Secure Transmission in Downlink Non-Orthogonal Multiple Access Based on Polar Codes
Ce Sun,Zesong Fei,*,Bin Li,Xinyi Wang,Nan Li,Lijie Hu
1 School of Information and Electronics,Beijing Institute of Technology,Beijing 100081,China.
2 Nanjing University of Information Science and Technology,Nanjing 210044,China
3 China Mobile Research Institute,Beijing 100053,China
Abstract: Non-orthogonal multiple access(NOMA)is deemed to have a superior spectral efficiency and polar codes have became the channel coding scheme for control channel of enhanced mobile broadband(eMBB) in the fifth generation (5G) communication systems.In this paper,NOMA combined with polar codes is used to achieve secure transmission.Both degraded wiretap channel and non-degraded wiretap channel are considered,where an eavesdropper intercepts the communication between base station (BS)and users.For the degraded wiretap channel scenario,a secure polar encoding scheme is proposed in NOMA systems with power allocation to achieve the maximum secrecy capacity.With regard to the nondegraded wiretap channel,a polar encoding scheme with multiple-input-single-output (MISO) system is proposed,where artificial noise is generated at BS to confuse the eavesdropper’s channel via transmit beamforming.The security and the secure rate are employed respectively in order to measure the secrecy performance.We prove that the proposed schemes for each scenario can achieve the secure rate and can transmit the signal securely and reliably.The simulation results show that the eavesdropper hardly decoding the secure signal when the legitimate receiver can decode the signal with very low block error rate(BLER).
Keywords:physical layer security; polar codes; nonorthogonal multiple access;artificial noise
I.INTRODUCTION
Channel coding and multiple access (MA) are regarded as two crucial technique of wireless communication from the first generation(1G)to fourth generation (4G).In the field of channel coding,polar code proposed by Arikan is the first capacity achieving family of error correction codes for binary-input discrete memoryless channels[1].Because of the low encoding complexity and capacity achieving property,polar code has supplanted the tail biting convolution code(TBCC),and becomes the channel coding scheme for control channel of enhance mobile broadband(eMBB)in the fifth generation (5G) communication systems.This capacity-achieving code family uses a technique called channel polarization.The polarization process of polar codes over a prime q-ary alphabet is studied[2],where a different approach to computing the degree of this polynomial for any prime alphabet size is shown.The work in[3-7]is dedicated to irregular polar codes,where polarlization units are irregularly inactivated to achieve additional degrees of freedom for code design.The irregular polar codes can significantly reduce encoding/decoding complexity.The successive cancelation(SC)decoding is the basic decoding algorithm for polar codes with low complexity.The successive cancelation list (SCL) decoding algorithm has better performance by maintainingLmostly likely decoding paths,but the complexity is increased with largerL[8].Apart from SC-based decoder,there are some belief propagation (BP) decoders with high parallelism,and a low complexity BP decoder is proposed in[9].
In the field of MA,as an important candidate of MA technique in the next generation wireless communication system,non-orthogonal multiple access(NOMA)has been proposed to increase the spectral efficiency and system throughput[10,11].NOMA technique can be further classified as two types upon investigating the multiplexing gain gleaned from the different domains,i.e.,code-domain NOMA and power-domain NOMA[12].Power-domain NOMA,which allows a base station (BS) to superimpose signals to multiple users with different powers,is deemed to have a superior spectral efficiency.Different users are allocated with different power levels according to their channel condition and the successive interference cancellation (SIC) is used in the receiver to cancel the multiple-user interference.In order to ensure the fairness of users in NOMA system,power allocation is an important part of NOMA.A cooperative simultaneous wireless power transfer(SWIPT)aided NOMA protocol was proposed by Liuet al..[13],where a NOMA user benefitting from good channel conditions acts as an energy harvesting source in order to assist a NOMA user suffering from poor channel conditions.Zhanget al.proposed an energy efficient(EE)-optimal power allocation strategy with the aim of maximizing the system EE[14].And in[15],a dynamic user clustering and power allocation for uplink and downlink NOMA systems were investigated to maximize the sum-throughput in a cell.
Security is a crucial concern due to the broadcast nature of wireless transmission[16].Physical layer security (PLS) has the potential to prevent information leakage from eavesdroppers by exploiting the differences in channel conditions and has attracted significant attention[17].Recently,NOMA and polar codes have been applied spread into the PLS to improve the performance gain and achieve strong security[18-20].In particular,[21]allocated the information bits in bit channels which are good for legitimate users (who are denoted as Bob) but bad for eavesdropper (who is denoted as Eve).The security key was discussed in[22-24],where the index and the value of frozen bits of the polar codes are hidden from Eve.[25]presented a secure transmission based on polar codes for fading wiretap channels.[26]designed an encoding and decoding scheme for polar codes over the general wiretap channel.Apart from the serial channel model,the parallel channel model is useful in many practical scenarios,such as transmission over block fading channels,multi-subcarrier communication and network coding.Polar codes construction over parallel channels was presented in[27]that considers the use of polar codes to enable secure transmission over parallel relay channels.By exploiting the properties of polar codes over parallel channels,a polar encoding algorithm was designed based on channel state information (CSI) between the legitimate transmitter and the legitimate receiver[28].
In[29],PLS rate maximization problem in NOMA systems was investigated where a single-input-singleoutput secure transmission system is considered.[30]focused on a NOMA system,where a transmitter sends confidential messages to multiple users in the presence of an external eavesdropper.The optimal designs of decoding order,transmission rates,and power allocated to each user are investigated.The PLS of NOMA in large-scale networks was investigated with invoking stochastic geometry[31].Both single-antenna and multiple-antenna aided transmission scenarios are considered.Also,the application of NOMA to a multi-user network with mixed multicasting and unicasting traffic was designed[32].The proposed joint design of beamforming and power allocation ensure that the unicasting performance is improved while maintaining the reception reliability of multicasting.An analysis framework was developed in[33]to evaluate the reliability and security performance of cooperative NOMA in the context of cognitive networks,where both a primary base station(PBS) and a NOMA-strong primary user send confidential messages to multiple uniformly distributed PUs in the presence of randomly located external eavesdroppers.The eavesdroppers in the above papers all belong to external eavesdroppers who are not involved in non-orthogonal transmission.The author of[34]considered a cellular downlink multipleinput-single-output (MISO) NOMA secure transmission system where users are grouped as multiple clusters.They focus on secure beamforming and power allocation design optimization problem which maximizes the achievable sum secrecy rate of central users subject to transmit power constraint at base station and transmission rate requirements at cell-edge users[35].
1.1 Motivation and Contribution
As mentioned above,PLS has been studied in various scenarios,but there is still a paucity of research contributions on investigating the security issues of the combination of MA and channel coding.For NOMA,there are a lot of research analysing the secure performance and the power allocation,but the research about designing a transmission scheme with channel coding or modulation is rare.For the channel coding,however,there are few research about applying the secure transmission scheme into the practical MA system,which motivates this contribution.In this paper,a secure transmission scheme is designed combining NOMA and polar codes.The difference among the transmission rate of legitimate users and eavesdroppers is analysed,and then the difference is devoted to design the polar encoding scheme.The degraded wiretap channel and the non-degraded wiretap channel are considered with the secure polar encoding scheme that is designed for both scenarios to transmit signal reliably and securely.The contributions made by this work are summarized as follows:
·We design a polar encoding algorithm in downlink NOMA system both for a degraded wiretap channel and a non-degraded wiretap channel.Then the security performance of proposed scheme is investigated.NOMA and polar codes are combined to achieve security.Additionally,artificial noise (AN) is generated at BS in the multiple-antenna aided scheme for enhancing the secrecy performance when wiretap channel is non-degraded channel.
·For the degraded wiretap channel,the gap of transmission rate between main channels and wiretap channel are investigated in NOMA system.Taking advantage of that gap,polar encoder is designed based on the nested feature of polar codes.The information is set into the subchannels which are‘good’for users but‘bad’for eavesdropper.The secure rate is analysed and the power allocation is optimized to maximize the secure rate.
·For the non-degraded wiretap channel,we note that the traditional coding scheme can not transmit signal securely.The multiple-antenna aided scheme is proposed to generate AN at BS.By transmitting appropriate AN,the wiretap channel is deteriorated without affecting the main channels to obtain the transmission rate gap between users and eavesdropper,then the polar coding scheme is the same as that for the above scenario.The power allocation among differen users in NOMA system and AN is analysed for this scenario.
·We prove that the proposed scheme can achieve the security and reliability for each scenario and the simulation results show that the eavesdropper can hardly decode the information when the legitimate receivers decode the signal with a very low block error rate(BLER).
1.2 Organization
The rest of the paper is organized as follows.In Section II,we give preliminaries of polar codes and NOMA,then the system model of transmission scheme is described.Section III proposes the polar coding scheme in downlink NOMA system for degraded wiretap channel.Then,the coding algorithm for the scenario of non-degraded wiretap channel is proposed in Sections IV.The simulation results are shown in Section V,followed by the conclusion in Section VI.
II.PRELIMINARIESANDSYSTEM MODEL
This section gives preliminaries of polar codes and NOMA,then the system model of transmission scheme is described.
