Security Risk Prevention and Control Deployment for 5G Private Industrial Networks
Wenfa Yan,Qin Shu,Peng Gao
1 China Mobile Group Design Institute Co.,Ltd.Hubei Branch,Wuhan 430024,China
2 China Mobile Group Design Institute Co.,Ltd,Beijing 100080,China
Abstract: In this paper,we investigate and analyze the network security risks faced by 5G private industrial networks.Based on current network security architecture and 3GPP requirements and considering the actual application of 5G private industrial networks,a comparative analysis is used to plan and design a private network security construction scheme.The network security construction model,network organization,and key processes of 5G private industrial networks at the current stage are investigated.In addition,the key direction for the next stage of construction is discussed.
Keywords:5G private network;network security;security risk prevention and control
I.INTRODUCTION
During‘The Fourteenth Five-Year Plan’period,China has made it clear that it will accelerate the construction of new infrastructure and digitalisation process.With the construction of network infrastructures,the commercialisation of 5G networks has also been accelerated[1].Due to the differences in business modes and application scenarios,different industries have their unique characteristics and security requirements.Ensuring network security for industrial customers with secure 5G networks has become the focus of private network construction.Security issues have been regarded as a major bottleneck for the development of Internet of Things[2].
5G networks are designed to support three application scenarios:Enhanced Mobile Broadband (eMBB),Massive Machine Type Communication(mMTC),and Ultra-reliable and Low Latency Communications(URLLC)[3].Same as the previous generation of mobile networks,the fundamental components of a 5G network include eaccess network(e.g.,base stations,access points,edge computing servers) and core network[4].A new feature for 5G networks is that private industrial networks can be supported.Specifically,the 5G network infrastructures are deployed for different private industrial networks in a way that collaborates with various industry application platforms to support various application scenarios.However,due to the complex human-to-human,human-to-things,and things-to-things interconnections,5G application scenarios are characterised by high complexity,variability,and unpredictability.
1.1 5G Security System Architecture
To support various vertical industries,the 5G access network has become highly heterogeneous and convergent.To accommodate the diversified needs of different applications,5G introduces a new network slicing function,i.e.,an end-to-end virtual network that enables end-to-end virtual isolation of wireless access,transmission,and core networks.The network slicing function securely separates 5G network resources and provides network services to customers from different types of industries and businesses simultaneously.Such a 5G network is based on Network Function Virtualization(NFV)[5]and Software Defined Networking(SDN)[6].In particular,with the virtualization of both software and hardware,cloud computing services can be realized on a general hardware platform[7].
The 5G network standards addressed the security vulnerabilities in the 4G network and guaranteed the security of communications.The security design of 5G networks includes the following aspects:
(i) Network Access Security:a set of security features that requires the terminal to securely authenticate and access services through the network,to protect against attacks on the radio interfaces,especially to prevent the wireless interface from being attacked[8].In 5G standards,5G AKA is adopted for authentication.In particular,5G networks need to support a wide range of real-time applications like videostreaming and vehicle to everything(V2X)communications,and meet the stringent quality of service(QoS)requirements of these applications[9].
(ii)Network Domain Security:a set of security features that enables network nodes to exchange signaling and user plane data safely and enables the network interface to provide 256-bit key transmission.
(iii)Service-based Architecture(SBA)[10]:a set of security features that ensures that the network functions of the 5G SBA architecture can securely communicate with other network domains,including network function registration,discovery,and authorisation security.
(iv)Security visibility:a set of security features that provides a series of functions that enables users to know whether the safety function is running.
1.2 5G Network Construction for Security Risk Prevention and Control
The 5G network construction is based on SBA and the network hardware is evolving towards cloud-based NFV.Meanwhile,5G is expected to provide about 1000x data rate[11],which boosts an increasing demand for industrial systems with openness,interconnection,and intelligence[12].In particular,a recent survey shows that there is a growing demand of openness,interconnectivity,and intelligence generated by large and medium-sized industries,such as transportation,electric power,medical treatment,and industrial parks.To satisfy the security requirement,private industrial networks should operate with the following rules:
(i)Application data should be kept within the enterprise park:all application data can be maintained using existing methods,and data transfer is restricted within the park.
(ii)The 5G basic network must ensure network security.The corporate security operations have gradually shifted from traditional public networks to private networks[13].If the application data are kept within the industrial park,the risk of data leakage would be reduced,and the network attacks can be defended and controlled.
