
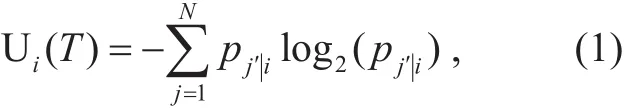
As the example illustrated in figure 2,at the first synchronized control channel interval, i.e., frame F1, the vehicles, e.g.,Bob, Alice and Grey use the pseudonyms x1, y1and z1to broadcast BSMs at time slot t2, t4and t6, respectively. The adversary can map the slot index with the current pseudonym of each vehicle, denote as. The vehicles change to the new pseudonyms x2, y2and z2at the frame F2simultaneously. Obviously, as the slot utilization and pseudonym changing operate inconsistently, the updated linking graph M2={(t2,x2),(t4,y2),(t6,z2)} links x1with x1, y1with y1and z2with z1, making makes Ui→ 0. Vehicles’ driving trajectories can be monitored continuously based on the messages transmitted at the specific time slots from the MAC layer.
III. THE MAC LAYER AWARE PSEUDONYM (MAP) SCHEME
MAP is a cross-layer scheme in which the RSU clouds coordinate vehicles to change pseudonyms and access the wireless channels in a contention free manner. Denote a representative vehicle as Viand its local RSU as RSUjto describe the MAP scheme. The interactive operation flow of a vehicle and the local RSU in the MAP scheme is illustrated in figure 3. For clear exposition, the primary notations are described in table I.
3.1 System initialization and basic key operation
In SDIV, efficient cryptographic schemes are generally compatible with the architecture. In this paper, we apply the Boneh-Boyen short group signature [21] for the key operation.Before Vienters the network, bootstrap and enrollment are required to obtain PKi, SKiand Certi, and the public key and certificate of RSUj, which are denoted as PKjand Certj, respectively. RSUjis assumed to cover the resident city of the driver. The CA stores the information {R IDi, P Ki, S Ki, C erti},and distributes to RSUjfor the tracking and revocation of Viwhen dispute happens.After registration, CA requests RSUjto distribute a set of pseudonyms and the corresponding private keys and the certificatesto Vi. Every time Vistarts a new trip, it checks whether it still has new pseudonyms, if not, it requests a set of new pseudonyms from RSUj. RSUjsends back the pseudonyms and records them in the tracking list of Vi.
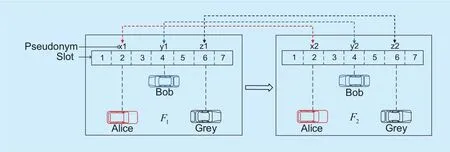
Fig. 2. The MAC layer semantic linking attack caused by the linking of the transmission patterns.
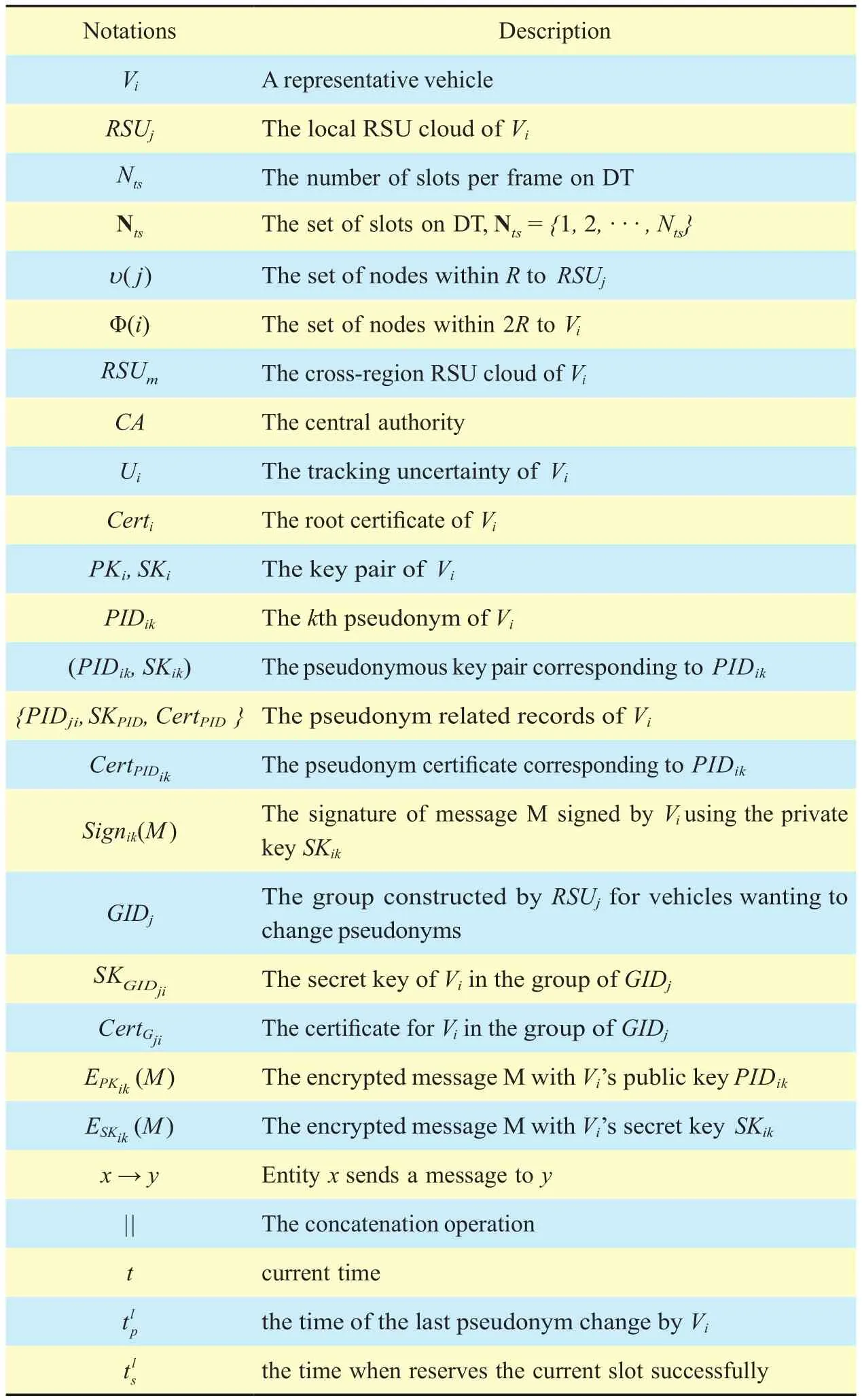
Table I. Notations used in this paper.
In order to prevent the semantic linking attack, the pseudonym changing should be accompanied by the identifiers of the other layers and the transmission slots. In MAP, the Cryptographically Generated Address (CGA)protocol is used to generate the new IP addresses from the new pseudonyms and to generate the MAC addresses from the generated IP addresses [22].
3.2 RSU cloud coordinated MAC layer operation
1)The synchronous channel resource scheduling