2.1 Polar Codes
Polar codes are based on the channel polarization phenomenon which is described as follows:For any binary discrete memoryless channels (B-DMCs)W:X →Ywith input alphabetX,output alphabetY,the channelspolarize in the sense that,for any fixedδ ∈(0,1),asNgoes to infinity,the fraction of indicesi ∈{0,...,N ?1}for whichgoes toI(W) and the fraction for which[0,δ) goes to 1?I(W).WhereNis the length of codeword which is equal to the length of polarized sub-channels,anddenotes theith polarized subchannel ofNsub-channels,I(?)denotes the channel capacity of?.The Bhattacharyya parameter is defined as
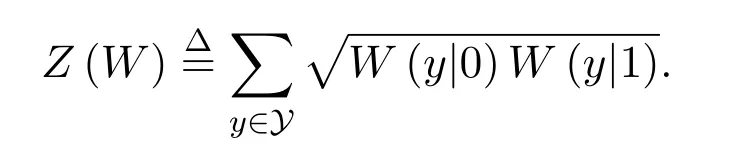
I(W) is the highest rate at which reliable communication is possible acrossWusing the inputs ofWwith equal frequency.Z(W) is an upper bound of error probability for maximum-likelihood(ML)decision when is used only once to transmit a 0 or 1.For any B-DMCW,we have
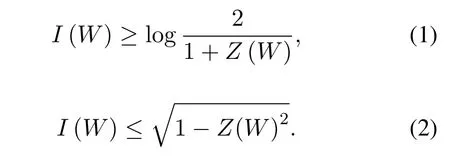
Following[36],based on Bhattacharyya parameter,the sub-channels are split into good sub-channels and bad sub-channels.The index sets of the good and bad sub-channels are given by
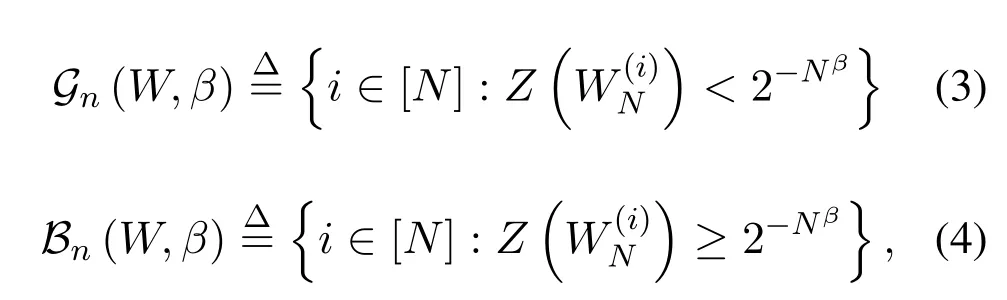
where[N]={0,2,...N ?1},andβ <1/2 is a fixed positive constant.It is worth noting that the fraction of the good sub-channels goes toI(W) asN →∞[1][36],which is stated precisely as follow:
Theorem 1:For any B-DMCWand constantβ <1/2,we have
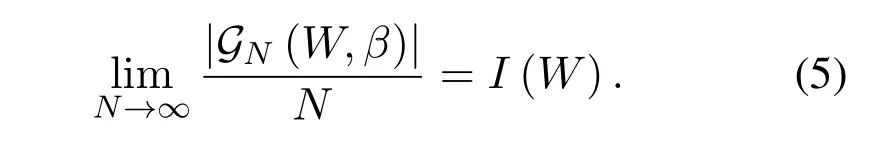
Theorem 1 readily leads to a construction of capacityachieving polar codes.We define the good subchannel set asAand the bad sub-channel asAC.Polar encoding is denoted aswhereis the codeword,{u0,u2,...,uN-1}is the information block,and GNis the generator matrix of orderN.The recursive definition of GNis given by
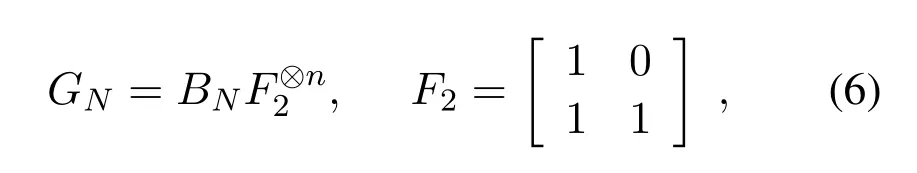
whereBNis a permutation matrix and?denotes kronecker product.
The construction of polar codes can be represented by Figure 1 using Eq.(6) withN= 2n= 8,n= 3,where{u0,u1,...,u7}denotes the message to be encoded and the{x0,x1,...,x7}denotes the codeword by polar coding.
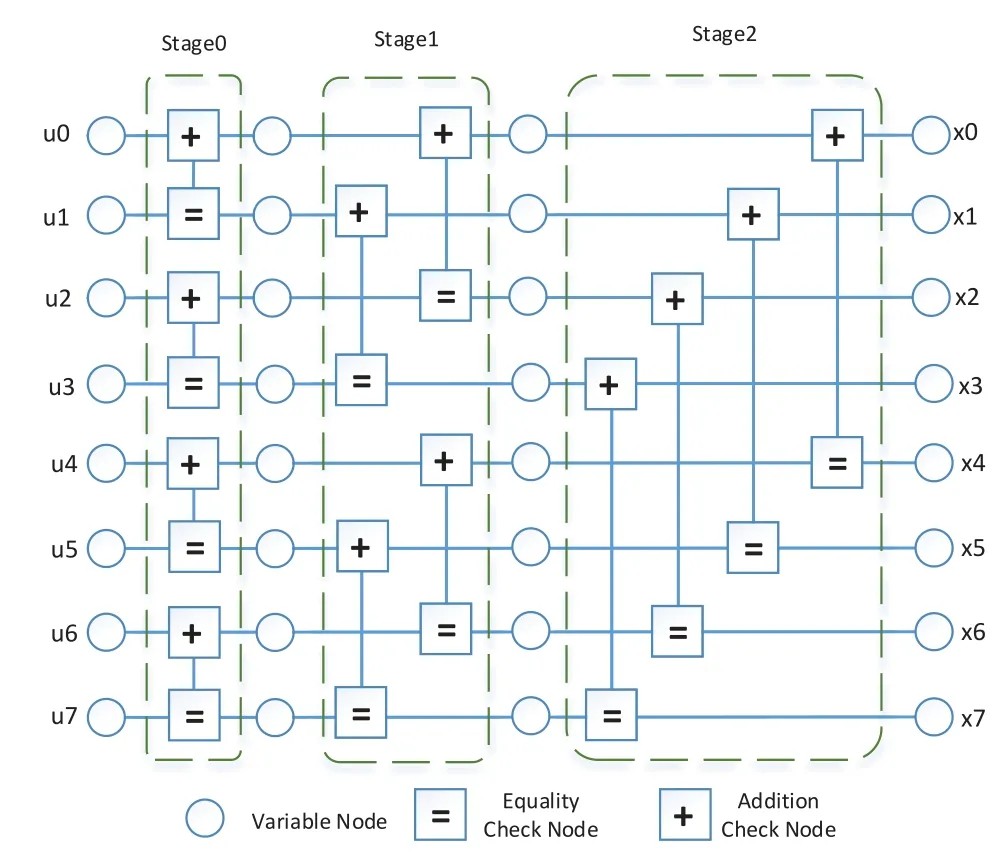
Figure 1. The processing of construction of polar codes.
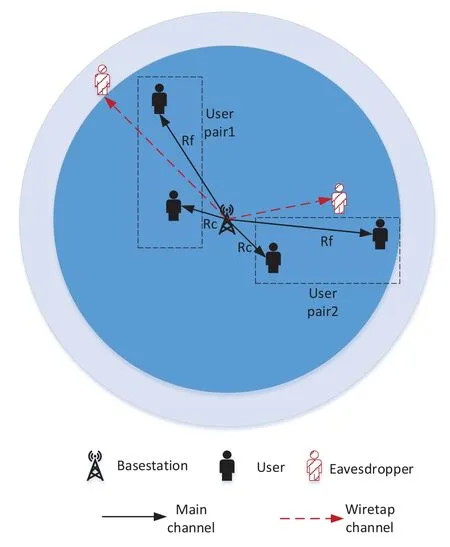
Figure 2. System model for downlink NOMA.