II.RELATED WORKS
2.1 Security Risks Faced by 5G Private Industrial Network
5G private industrial network can be applied in many business scenarios.A typical 5G industry network architecture is shown in Figure 1.
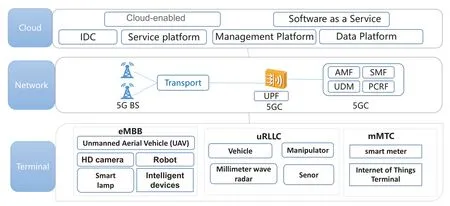
Figure 1. The architecture of 5G industry network.
(i)Terminals:Multiple types of access terminals are used in various service scenarios.One type of terminal is equipment used for sensing and monitoring,such as millimetre-wave radar,various sensor,HD camera,etc.,which is used to collect information from the environment and send the raw data to the network.The other type of terminal is application terminal,such as vehicle,automated guided vehicle(AGV),smart meter,etc.,which is able to receive and execute certain commands and tasks generated by applications.
(ii)Network:5G proprietary network,including 5G base station,access network,and core network.
(iii)Cloud:belong to the application layer of 5G private network,which provides and implements hardware and software for computing services.
According to the unique features of the three 5G application scenarios(eMBB,mMTC,and URLLC),the main security requirements of 5G private network are as follows:
(i)Security requirements in eMBB scenario
The applications in this scenario are characterized by high data rate,such as HD video and VR/AR.The security requirement is the service is that the 5G network must reliably support transmissions with high data rate and heavy traffic load,i.e.,without or with negligible interruption.This necessitates stringent requirements for speedy network recovery.
(ii)Security requirements for mMTC scenario
This scenario is characterized by a large number of IoT devices,and the typical industrial applications include smart grid and smart water conservation.The security requirements include:
First,the application data security:massive data must be safely transmitted and processed;
Second,the security of terminal access:given the large number of terminals that are spread over a certain area,it is necessary to ensure that their access processes are secure,such that security vulnerabilities caused by terminals and security threats to the network and cloud can be avoided,thus focusing on preventing DDoS attacks.
Third,network disaster recovery security:Under unpredictable natural disasters that cause significant damage to the network infrastructures,the network is expected to protect or migrate the application data and perform a certain level of self-recovery.
(iii)Security requirements for URLLC scenario
This scenario is characterized by terminals that are required to process applications with stringent latency requirements,such as autonomous driving,remote medical care,etc.The security requirements include:
I come from the Tsardom of Vyslav, answered Tsarevitch Ivan, son of Tsar Vyslav, and I am called Ivan. Thy Fire Bird entered my father s garden by night and stole many golden apples from his favorite tree. Therefore the Tsar, my father, sent me to find and bring to him the thief.
First,application security.It is necessary to prevent security risks and ensure high reliability of various applications.
Second,control safety.It is necessary to guarantee the control security of multiple types of terminals under different application scenarios,using a variety of authentication methods;
Third,network security.It is necessary to provide highly reliable connection to various applications,so as to guarantee the security of 5G private network without interruption.
To sum up,security requirements in 5G scenarios mainly focus on network security.Customers in various industries focus on how the 5G private network can fully guarantee network security,and avoid the impact of network security loopholes on the enterprise cloud.Network security risks primarily involve terminal access,open edge networks,and internal boundary control inenterprise private clouds.
(i)Terminal tampering
5G access terminals are equipped with USIM cards,which may be inserted into an unauthorised terminal.If such a terminal is connected to the network,it may launch network attacks that can results in security risks to both the 5G network and the corporate intranet.
(ii)Open edge networks
Edge computing is an important approach for industry customers/terminals to access 5G networks,but its opening interface may cause security regulatory risks.As the sinking part of the core network,edge computing has changed network architecture and business modes.Edge computing is open to third-party applications and the Internet,which brings security risks to the network boundary,including security threats to the underlying cloud infrastructure and third-party applications.
The private virtual layer in an enterprise private cloud may be vulnerable to malicious tampering or may be infected by viruses or Trojan horse malware.Such risks may threaten the security of 5G networks and result in information leakage.