In MAP, time is divided into frames with 100ms, which is compatible with the synchronous interval specified by the Dedicated Short Range Communication (DSRC). There are four periods designed in each frame: a coordination period (CP), dedicated transmission period (DT), flexible period (FP) in the control channel (CCH) and the reservation period (RP) in the service channels (SCHs).As the RSUs can fully understand the position, direction and speed of vehicles within its communication range by listening to the safety messages and exchange information with each other, they cooperate to calculate the densities of vehicles and the optimal duration of each period. As illustrated in figure 4, when the traffic density is high, the duration of the DT and FP is increased to support more vehicles to broadcast the safety and request messages.When the traffic density is low, the duration of the control channel is reduced so that the resources on the SCHs could be utilized more efficiently.
The CP is used by the local RSU to broadcast the coordination information (CI) at the beginning of every frame to inform all the vehicles within its coverage. We suppose that the CI includes the slot status information (SI)in the DT period, the mix-zone construction invitation information and the scheduling information of the other periods.
The DT is time slotted for each vehicle to reserve at least one time slot to broadcast the safety messages periodically. Assume there are Ntsslots in the DT period, SIiis consisted of 2 bits to represent the status of the ith slot sensed by RSUjto the nodes with υ(j). Specifically, if tsiis occupied by a node within υ(j), SIiis set to “01”; if tsiis occupied by more than one vehicle within υ(j) that are possible to cause merging collision, SIiis set to “10”; if a transmission collision is perceived in tsi, SIiis set to “11”; in other cases, SIiis set to “00”.
In addition to the periodical broadcast of safety messages, vehicles dynamically transmit the encrypted pseudonym request or data service request to the RSU. The certificate revocation list is also needed to broadcast by the RSU to the vehicles. To separate the transmission of these occasional messages to the periodical safety messages, the CSMA based FP is applied. Vehicles contend to make reservation of the service channel secretly during the FP and then switch to the specific service channel during the RP to receive pseudonyms and data services from the RSU. As the number of vehicles increases, there will be more vehicles to transmit during the DT and FP. Thus, the interval of DT and FP are adjusted according to the vehicle density, so as to increase the channel utilization efficiency. The encrypted request information does not harm the user privacy and degrade the safety message transmission reliability. More details about the channel resources scheduling procedure are presented in Algorithm 1 and the three-way handshake approach is applied during the pseudonym and data service request procedure, which is described in Algorithm 3.
2) Vehicles’ channel accessing procedure:
When Vistarts a new trip, it firstly tunes to the control channel listening to the local RSUjand nearby vehicles periodically. It obtains the CI from the coordination message and randomly selects a time slot tsiwith SIi= “00” to transmit the safety messageto notify its existence to the surrounding nodes.