AsZ(W)is an upper bound of error probability,we note that the channel output is not decoded to under successive cancellation decoding satisfies
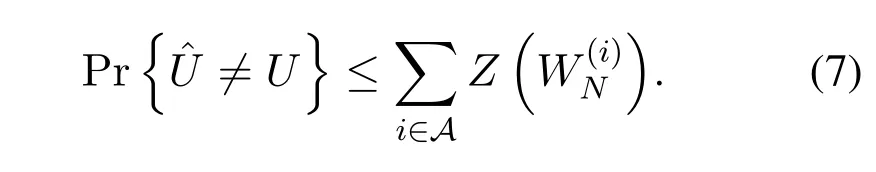
The SC decoder generates its decisionby computing
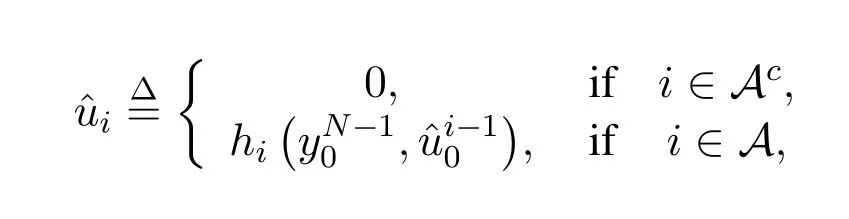
with
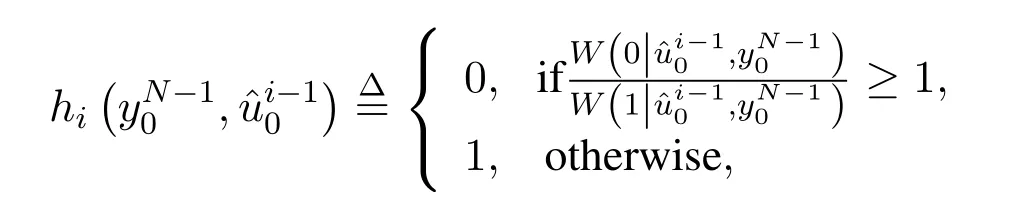
whereydenotes the received message and.
The SC decoder of polar codes can be regarded as a greedy search algorithm based on the compact-stage code tree.Two paths associated with an information bit at a certain layer are candidates and only one path that has larger probability can be selected for the further processing.Based on the SC decoder,the SCL decoder searches the code tree layer by layer with the same manner as SC.Different from SC,the SCL decoder allowsLcandidate paths to the further processing.
2.2 NOMA and System Model
After encoding and modulating,the signal is superimposed to multiple users with different powers.Power domain is regarded as the extension of time-domain,frequency-domain and space-domain.Therefore,in limited time,frequency and space,more users are allowed to access.It is well documented that,orthogonal multiple access technology allocates the orthogonal resource to different users to avoid interference.But in NOMA system,the interference is introduced aiming at the condition when the channel state among users are quite different.
As shown in Figure 2,we focus our attention on a secure downlink communication system.In the system,BS transmits signal toMusers.TheMusers are divided in toM/2 pairs.Each pair is allocated to an orthogonal resource,such as a time slot or a frequency band.For simplicity,we only focus our attention on investigating two typical pairs of users in this paper.
The path fading channel is considered in the system,it is assumed that all the channels between BS andMusers obey|h1|2<|h2|2<···<|hm|2.And in one user pair,c-th user is close to BS whilef-th user is far from BS(c <f),they are paired for transmission in the same resource elements (REs).Apart from BS and legitimate users,there are an eavesdropper (Eve)intercepting the information transmission,two scenarios are considered in this paper,one is that the distance between BS and Eve is farther thef-user,and anther scenario is that the the distance between BS and Eve is farther than thec-user and closer than thef-user.The signalxi(i=c,f)of different users in one pair is superimposed so the transmit signalsof BS is denoted as:
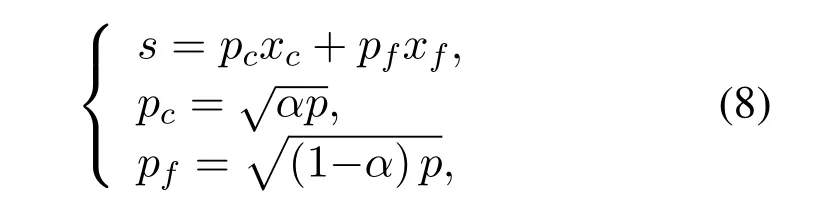
wherepis the power of BS andαis the coefficient for power allocation.
At the receiver,the legitimate users receive signalyithat is defined as:
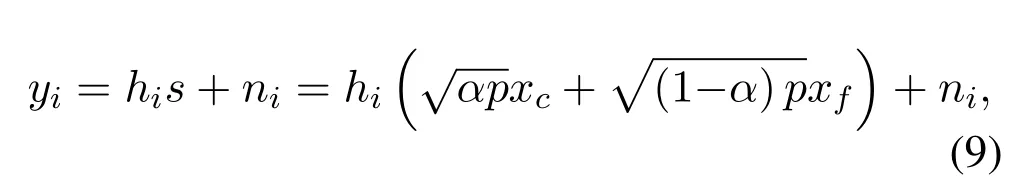
whereniis the additive white Gaussian noise with 0 means andvariance,that isThe receivers use SIC detector which is shown in Figure 3 to detect the signal.For thef-th user,he is farther thanc-th user and allocated more transmission power,so he has a less interference-infested signal.When thef-th user detects the signal,The signals of other users are threaded as interference and target signal is detected directly.The signal-to-noise-plus-interference rate (SINR) of thef-th user can be calculated as follow
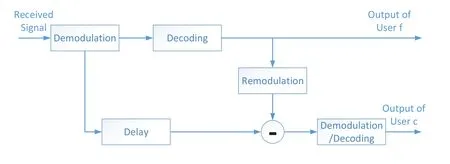
Figure 3. The process of SIC detector.
Figure 4. Secrecy rate vs.power allocation with different BS power.
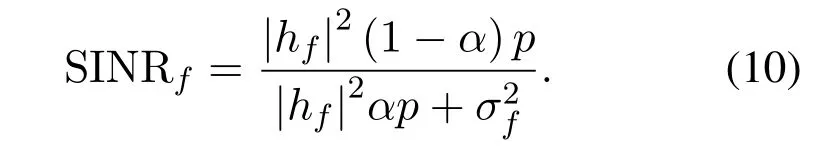
For thec-th user,it should detect the signal of thef-th user firstly,then the signal of thef-th user is remodulated and deducted from the original signal.Finally,thec-th user can detect his target signal.The SINR of thec-th user can be calculated as follow:
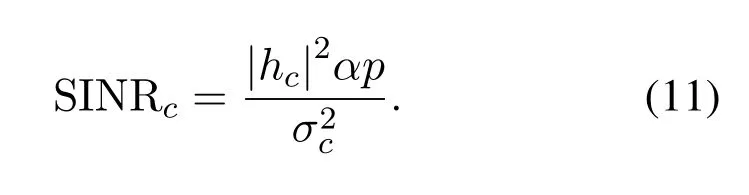
The Eve receives signalzthat is defined as:
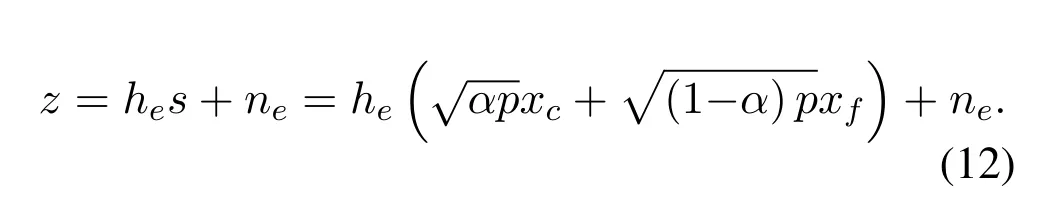
The worst-case is considered,in which the Eve is assumed to have capability of powerful detection.By applying multiuser detection techniques,the multiuser data stream received from BS can be distinguished by Eve,upon subtracting interference generated by the superposed signals from each other.In detail,when Eve detects the signal ofc-th user,it is assumed to detected the signal off-th user correctly.In fact,this assumption overestimates the Eve’s multi-user decodability.Therefore,the SINR of detecting the signal of each user in one pair for the most detrimental Eve is
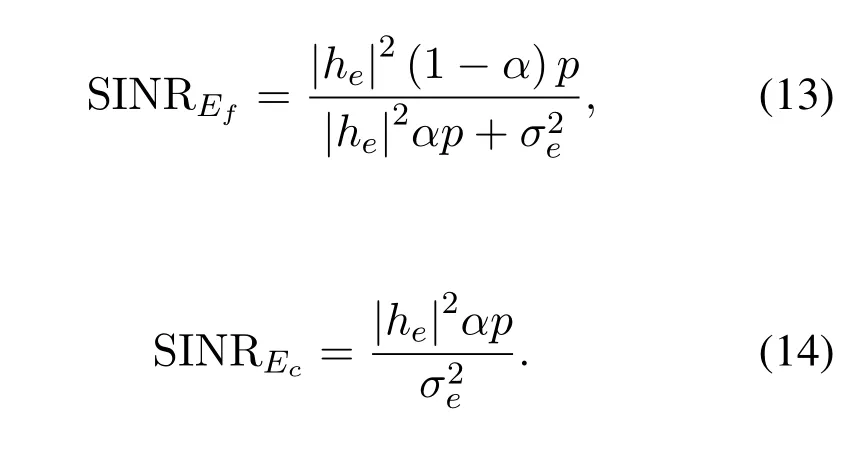
III.POLAR CODES FOR DEGRADED WIRETAP CHANNEL
In this section,a degraded wiretap channel is considered,in which the Eve is farther from BS than the two users in a pair.