2.2 Potential 5G Private Industrial Network Security Risks
As a typical DICT application foundation,5G private industrial networks must continuously adapt to the emerging 5G security technologies.This way,the IT cloud security and control requirements can be satisfied,and the security and control of“cloud network end”can be realized.The safety and control are improved from two perspectives:
(i)Strengthen network security supervision:realise hierarchical access management and control for all terminals involved in private network communication.Various types of access terminals can enhance access management,while edge computing can enhance internal and external security monitoring with edge security opening capabilities.Strengthening the security and control of access terminals can effectively reduce security risks.
(ii)Optimise physical security isolation mechanism:Soft channel isolation is achieved through network slicing,which combines slicing security management with both internal and external network security and control.At the physical layer level,this involves strengthening the hard isolation between cloud resource pools and the cloud network defences.This mechanism includes enhancing the isolation of cloud firewall hardware and access control,aiming to resist various sudden attacks.
III.NETWORK SCHEME FOR 5G PRIVATE INDUSTRIAL NETWORK SECURITY
With the proliferation of 5G industry applications,security and control are playing increasingly important roles.For example,in a 5G smart power system,the level of security is higher than traditional power industry.Therefore,it is necessary to investigate risk prevention and control in the actual network deployment[14].
In 5G private network construction,firewall deployment has been carried out using existing principles,while the internal and external isolation sare applied between the data bearer network and the power industry network.From the perspective of enhancing network security supervision,it is necessary to focus on improving the security and control of access terminals.5G terminal security access technology is primarily used to ensure identity authentication and access control in a system witha large number of terminals.Under the current machine-card separation networking mode,edge computing access risks caused by card tampering,and the resulting 5G network security risks are eliminated.
Therefore,a two-level terminal authentication system,e.g.,the 3A system,should be deployed in private industrial networks.
3.1 Access Control Via Two-level Terminal Authentication