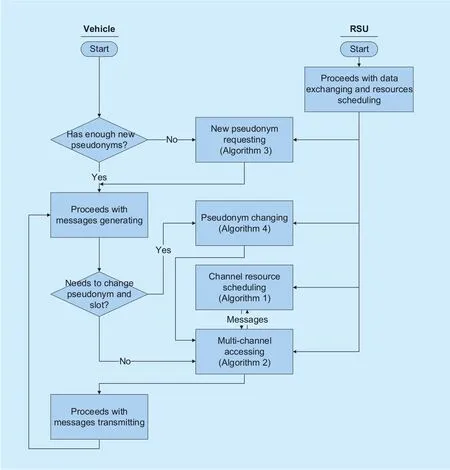
Fig. 3. The interactive operation flow of each vehicle and its local RSU in the MAP scheme.
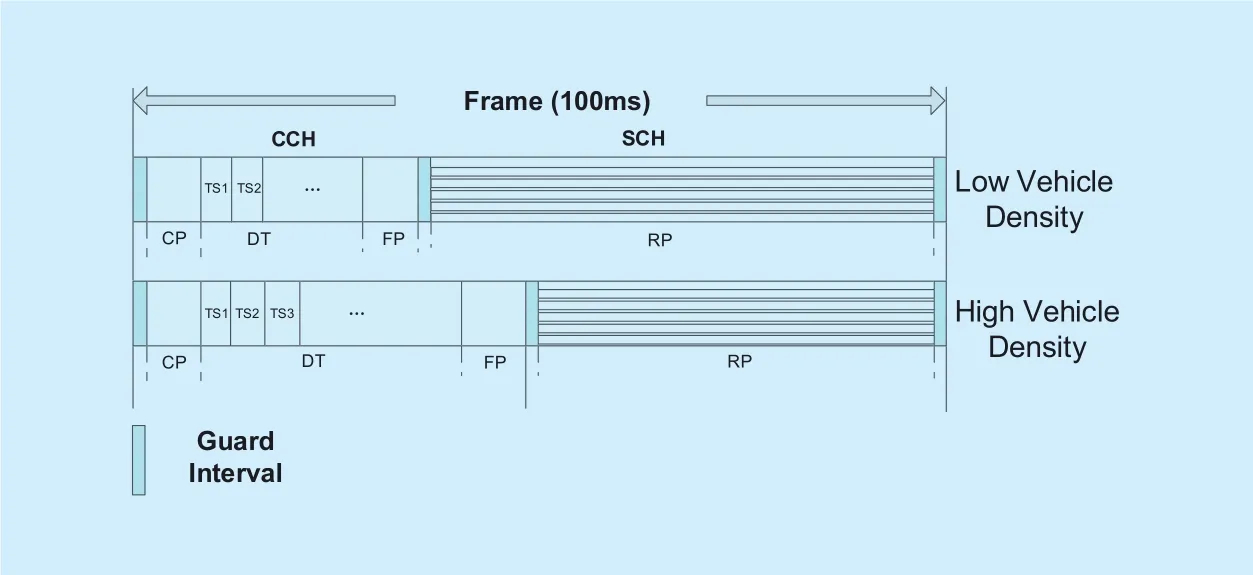
Fig. 4. The MAC layer frame structure in the MAP scheme.
After the reservation attempt, Vilistens to RSUjfor the updated coordination information. Viutilizes the slot continuously if it is notified the slot status is “01”, i.e., reserved successfully. If Vireceives the pre-collision warning about the slot, it utilizes the slot temporarily and transmits in a new slot with status“00”. After it reserves the new slot successfully, it will release the current slot. If a trans-mission collision happened, i.e., the slot status is set as “11”, it releases the time slot and reserves a new one slot with status “00”. The channel accessing procedure of Viis summarized as Algorithm 2.

?
3.3 Pseudonym request procedure
The vehicle Vihas to request new pseudonyms if it lacks enough pseudonyms to finish the trip. Vicontends to send the encrypted pseudonym request req, where the PseudoReq includes the number of requesting pseudonyms and privacy levels to define the expiry time for the pseudonyms. The RSU receives the request and verifies it according to the pseudonym record of Viin the local cloud. If Viis driving across the cloud region and the cross-region cloud RSUmdid not have a record, it requests the information of Vifrom RSUjand record it in its database,including {C erti, P IDi, S KPIDi,C ertPIDi}. Afterward, it sends back the reservation resn to assign Vithe service channel resource for the pseudonym reception during the RP. Visends back an acknowledgement to notify the RSU that it has successfully received the reservation information. During the RP, Vitunes to the assigned service channel to receive the new pseudonyms. After distributes the new pseudonyms successfully, RSUmupdates the record about Viwith the new pseudonym information, i.e., {P IDi, S KPIDi,C ertPIDi}. The pseudonym requesting procedure is presented in Algorithm 3.
3.4 The MAC layer aware pseudonym change
1) The privacy level metrics
To quantitatively determine when it is suitable for vehicles to change the transmission slots and pseudonyms, we propose a new composite privacy metric including the pseudonym age, anonymity set size and the group confusion.
? The anonymity set size ASimeasures the number of vehicles that changing pseud-onyms together in the mix-zone. When construct a mix-zone, the anonymity size should be large enough to make the vehicles mixing with each other, i.e.,ASi≥ ASth.