3.1 Power Allocation
A polar encoding scheme is designed for security transmission in downlink NOMA system,how do we measure the security of our scheme? Security is usually measured in terms of the normalized mutual information between the message and Eve’s observations.Specifically,one is interested in encoding algorithms that satisfy the following
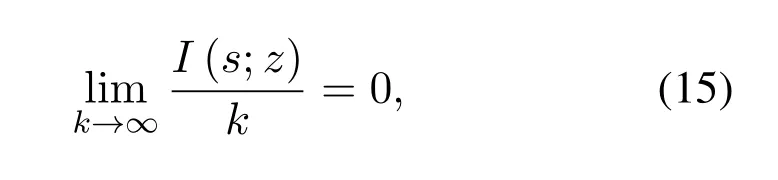
wherekis the length of information.As thexcandxfare independent,theI(s;z)in Eq.(15)is
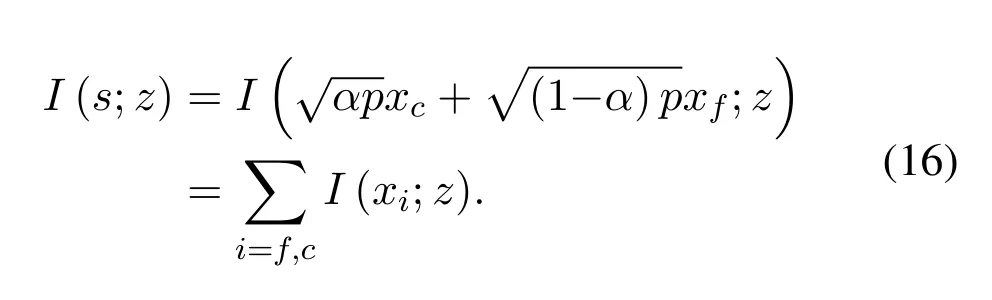
And for the whole communication process,the secrecy capacity of the users can be defined as:
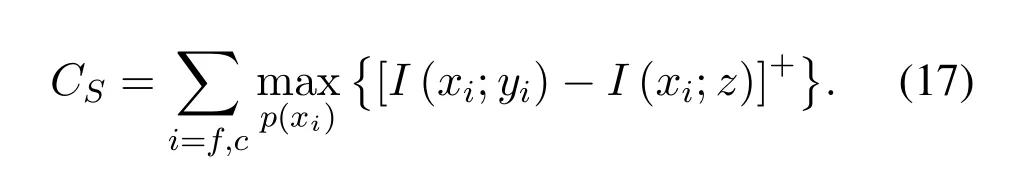
In our model,the modulation method of user is binary phase shift keying (BPSK),xiis restricted to a binary alphabet with uniform distribution,i.e.,
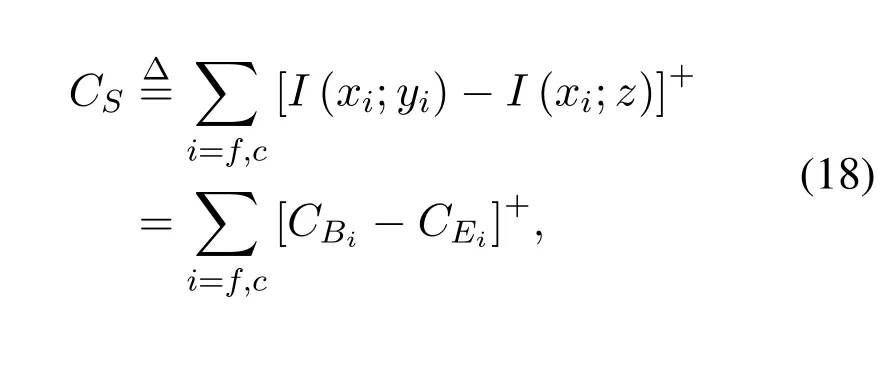
whereCBiandCEiare the binary-input constraint channel capacities of the main channels and the wiretap channels respectively and[x]+=max{0,x}.The mutual informationI(x;y)is defined as:
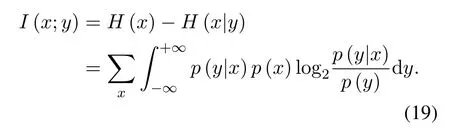
CSI of the main channel is perfectly available at all nodes.Then the instantaneous capacity of the main channel is shown in Eq.(21) at the top of next page,whereis the variance of the equivalent noise fori-th user:

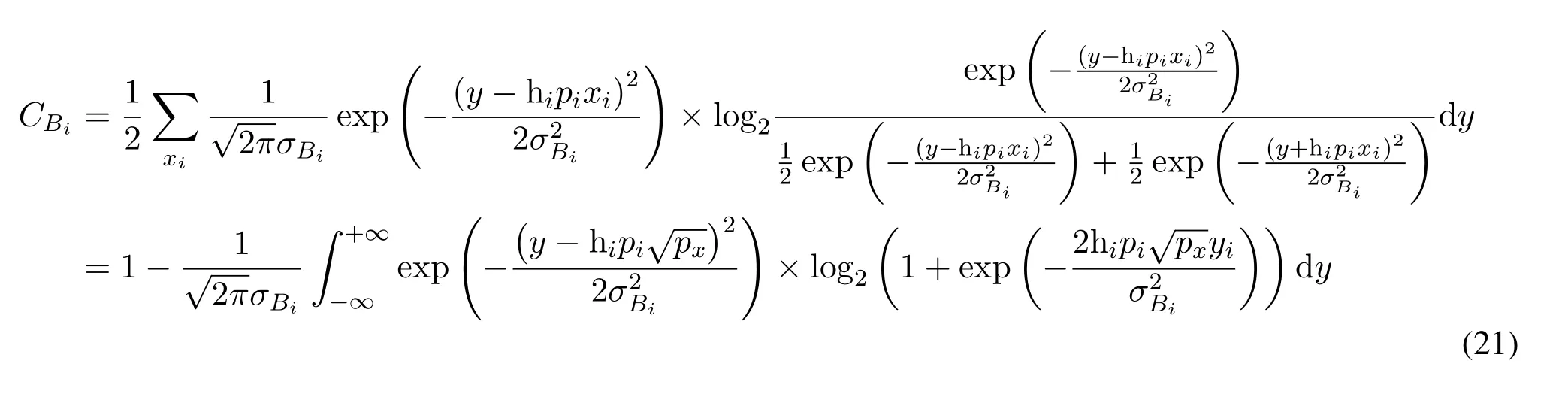
A series expression for evaluating Eq.(21) is given in Eq.(22),whereAsvanishes fast with the increasing ofj,so the maximum ofjdoes not to be quite large when evaluating the channel capacity using Eq.(22).
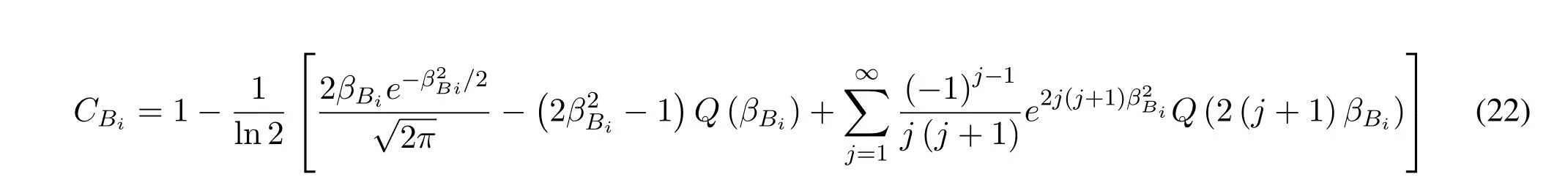
The calculation of capacity of wiretap channel is same as that of main channel,which can be given by Eq.(23) at the top of next page,where.
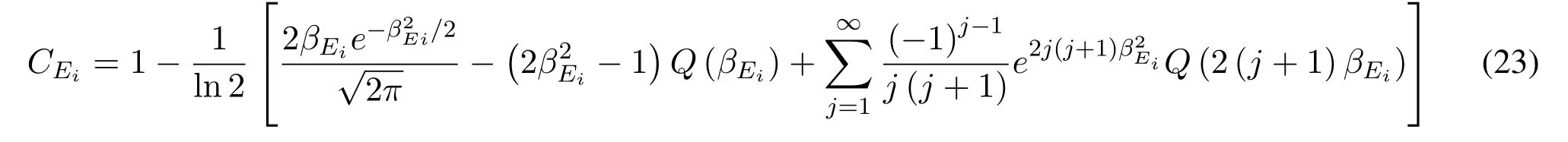
The optimal power allocation between two users in one pair needs to be found to maximize the secure rate.As the same time,the rate of each user should not be below a thresholdCthr.The optimization problem can be formulated as:
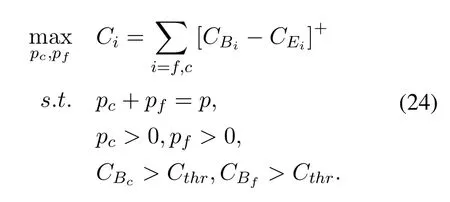
We setpc=αpandpf= (1?α)p.This optimization problem can be turned into a single variable problem due to the power constraint,and can be easily solved.The Figure 4 and Figure 5 show some cases of secure rate change with the different coefficient of power allocation.BS power isp= 40dBm(case1) andp= 60dBm (case2) in Figure 4 respectively.The distance ofc-th users andf-th users and eavesdropper from BS are{5m,8m,20m}(case1),{7m,12m,25m}(case2)in Figure 5 respectively.The simulation results show that the secure sum rate is better with largerαwhenf-th user’s rate reach the minimum threshold.