Power terminals will be used in various 5G smart grid application scenarios,and 5G power CPE will be used in 5G networks to satisfy the need for anti-interference and equipment safety.To strengthening risk prevention,it is critical to implement 5G access control and deploy a two-level authentication (3A) system based on network authentication for terminal user cards.The 3A authentication system flexibly binds the username,password,and the access terminal’s IMEI with the user number,and then performs access authentication.The authentication mechanism can satisfy the management requirements of customers in a given industry and ensure access security.The architecture of a 5G electric power system private network is illustrated in Figure 2.
A3A authentication system can be deployed in 5G edge computing systems.Alternatively,the authentication server can be deployed in the DMZ area of an industry network.Comparison shown in Figure 3.
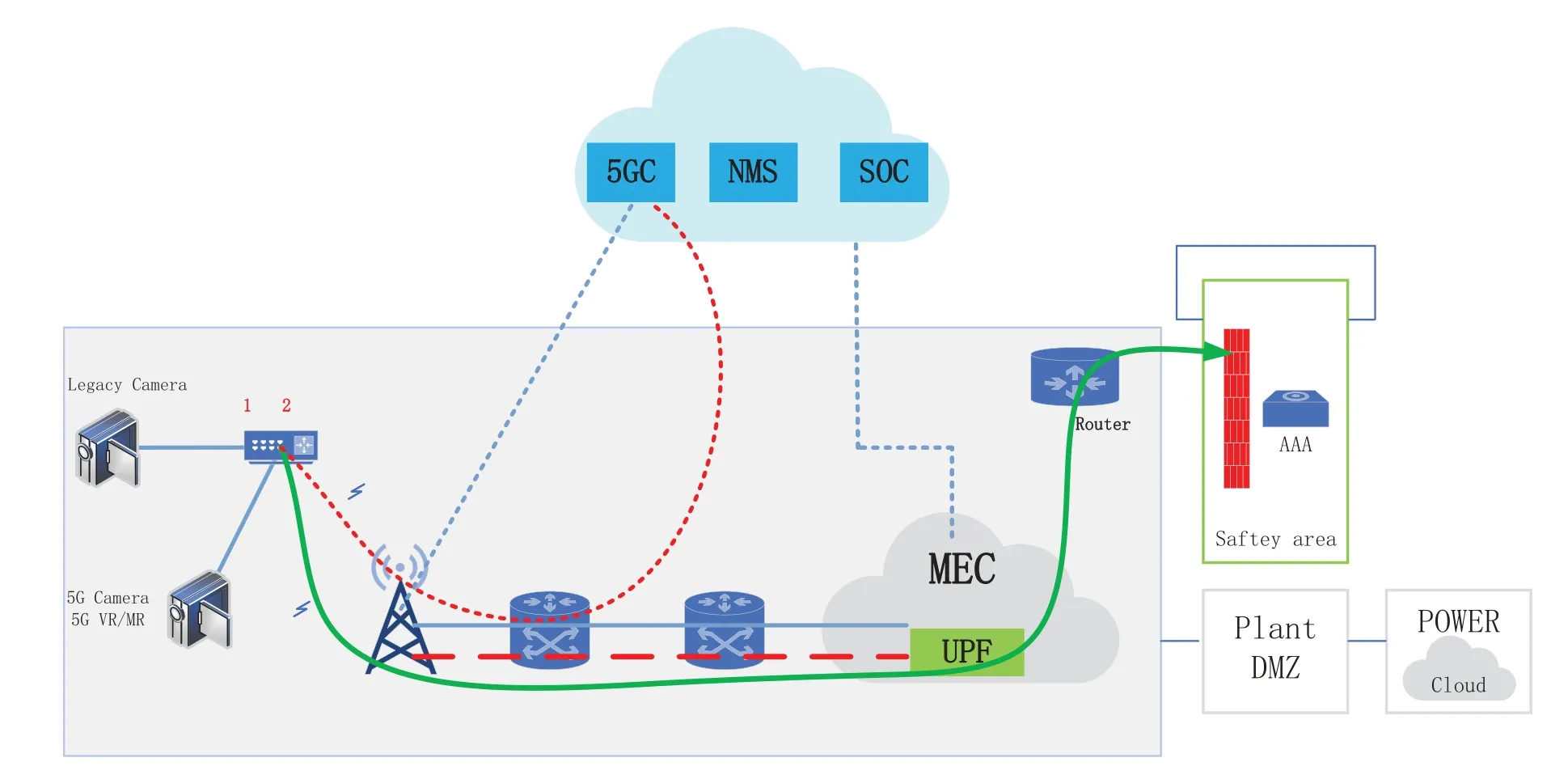
Figure 2. Diagram of 3A certification system.
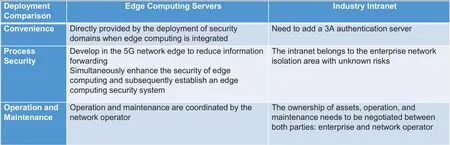
Figure 3. Comparison of different deployment methods.
From the perspective of enhancing the security of edge computing and 5G network,the authentication process in a real system is implemented at the network edge,which is supported by the computing and storage resources of edge computing servers.In this way,the service delay is guaranteed to be small,and the requirement that the delay must be no larger than the required 20ms due to the two-level authentication exchange is satisfied.
3.2 Two-level Authentication Realisation Process Improvement
Currently,5G terminal access authentication is primarily rely on 5G AKA to realise two-way authentication and encryption,and the identification parameter is the 5G permanent identifier SUPI.The 3A system is connected to the 5G communication network,which works cooperatively with security certification.
Terminal access implements a two-level authentication process:When accessing the 5G network,various terminals first complete the encryption-based authentication via a wireless network and a User Data Management (UDM) system.Once a new 3A authentication mechanism is initiated,the two-level authentication is performed between the terminal and the 3A authentication server,as shown in Figure 4.
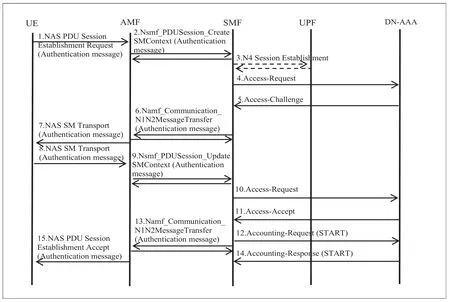
Figure 4. Two-level authentication flow chart.
In the authentication process,SMF first obtains the user identification information,i.e.,the SUPI,from the UDM system and checks whether the SUPI value matches the user type and determines whether the access should be granted.The second step of the authentication process is initiated only if the first step is completed successfully.The second step of authentication is performed as follows:
Authentication trigger:The SMF that has authenticated the user initiates PAP/CHAP authentication,which is used to obtain the authentication information from DN-AAA.The information can be verified using a combination of user number,PEI (similar to IMEI),user name,and password.
UPF establishes an authentication channel:According to the rules,the two-level authentication server is deployed outside the 5G private network,and the UPF needs to establish a PDU data channel to send authentication information.