? The group confusion Giis proposed to evaluate the geo-indistinguishability of Vito the surrounding vehicles. During the pseudonym change procedure, Vi’s location information provides a clue for the adversary to carry out the semantic linking attack, while the nearby vehicles’ locations provide cloaking noise to the adversary if their locations are close enough. Based on the geo-indistinguishability concept [27],given the parameter ε∈R+, Gi≥ Gthis satis fied iff there exists at least another vehicle Vjin the proximity that satis fies:
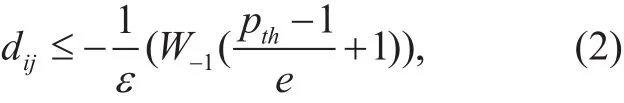
where dijis the Euclidean distance between Viand Vj, the RSU assigns a value to pth∈[0,1] according to the estimation of the adversary’s tracking capacity, W?1is the Lambert-W function. Since dijis a physical quantity expressed in the unit of meters or kilometers, ε needs to be updated in the inverse unit, so that εdijis a pure number.
2) Pseudonym change procedure
To change the transmission slots, MAP leverages the group signature for vehicles to construct the mix-zones. During the procedure of pseudonym change and resource scheduling, the group is given a group ID GIDj,which is used for vehicles to transmit in the mix-zone.

?
?
?
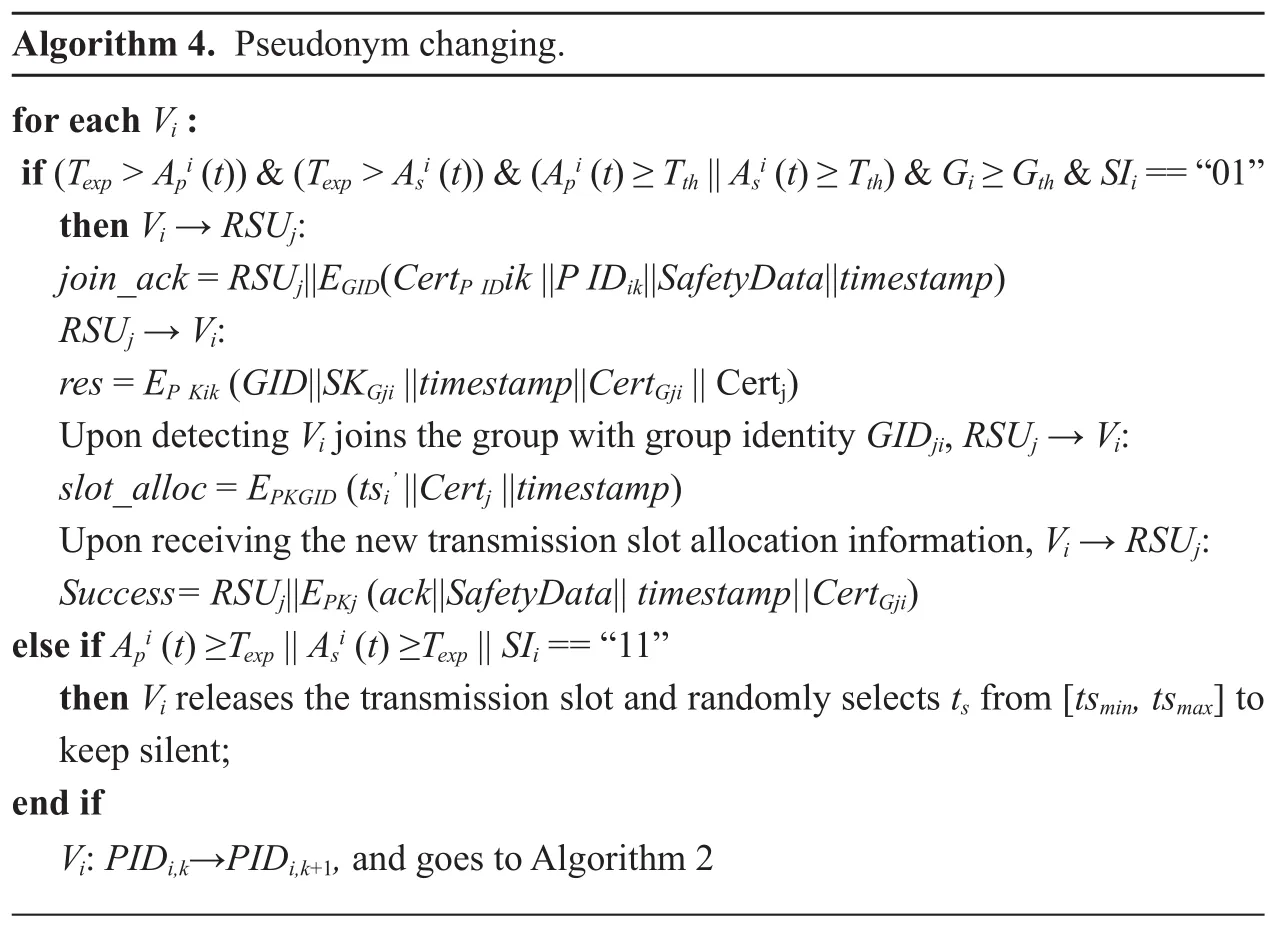
The pseudonym change algorithm includes the mix-zone construction, transmission resource and pseudonym change, mix-zone leaving, and new pseudonym and transmission slots utilization, which is described in Algorithm 4. The RSUs corporately to monitor the Ap( t ) and As( t) for each vehicle. Assume a set of vehicles, denoted as Nc, need to change pseudonyms and transmission slots, when either or both of Ap( t) and As( t) has been equal to or larger than Tthr. RSUjcalculates whether it is optimal for vehicles to construct a mixzone. If (Nc≥ ASth) ∧(Gi≥Gth,? vi∈ Nc) is satis fied, RSUjsets a mix-zone time window Tmand broadcasts the construction invitation to oblige vehicles to change the pseudonyms and time slots. Upon receiving the invitation and group identity, Vichecks its pseudonym and transmission slot age, and transmits the safety message by setting the join_ack as 1 in the header to indicate that it has accepted the request. Then the vehicle becomes one of the group members, and keeps silent in the next frame to let the RSU use its transmission slot to transmit the response. After RSUjreceives the join_ack transmitted by all the residing vehicles in the last frame, it firstly transmits the response in the new frame in each group member’s corresponding slot. RSUjshuffles the time slot allocation for the group members,and provides each of them the encrypted new time slot allocation (slot_alloc) information.After the group member has received the new time slot allocation information from RSUj,it broadcasts the success information to notify its success changing. Vehicles can join the group as long as the counter is not expired. To let all the group members change to the new time slots simultaneously, the RSU broadcasts the group _ leaving information after the construction time window expires. Each vehicle leaves the group by utilizing the new time slot and new pseudonym for safety message broadcasting. Until now, the pseudonym and time slots change procedure is finished.In some extreme scenarios, Vidid not change the pseudonym or time slot when the age is approach Texp, it releases the time slot and selects a random counter within [t smin,t smax]to keep silent. After the silent period expires,Viutilizes a new pseudonym to carry out the channel accessing procedure again.