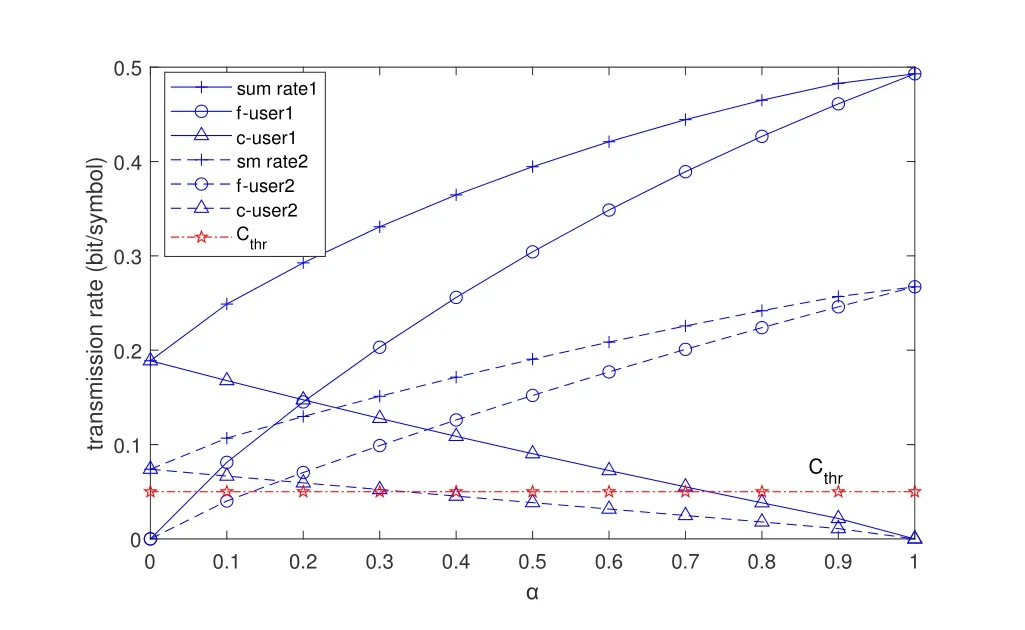
Figure 5. Secrecy rate vs.power allocation with different distance.
3.2 Proposed Scheme
The proposed scheme is based on the polar codes’nested feature that is proved in[37]as follow:
Lemma 1.The W and W? are the BDMCs and the W? is degraded with respect to the W.Letanddenote the correspondingpolarized sub-channels.Thenis degradedwith regard tofor all i= 0,2,...,N ?1,so.
As mentioned above,in this section we consider the ideal scenario in which the wiretap channelW?is degraded with respect to both main channels.It should be noted that there are only one wiretap channel for one user pair in the system model,but actually the eavesdropper detects the signal of each user by SIC detector and there are two equivalent wiretap channels based on the different SINR:withandwith,whereandcan be calculated by Eq.(14) and Eq.(13) respectively.It follows Lemma 1 that the set of good sub-channels ofW?is the subset of the that of main channelsW.We havefor all constantsβ.
Based on the nested feature and the gap betweenW?andW,when polar encoding performing at BS,the sub-channels of each user are split into three sets:the set of random bitsR,the set of information bitsAand the set of frozen bitsF,which are illustrated as Figure 6.Formally,we fix a positive constantβ <1/2 and three subsets are defined as follow:
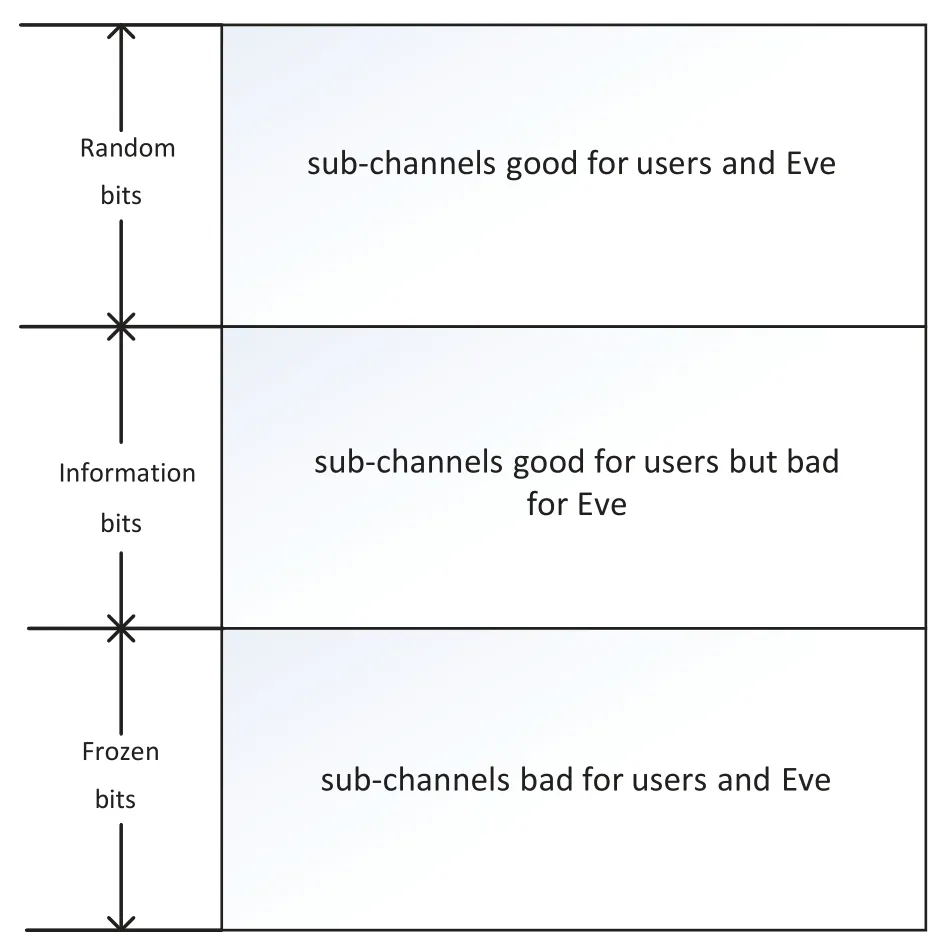
Figure 6. Sub-channel set in the polar encoder.
When BS encodes the information of each user in one pair,the sub-channel sets for each user are calculated and transmitter set the random bitsriintoR,information bitsaiintoAand frozen bits intoF,wherei={c,f}and the frozen bits are set as full zeros sequence 0.Theai,riand frozen bits are combined as an encoding sequenceuifor each user.Then the polar encoder encodesuiasxi,(i={c,f})by Eq.(6).The signalxiof different users in on pair is superimposed as the transmission signalsas noted in Eq.(8).The transmission process is completed.And the receiving process has been shown as Figure 3,and the whole communication process is shown as FIgure 7.
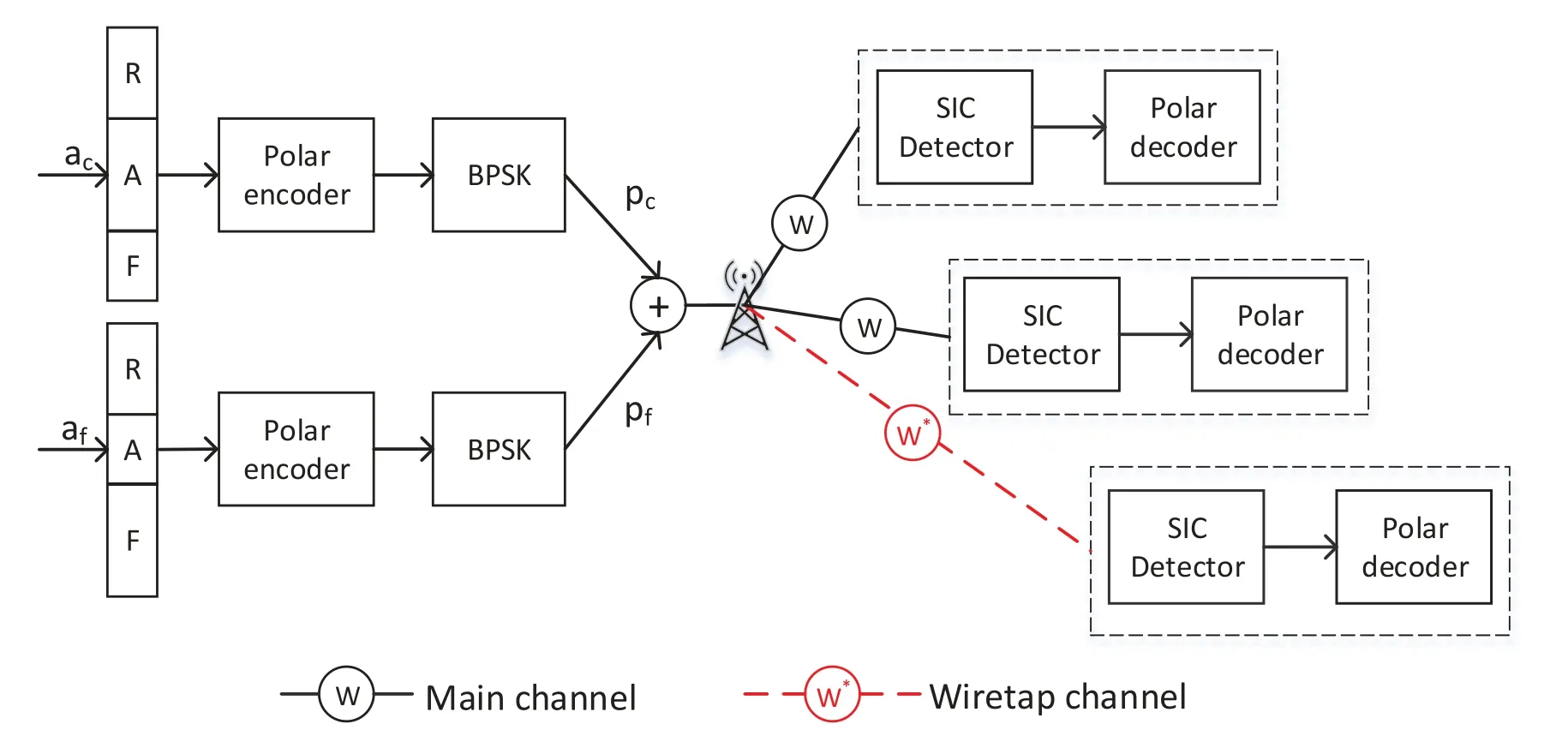
Figure 7. The whole communication process.