SMF saves authentication information:After the authentication is completed,the SMF can save the DNN name of the 3A authentication server to facilitate the acquisition of the second authentication,so as to reduce the repetition of the process.
Currently,industry terminals do not support the EAP protocol defined by 3GPP;therefore,the 3A Radius protocol is used with industry terminals in the initial construction.In smart power generation and power grid monitoring scenarios,the core network SMF to 3A multiplexes the signaling plane channel of the data bearer network.As sensitive information is involved in the communication,IPsec encrypted tunnels are used for information delivery.
3.3 Modelling for Certification System Application
In this section,the user authentication model is described,which is based on 5G smart grid business scenarios and terminal types.According to the requirements of current business scenarios and the type of application protocol,the authentication model includes the following components:
(i) Classification of terminals:terminals are divided into two categories.The first kind of terminal is a terminal that uses a 5G USIM card,and the second kind of terminal is a terminal that connects to the 5G network.
(ii)Terminals concurrent authentication parameters:the parameters of authentications that occur in the same time period.
(iii)Authentication period:primarily refers to the time it takes for the authentication information to be stored.
(iv)Single authentication information length:the size of each key authentication information item(in bytes)is restricted according to the authentication rules.For example,PEI(IMEI)occupies 15 bytes.
Based on data format requirements,the settings of the authentication model at the initial deployment are shown in Table 1.
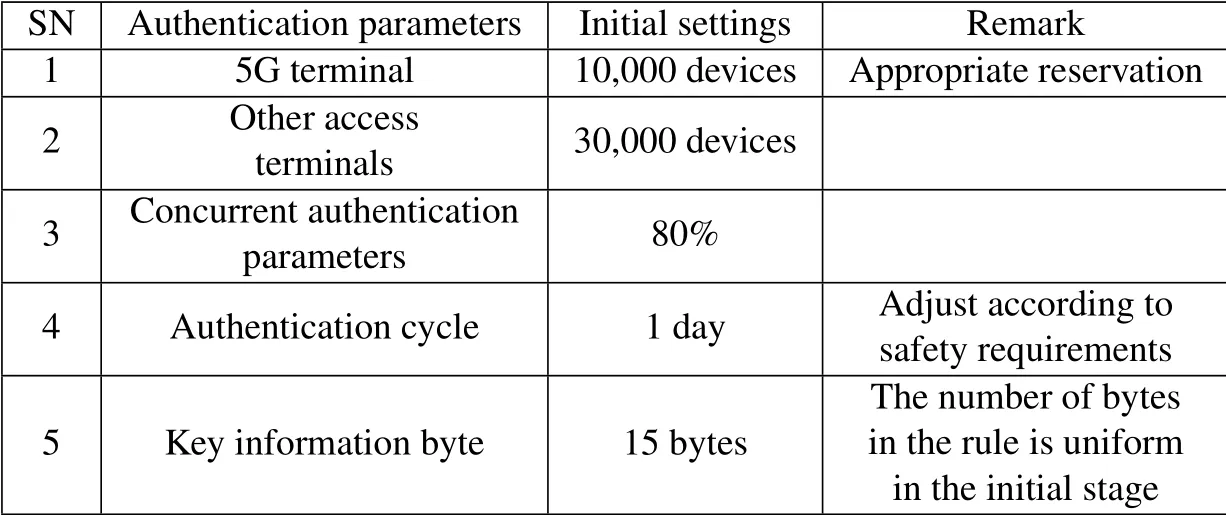
Table 1. Parameters and settings of 3A certification model for power terminals.
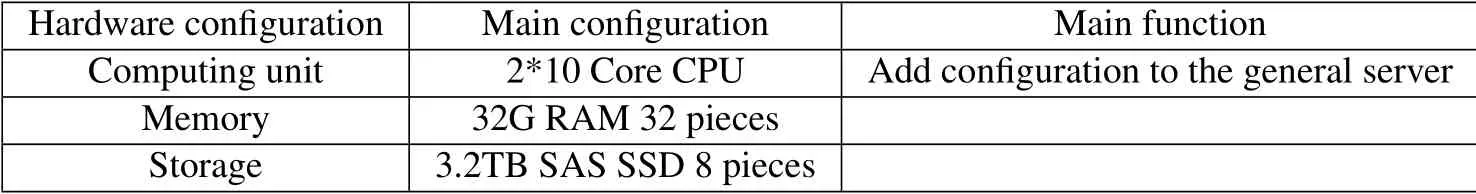
Table 2. Main hardware requirements for power 3A system construction.