IV. SECURITY AND EFFICIENCY ANALYSIS
4.1 Packet overhead evaluation
In this section, we analyze the efficiency and security properties of the MAP scheme. As described in Section IV, each coordination message include the header, the CI, the payload, the signature and certificate of the RSU.Accordingly, the length of the packet is calculated as follows.
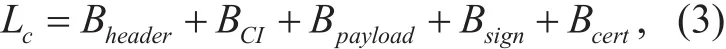
where Bheaderis the number of bytes of the header as defined in the DSRC standard, BCIdenotes the number of bytes required for the SI and the scheduling information. Bpayloadis the number of bytes required for the safety data,Bsignis the number of bytes required for the signature, Bcertis the number of bytes required for the certificate. Assume the number of the slots in the transmission period Nts=160 to support at least two-hop range vehicles under most congested scenario in which the number of vehicles is 80 under a 500m coverage range of the RSU. Thus, it requires 40 bytes to represent the slot status, 3 bytes is required to indicate the duration of the DT, FP and RP, respectively. Bpayload=53,Bsign=56,Bheader=19, Bcert=126. Therefore, the total length a BSM is 294 bytes. To evaluate the appropriate interval of the coordination period,considering the RSU can transmit using the largest transmission rate 27 Mbps supported by IEEE 802.11p, the transmission delay takes less than 0.1 ms, therefore coordination period is assumed to be 1ms. Similarly, the total length of a routine safety message is 254 bytes[10]. To evaluate the appropriate interval of a transmission slot, considering a mandatory supported transmission rate 12 Mbps for vehicles, the transmission delay takes less than 0.20 ms. The transmission and flexible period is flexible adjusted by the RSU cloud based on the local traffic density and mobility, so that not only the safety message transmission in the control channel is guaranteed, but also high throughput is provide in the service channels. The simulation results further prove the efficiency and reliability of the scheme in the next section.
4.2 Security and privacy analysis
The MAP scheme provides the message integrity, authentication, traceability and defend against various attacks through the standard cryptographic primitives including the asymmetric key-based encryption. With the help of digital signatures, all entities verify the digital signature to ensure the message integrity. With the certificate in the messages, the sender is authenticated and verified. The encryption mechanisms ensure that the adversary cannot open the encrypted messages by launching brute-force cryptanalytic attacks. The replay attacks would not be successful due to the usage of timestamp. Meanwhile, the adversary cannot simulate an RSU or forge the RSU messages as the RSUs are connected and controlled by the OpenFlow Controller by the central cloud. In order to defend against Sybil attacks, we consider that each pseudonym has an expiry time and the new pseudonyms are generated and distribute to the vehicles by the RSU cloud.