Figure 8. The secrecy rate of AN-aided scheme vs.power allocation with the distance of c-user,f-user and eavesdropper from BS is{5m,8m,7m}.
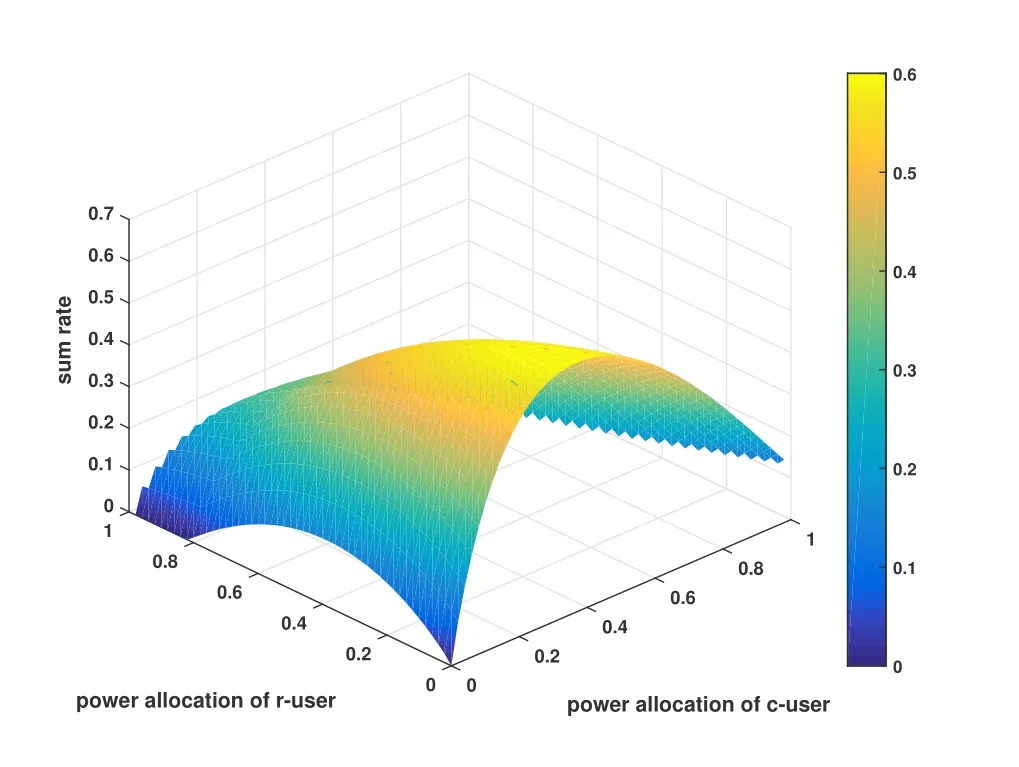
Figure 9. The secrecy rate of AN-aided scheme vs.power allocation with the distance of c-user,f-user and eavesdropper from BS is{7m,10m,12m}.
3.3 Reliability and Security
It has been proved that polar encoding can achieve the security by setting information in theAset for a single user[20],that is
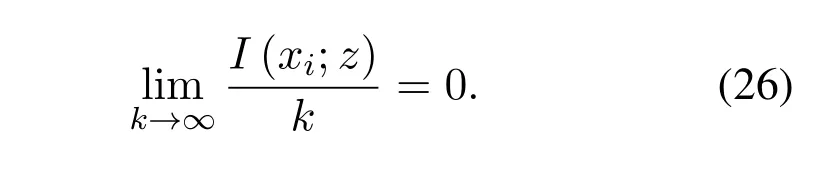
Then we have:
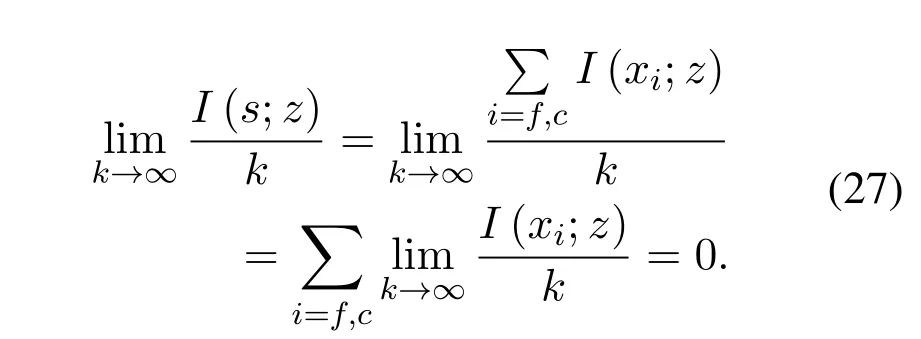
The security is proved.The transmission rate is
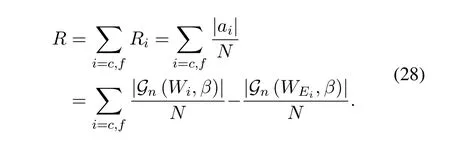
When the code length goes to infinity,
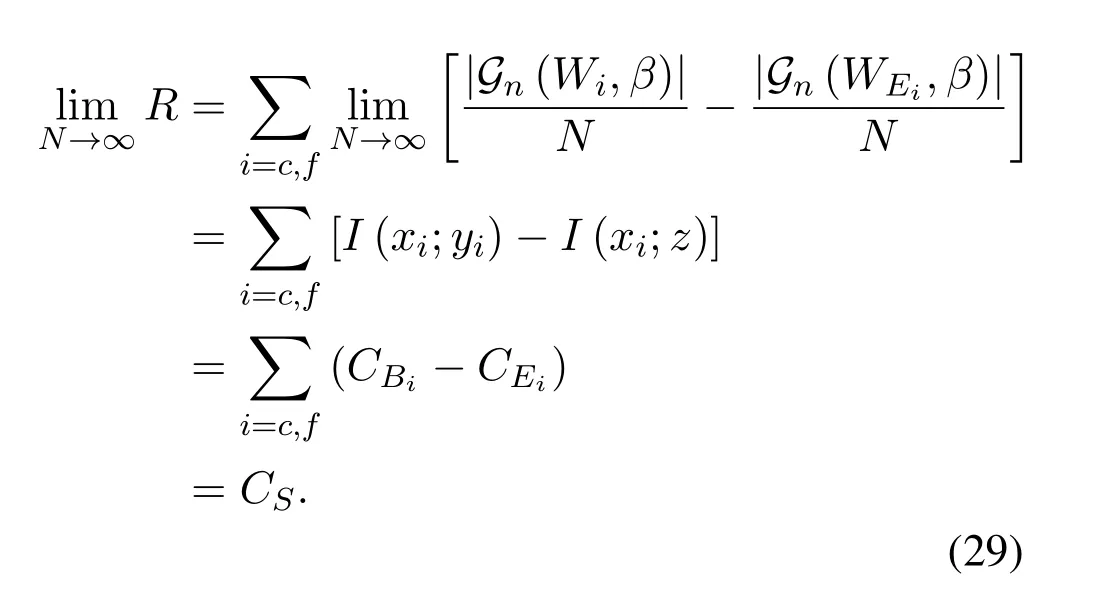
Eq.(29) implies that the our polar coding scheme can achieve the secrecy capacity.