3.4 5G Smart Grid Private Network Security Deployment Application
Due to regulatory requirements,power grid securityis divided into production control and information management.In the construction of a 5G smart grid private network,applications based on terminal security are enabled.
For 5G power terminals and 5G wireless networks,edge computing nodes are installedatkey industrial parks of the power grid.Here,5G industry terminals refer to the power industry terminals and other terminals that support 5G communication.Based on the different security needs of customers,such terminals can be classified as general industry terminals and dual-domain security terminals.Compared with ordinary terminals,dual-domain security terminals can provide a higher level of data security and satisfy a higher level of protection requirements.
A small 5G base station deployed indoors and a 5G macro base station deployed outdoors provide seamless 5G wireless coverage for the entire park.At the same time,existing mobile and fixed networks in a given area,such as Wi-Fi and optical fibre networks,are integrated to achieve fully connected wireless coverage.This way,all types of terminals can be controlled.
In addition to wireless access,Mobile Edge Computing (MEC) is also used to provide computational task offloading and edge access capabilities.The computing and storage capabilities of MEC servers can be utilized to provide computing services to terminals in the working area of the park.This way,interaction delay can be reduced.Besides,the security level can also be improved since the data generated by terminals are processed within the industrial park.Earlystage edge computing is operated with built-in NFV mode,where the hardware guarantees the basic requirements.According to the business scenario model in Table 2.the hardware requirement can be identified.
The security risk prevention and control platform are based on terminal management,which continues to add security management functions,including unified authentication of user accounts,compliant content monitoring,and hierarchical content filtering.Secure big data applications are based on control data.
After the network deployment is complete,packets are captured and decomposed for the secondary authentication process.The process information shows that the terminal authentication is running normally.as shown in Figure 5.
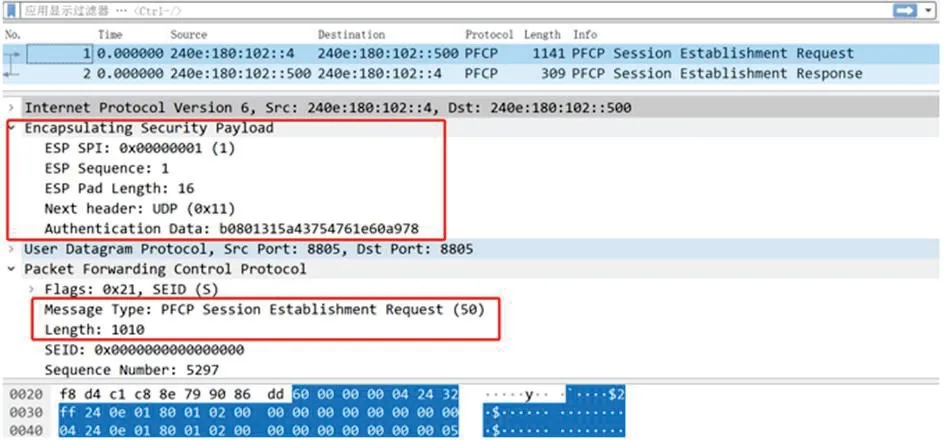
Figure 5. Decoding flow chart.
IV.CONCLUSION
This paper studied the security risks faced by 5G private industrial networks and proposed a security enhancement solution for 5G smart grid private networks.The proposed scheme meets the security risk prevention and control requirements of industry customers for terminals.Besides,it can classify and control all types of access terminals.With the continuous development of 5G applications,the 5G terminal industry chain and solutions will continue to improve,making data safety an increasingly important area.
ACKNOWLEDGEMENT
This work was supported by the company research topic.
- China Communications的其它文章
- Correlation-Aware Replica Prefetching Strategy to Decrease Access Latency in Edge Cloud
- Secure Transmission in Downlink Non-Orthogonal Multiple Access Based on Polar Codes
- M2LC-Net:A Multi-Modal Multi-Disease Long-Tailed Classification Network for Real Clinical Scenes
- DEEPNOISE:Learning Sensor and Process Noise to Detect Data Integrity Attacks in CPS
- Beamforming Optimization for RIS-Aided SWIPT in Cell-Free MIMO Networks
- Cost-Minimized Virtual Elastic Optical Network Provisioning with Guaranteed QoS