By defining the appropriate value of the pseudonym age and transmission slot age for the vehicles, they will change the pseudonym and slots within a safe-and-efficient span of time, neither too frequently nor too long.Meanwhile, the RSUs cooperate to determine the optimal mix-zone construction scenarios to so that the pseudonym changing is efficient and with large anonymity set size for vehicles.Furthermore, the group-confusion privacy metric is taken into consideration for the pseudonym changing of each vehicle, when constructing the mix-zones, it is hard for the GPA to continuously track a target as it cannot improve its posterior knowledge about the target based on its location information. All these vehicles look like the target vehicles if the vehicles with indistinguishable location information change their pseudonyms and transmission slots simultaneously in the mixzones. As a consequence, the time-to-confusion is constrained by the pseudonym age and the transmission slot usage duration. In contrast, if the MAC layer transmission is not considered when changing pseudonyms, the time-to-confusion could be unbounded by the pseudonym age as the MAC layer semantic linking attack facilitates the linking of the new and old pseudonyms of the targeted vehicles.
4.3 Performance evaluation and simulation results
In order to evaluate the performances of the proposed scheme, extensive simulations are conducted by considering a city grid layout scenario. It consists of 16 square city blocks in a 10 km2region. There are 9 large intersections deployed with RSUs that are connected together. The transmission range of the RSUs is assumed to be 500m and the transmission range of the vehicles is assumed to be 250m.Each street has two directions and vehicles with larger speed can go ahead of the vehicles with the lower speed. We assume when a vehicle reaches a junction area, it chooses on of all possible directions randomly. The vehicle located at an intersection can communicate with the vehicles at both directions near the intersection. The intersection range of each side is assumed to be 50m. The average number of vehicles within one hop set is assumed to be 10 to 100. Each vehicle moves with a constant speed drawn from the normal distribution and the number of vehicles on the system is kept constant during the simulation. Each vehicle is preloaded with 10 pseudonyms. The other simulation parameters as summarized in table 2.
We measure the average pseudonym age,anonymity set size and the time-to-confusion of MAP under different traffic densities.The pseudonym age starts to count when the pseudonym is utilized to transmit the first message. The pseudonym age thresholds are set as the recommended pseudonyms of the SAE J2735 [25] and European standard [5] respectively. To calculate the suitable group-confusion, the distance threshold for each vehicle Viis set as the average vehicle distance.
Considering the cross-layer performance,the packet delivery ratio (PDR) is used to verify the transmission reliability. The PDR of a vehicle is calculated as the total number of the safety messages that have been successfully transmitted within the lifetime to the total number of the safety messages generated by the vehicle. During a vehicle releases the old transmission slot and keeps silent before the new transmission slot reservation, the messages are assumed to be undelivered. When a vehicle encounters collisions or does not reserve a time slot or enters the silent period,the safety messages are also assumed to be undelivered. The transmission delay is an important metric in the measurement of transmission efficiency. While in the MAP scheme,safety messages are always broadcasted in thespecific transmission slots, thus the transmission delay in the MAC layer is bounded within 100ms. The performance of the MAP scheme is compared with the VeMAC and the IEEE 802.11p.
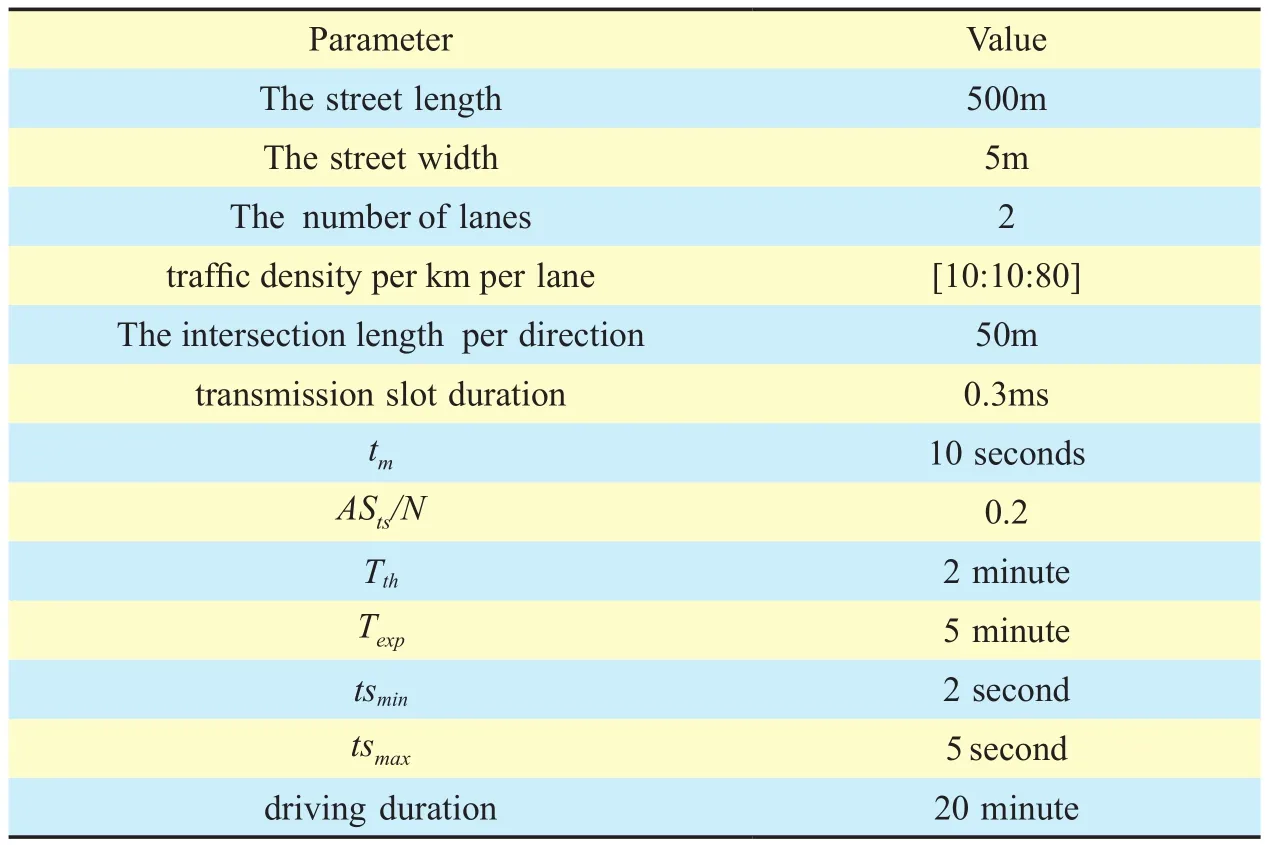
Table II. Parameter settings in numerical evaluation verification.