The reliability is proved as follow
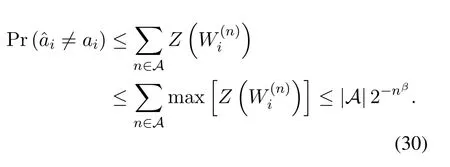
When code lengthNgoes to infinity,and the reliability condition is satisfied.
IV.POLAR CODES FOR NON-DEGRADED WIRETAP CHANNEL
In the section III,an ideal scenario that the wiretap channel is degraded with respect to the main channel is considered.However,this condition can not always be guaranteed in practical scenarios.In this section,a practical scenario that the wiretap channel is better than some mean channels is considered whereWfis degraded with respect to the.
As denoted in Eq.(18),because the the channel state of wiretap channel is better than that of the channel off-th user,The secure rate off-th user iswhich means that thefth user can not transmit any signal securely.In order to transmit thef-th user’s signal securely and reliably,MISO system is considered in this scenario and AN is generated at BS for confusing the wiretap channel.In this scenario,BS is equipped withNtantennas,while the users and Eve are equipped with only one antenna.BS superimposes the signal of users and AN together.The channel matrix of thec-th user,thef-th user and Eve is denoted asWithout loss of generality,we assume thatThe key ideal of AN-aided scheme is to set AN into the null-space of main channels,it will not impose any interference on users,however,AN can degrade the wiretap channel dramatically.The partial power of BS is allocated to AN to ensure the wiretapis degraded with respect to the main channelWf,then the polar encoding scheme can be used.The AN should meet the condition

where H =[hc,hf]and v is AN.The necessary and sufficient condition for the Eq.(31)to have a non-zero solution is rankTherefore we setNt >2 to make sure that there is null-space for two users of one pair.The singular value decomposition(SVD)of HTis
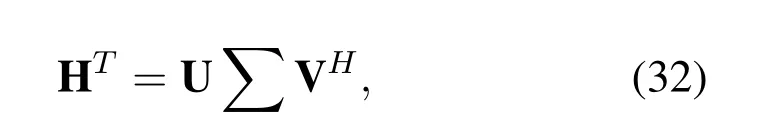
The AN is defined as

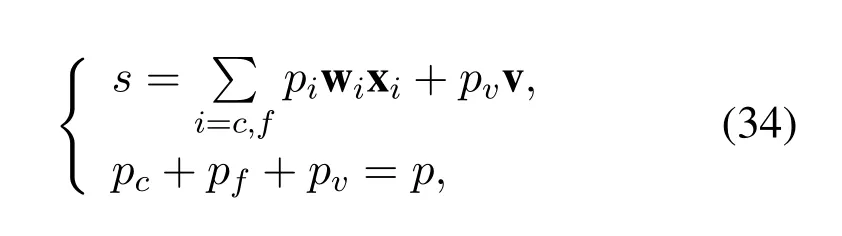
In the receiver,the received signal of users are
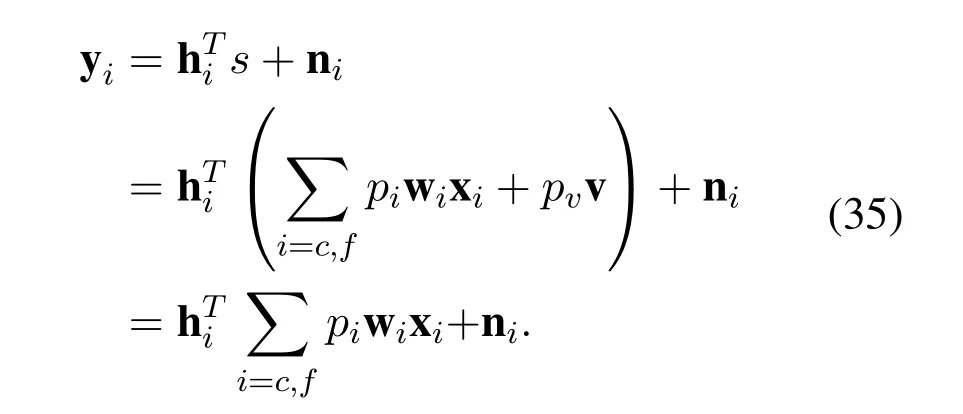
The SINRs for thef-th user and thec-th user are denoted as follow respectively:
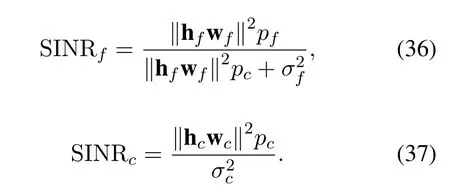
The received signal of Eve is
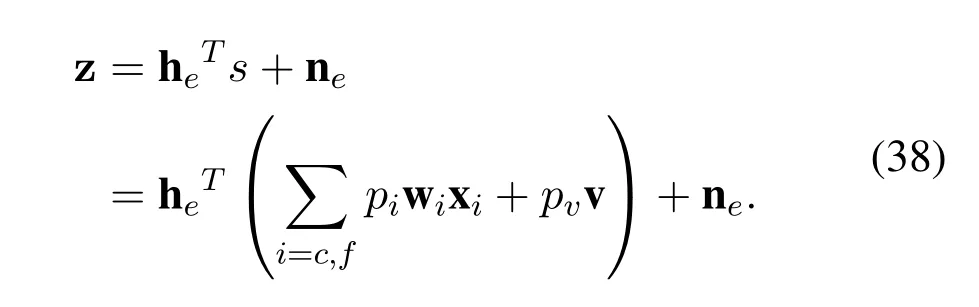
The SINR of detecting the signal of each users in one pair for the most detrimental Eve is:
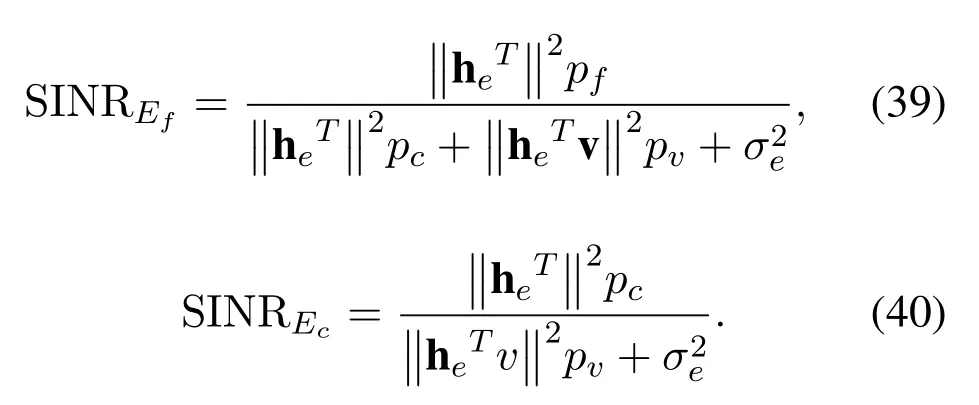
The capacity of the main channels and the wiretap channel have been shown as Eq.(22) and Eq.(23).In order to make sure that the users can transmit the signal at a certain rate,the threshold of the capacityCthrof the users should be set.For simplicity,we assume that the beamforming matrix is fixed and the parameters needed to be optimized are the power of users and AN.The more power is allocated for AN,the more obviously wiretap channel degrades.On the other hand,if too much power is allocated for AN,power allocated for users is inadequate,then the users can not meet the requirement of the capacity.The optimization problem can be formulated as:
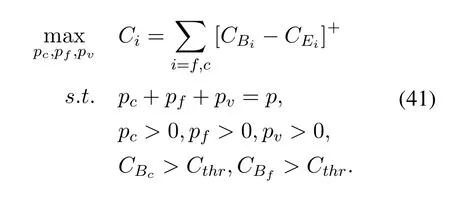
Because the optimization problem (41) is convex,it can be solved efficiently by interior point method[38].Figure 8 and Figure 9 show some cases of secrecy rate changing with the different distance from BS.The simulation results show that there exists an optimal power allocation that maximizes the secrecy capacity.
Withe the AN-aided scheme,the wiretap channel is degraded with respect to the both main channels,then the polar encoding scheme is the same as the previous section.
V.SIMULATION RESULTS
In this section,we give some simulation results to show the performance of our proposed coding schemes.The block error rate(BLER)is used to measure the performance of the proposed scheme.
5.1 Degraded Wiretap Channel Case
A path fading channel model is considered,that iswherediis the distance ofi-th user from BS,which means that the closer user is to BS,the better the channel state is.βis the fading factor that is set as 2.5 in this paper.Thedc,dfanddeis set as{5m,8m,20m}and{7m,12m,25m}respectively in this simulation.The code length is 128bits and the code rate is set as 1/2 and 1/4 respectively.The polar decoder uses SCL algorithm withList=8.
The simulation results are shown as Figure 10 and Figure 11.It can be observed that BLER of thecth user is about 2dBbetter thanf-th user because of the closer distance from BS(the better channel state).Compared with the legitimate users,BLER of Eve is 1 when that of legitimate users are less than 10-4,which means that eavesdropper can not obtain any information when legitimate users decode signal reliably.