The privacy preserving performance of the MAP scheme is compared with the schemes without MAC layer operation awareness. In the first compared scheme, namely NMAP,vehicles decide to construct the mix-zones without considering the transmission slot usage condition as in MAP. The RSUs do not shuffle the transmission slots for the vehicles when they change pseudonyms. While the second scheme applies the effective pseudonym changing at social spots (PCS) [7] strategy with VeMAC for the MAC layer operation.In PCS, vehicles stop transmitting the safety messages when they enter the traffic light area, and begin to construct the mix-zones.After vehicles leave the mix-zone, they start to utilize the new pseudonyms to transmit safety messages in a distributed manner. The evaluated performance metrics include the average anonymity set size, pseudonym age and time-to-confusion.
In figure 5, the pseudonym age in the three schemes are investigated. The pseudonym in NMAP has the longest duration as the pseudonym age is influenced by the pseudonym age threshold, and the age distribution of the neighbors’ pseudonyms, while in the MAP scheme, it is also affected by the transmission slot usage duration. The pseudonym age in PCS is in fluenced by the frequency of encountering the intersections. However, in the real traffic environments, the utilization relies on the traffic topologies and traveling routes. If vehicles encounter intersection too frequently,it causes a waste of pseudonyms. On the other hand, if the intersection distribution is too sparse, it causes a long tracking duration of vehicles by adversaries and even compromises the location privacy.
The average anonymity set size in the mixzones achieved in the three schemes is presented in figure 6. It shows that the PCS strategy achieves the largest anonymity set size. The reason is that, all the vehicles gathering in the intersections change the pseudonyms without the consideration of the pseudonym age. The total number of vehicles at road intersections is much larger than the number of vehicles with the pseudonym lifetime expired within the one hop range in the MAP and NMAP schemes. The anonymity set size in MAP is slightly larger than in the NMAP scheme. The reason is that, as the cooperation decision of the vehicles in the MAP depends on both the pseudonym age and transmission slot usage.From figure 5 we have observed that the average pseudonym age in the MAP scheme is slightly shorter than in the NMAP scheme,which implies that the vehicles change pseudonyms more often than in the NMAP scheme,thus there would be more cooperative vehicles gather together in the MAP scheme.
All the three schemes can achieve a guaranteed anonymity set size level in the mix-zones.As the pseudonym changing strategies of MAP and NMAP are both based on the cooperation age threshold, they show almost the same performance of the anonymity set size. As figure 7 illustrates, the maximal time-to-confusion is unbounded by the pseudonym age in NMAP and PCS regardless of the pseudonym changing. In NMAP, vehicles change pseudonyms without shuffling the transmission slots. Vehicles usually acquire separately slots under the coverage of the RSU, and the mix-zone construction of each vehicle is carried out by the same RSU. Thus, the adversary can distinguish each vehicle based on its transmission slot index. Consequently, the time-to-confusion is much larger in NMAP and PCS than in the MAP scheme. The time-to-confusion in PCS shows a slight decrease when compared with NMAP. The reason is that in PCS,vehicles change pseudonyms at intersections,where the merging collisions happen more frequently. Thus, there is a higher probability that the pseudonym changing and slot releasing happen simultaneously among several vehicles in PCS, causing the adversaries lose the linking of the pseudonyms. However, the adversaries are still able to track a targeted vehicle continuously at most cases in PCS. In the proposed MAP scheme, vehicles change the pseudonyms with the transmission slots during the silent period, which cuts the linking of the new pseudonym and old pseudonyms of vehicles in the network. Therefore, the time-to-confusion is limited by the pseudonym age.