5.2 Non-degraded Wiretap Channel Case
In this scenario,we compare BLER of legitimated users with BLER of eavesdropper for ANaided scheme and without-AN-aided scheme respectively.Thedc,dfanddeis set as{5m,8m,7m}and{7m,12m,10m}respectively in this simulation.Through the distance from BS,We can see that the wiretap channel is non-degraded with respect to the channel off-user.
The simulation results are shown as Figure 12 and Figure 13.It can be seen that Eve can decode the information of users correctly without AN-aided scheme,even BLER for decoding information off-user is better than the legitimate user.Though BLER for decoding information ofc-user is worse than legitimate user,the information can not be transmitted securely.However,with AN-aided scheme,BLER of eavesdropper is 1 which means that Eve can not obtain any information when legitimate users decode signal reliably.
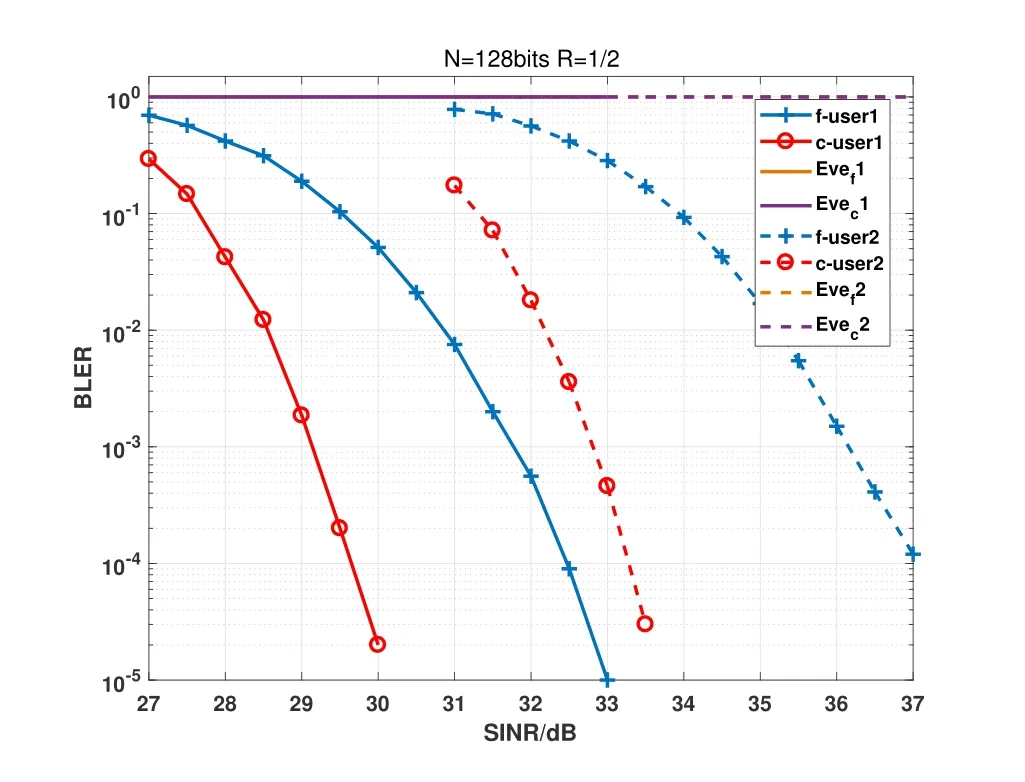
Figure 10.BLER of different users for the degraded wiretap channel case with code length is 128bits and code rate is 0.5.
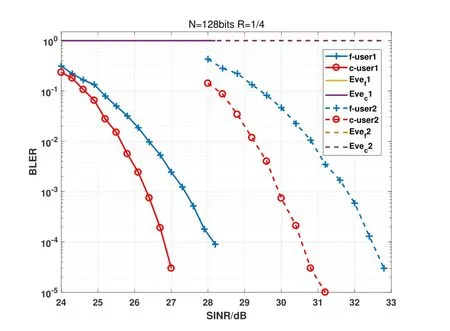
Figure 11.BLER of different users for the degraded wiretap channel case with code length is 128bits and code rate is 0.25.
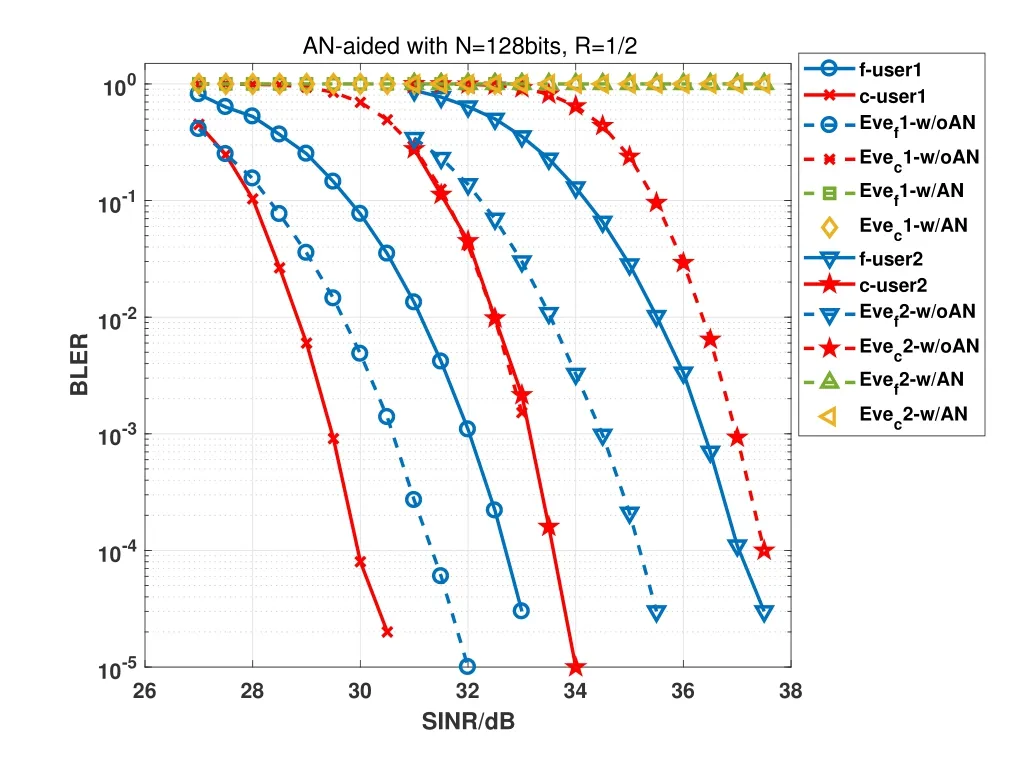
Figure 12. BLER of different users for the non-degraded wiretap channel case with code length is 128bits and code rate is 0.5.
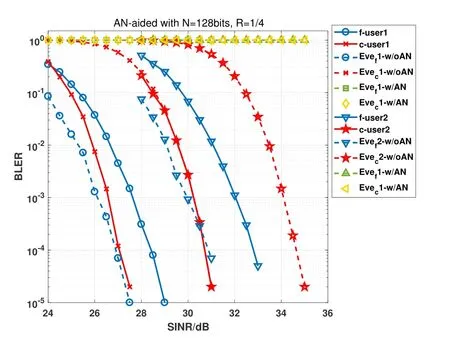
Figure 13. BLER of different users for the non-degraded wiretap channel case with code length is 128bits and code rate is 0.25.
VI.CONCLUSION
In this paper,a secure transmission combined polar codes and NOMA has been proposed,where both scenarios for degraded wiretap channel and non-regraded wiretap channel are taken into account.Firstly,a secure polar encoding scheme is proposed when the channel state of eavesdropper is degraded with respect to both legitimate channels in NOMA system.In this case,a polar coding scheme is designed to achieve reliability and security.Then based on the first scheme,the case that the channel state of eavesdropper is not degraded with respect to both legitimate channels in NOMA system is considered,in which a polar encoding scheme with MISO system is proposed.Furthermore,artificial noise is generated at BS to degrade the wiretap channel via transmit beamforming.The simulation results show that the eavesdropper hardly decoding the secure signal when the legitimate receivers can decode the signal with very low BLER.
ACKNOWLEDGMENT
This work was supported in part by Science Foundation of China under Grant No.61871032 and in part by the Chinese Ministry of Education-China Mobile Communication Corporation Research Fund under Grant MCM20170101.The work of Bin Li was supported by the Natural Science Foundation of Jiangsu Higher Education Institutions of China under Grant 20KJB510036,and by the Guangxi Key Laboratory of Multimedia Communications and Network Technology under Grant KLF-2020-03.
- China Communications的其它文章
- Correlation-Aware Replica Prefetching Strategy to Decrease Access Latency in Edge Cloud
- M2LC-Net:A Multi-Modal Multi-Disease Long-Tailed Classification Network for Real Clinical Scenes
- DEEPNOISE:Learning Sensor and Process Noise to Detect Data Integrity Attacks in CPS
- Beamforming Optimization for RIS-Aided SWIPT in Cell-Free MIMO Networks
- Security Risk Prevention and Control Deployment for 5G Private Industrial Networks
- Cost-Minimized Virtual Elastic Optical Network Provisioning with Guaranteed QoS