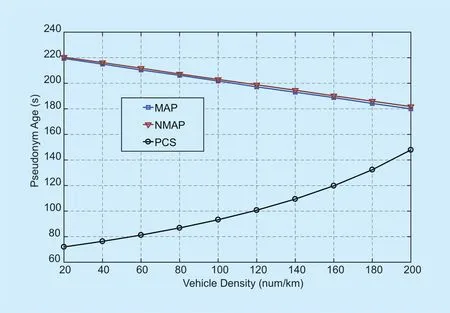
Fig. 5. The average pseudonym age of the MAP, NMAP and PCS schemes.
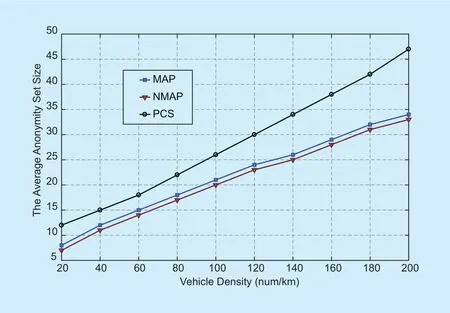
Fig. 6. The average anonymity set size of the MAP, NMAP and PCS schemes.
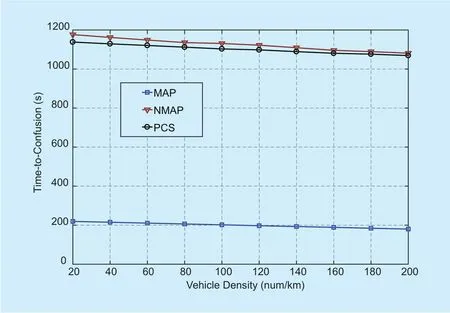
Fig. 7. The maximum time-to-confusion of the MAP, NMAP and PCS schemes.
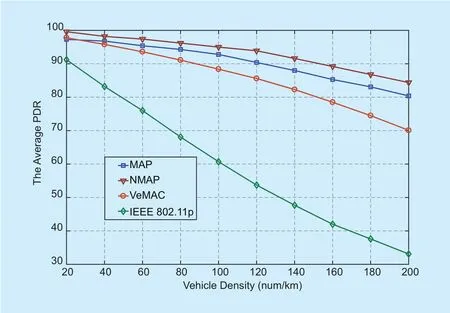
Fig. 8. The average PDR of the MAP, NMAP, VeMAC and IEEE 802.11p.
Figure 8 shows the average packet delivery ratio of the MAP, NMAP, VeMAC and IEEE 802.11p. The collisions, the silent period spent during the mix-zone construction and the time cost to reserve a new transmission slot all degrade the performance of the safety message delivery. The VeMAC scheme exploits the distributed time slotted control operation for the safety messages. The performance is slightly inferior to the RSU coordinated MAC layer performance of the MAP scheme. Compare the PDR obtained in MAP and NMAP, the PDR is almost the same. In the NMAP scheme, vehicles change pseudonyms without shuffling the transmission slots. The transmission slots can be utilized until collisions happen or trip finished for the vehicles. While in the MAP scheme, the RSU clouds shuffle the transmission slots for the vehicles with no extra cost or collisions when they change pseudonyms. As the number of vehicles increases, the merging collisions in the TDMA based schemes dominate the packet loss in the network, as a consequence, the final PDR decreases nearly in an exponential trend as the number of vehicles increases. The IEEE 802.11p has the worst performance. Our scheme presents an effective performance in both the location privacy preservation and safety messages transmission.
V. CONCLUSION
In this paper, we have presented a SDN based three-layer system architecture for the IoV,namely SDIV. We found a new MAC layer semantic linking attack and pointed out that the pseudonym management and channel accessing must be designed collaboratively. To deal with the new attack, the new cross-layer MAP scheme is proposed in the SDIV. The scheme coordinates vehicles to adaptively change pseudonyms and access the wireless channels in a contention-free manner. By measuring a composite privacy metric that includes the pseudonym age, anonymity set size and group confusion, the RSU clouds leverage the group signature for vehicles to change pseudonyms by constructing mix-zones. The security analysis and simulations results verify the effectiveness of the scheme. To the best of our knowledge, most previous work considered the MAC layer protocol and pseudonym schemes separately. This paper shed light on the cross-layer protocol design for the IoV as the security and privacy preservation must be provided for all the communication layers.
ACKNOWLEDGEMENTS
This work was supported by key special project of National Key Research and Development Program (2017YFC0803900).
- China Communications的其它文章
- DNN-Based Speech Enhancement Using Soft Audible Noise Masking for Wind Noise Reduction
- Delay-Based Cross-Layer QoS Scheme for Video Streaming in Wireless Ad Hoc Networks
- Asymptotic Analysis for Low-Resolution Massive MIMO Systems with MMSE Receiver
- Golay Pair Aided Timing Synchronization Algorithm for Distributed MIMO-OFDM System
- Joint Non-Orthogonal Multiple Access (NOMA) &Walsh-Hadamard Transform: Enhancing the Receiver Performance
- 8-Weighted-Type Fractional Fourier Transform Based Three-Branch Transmission Method

